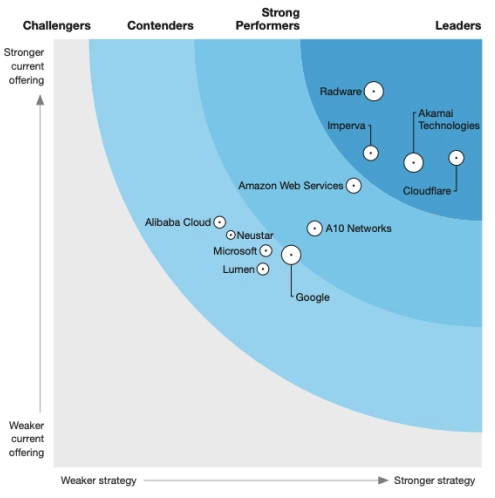
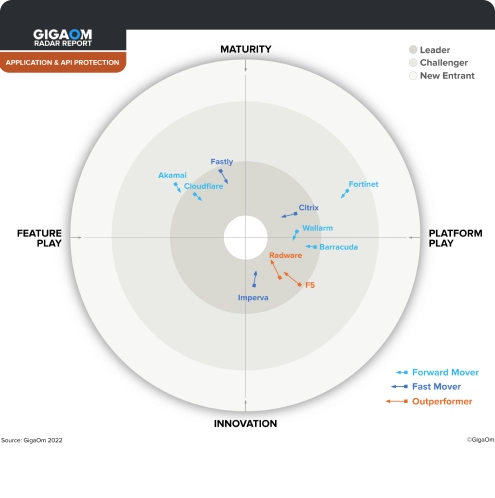
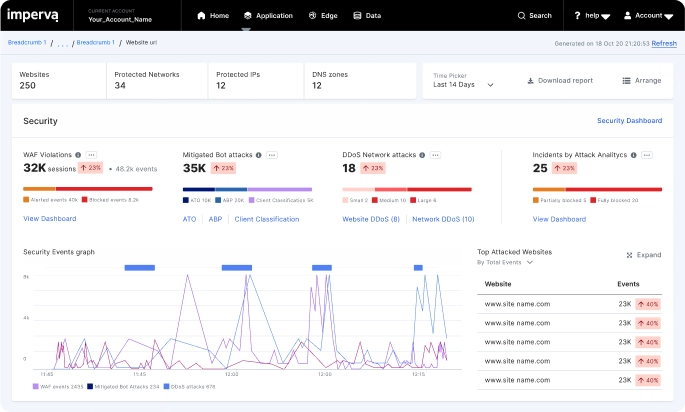
Imperva named a leader in the 2024 IDC MarketScape for WAAP Strengthen your defenses against cyber threats
Read nowImperva latest news
Luke Babarinde discusses modern application security challenges with TechStrong TV
Watch now
Imperva named an overall leader in the KuppingerCole Leadership Compass 2024 for WAF
Read more
Keep Operations Running Smoothly During the Holiday Shopping Surge
Read the blog post
The Economic Impact of API and Bot Attacks
Read the reportEnterprises move to Imperva for
world class security

Multi-layered security
Consolidate security point products for detection, investigation, and management under one platform.
Fast response
Quickly neutralize threats to deliver a seamless user experience even under attack.

PCI DSS 4.0 compliance
Demonstrate continuous compliance to simplify the audit process.
Imperva products are quite exceptional