What is Web Application and API Protection (WAAP)?
Web applications are programs that users can access via a web browser, and are a critical component of many organizations’ web presence. A web application may also include application programming interfaces (APIs), which provide programmatic access to the application’s capabilities.
Adam Hils and Jeremy D’Hoinne of Gartner coined the name Web Application and API Protection (WAAP) in reference to cloud-based services created to safeguard vulnerable APIs and web applications.
Cloud WAAP services provide various security modules, based on an auto-scaling, multitenant cloud infrastructure. The core features of Cloud WAAP are bot mitigation, WAF, API protection, and protection against DDoS. A varying depth of security is possible for every module. Cloud WAAP services are often provided with additional service components that can improve web application performance.
Why Is WAAP Important?
Web applications and APIs are accessible via the public Internet and provide access to sensitive data, making them a main target for attackers. Traditional security solutions cannot effectively protect these applications, making WAAP a must.
Here are a few reasons traditional solutions cannot protect web applications effectively:
- Signature-based attack detection is ineffective—threats against web applications continually change. Trying to safeguard against them using signature-based detection solutions is an unscalable strategy. WAAP solutions offer continuous self-learning, which helps organizations keep ahead of a developing application security threat environment.
- Port-based blocking won’t work—traditional firewalls filter traffic according to the protocols and ports in use. However, attacks against web applications and web APIs make use of the same web ports and protocols as users—such as HTTP(S)—making it infeasible to only filter out malicious traffic using this method. A more detailed level of inspection is needed to distinguish potential attacks from legitimate traffic.
- HTTP traffic can be involved—web applications can be involved, and cybercriminals use this complexity to conceal malicious content. The level of security inspection offered by a conventional intrusion detection and prevention system (IDS/IPS) is inadequate for isolating and protecting against threats to web applications.
- Encrypted traffic inspection is necessary—more than half of all web traffic today uses TLS encryption, which is advantageous for privacy but makes it more difficult to detect malware and other malicious content. WAAP solutions can inspect TLS connections, allowing them to identify sensitive data and malicious content hiding in encrypted traffic.
Why Traditional WAFs Are No Longer Enough
Gartner analysts estimate that WAF physical appliance sales are decreasing, as most vendors are experiencing a low-single-digit growth or a decline. There are some expectations, where WAF vendors are working to improve their cloud WAF services by offering to meet WAAP requirements.
The decline of WAF appliances is mainly due to the evolution of enterprise web applications:
- Modern applications frequently change—the adoption of agile and DevOps practices means that modern web applications and APIs are in a continuous state of flux. Web application firewalls (WAFs), which demand manual tuning and creation of custom rules, are not well adapted to rapidly changing applications.
- Cloud hosting has become a popular architecture—this is leading solution providers to offer cloud-native application security solutions. It also provides greater benefits, including minimizing potential bottlenecks or latency, particularly when the web applications cater to customers from multiple areas.
- The positive security model is lacking—WAF technology has not delivered on its assurance to automatically produce allow lists for URLs and parameters founded on automatic learning of application traffic. In reality, they require heavy manual configuration and tuning.
- WAF has seen minimal innovation recently—the fast growth of web standards (HTTP 2.0, increased use of JSON payload) monopolized vendor development plans, leaving little room for the development of new security features.
- Multi-cloud strategy—each cloud provider offers different features and uses a different architecture. Organizations operating across multiple clouds need to build an intricate cross-provider capabilities matrix to achieve effective security controls. Cloud-agent-based runtime protection and WAAP services are more suited to a multi-cloud environment.
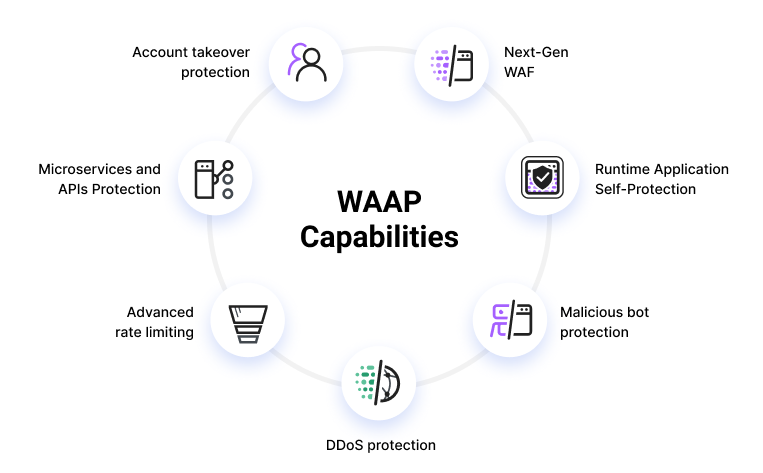
Web Application and API Protection Service: Key Capabilities
Complete Web Application and API Protection services safeguard your web applications and APIs against a broad spectrum of attacks. A WAAP service must effectively inspect requests before they reach the API endpoint or application.
The core capabilities of a broad WAAP service include:
- Next-Generation Web Application Firewall (Next-Gen WAF)—protects and monitors web applications from a broad spectrum of attacks at the point where they are deployed—the application layer. A next-gen WAF differs from a traditional WAF in that it uses behavioral analysis and artificial intelligence (AI) to block attacks without relying solely on known attack patterns and manual security rules.
- Runtime Application Self-Protection (RASP)—embedded in the application runtime domain, this offers real-time attack defense for APIs and web applications.
- Malicious bot protection—isolates and stops attacks from suspicious bots while permitting safe bot traffic to reach the application.
- Distributed Denial-of-Service (DDoS) Protection—safeguards against DDoS attacks targeted at applications, APIs and microservices, at the application and network layers. Able to scale up to defend against massive-scale attacks.
- Advanced rate limiting—safeguards against abusive activity at the application level which adversely influences website and API performance.
- Protection for microservices and APIs—places security within the microservice, application, or serverless function to produce a context and data-aware micro perimeter around all individual services.
- Account takeover protection—safeguards against cybercriminals using compromised credentials from data dumps and password lists. Detects unauthorized access to customer accounts via authentication APIs or an application’s customer-facing authentication process.
Considerations for Evaluating a Cloud WAAP Service
Here are a few ways you can evaluate if a WAAP solution is right for your organization.
Regulatory and Cultural Constraints
More than efficient regulatory constraints, fear of legal issues could elicit organizational pushback. This could prevent the adoption of cloud-based security services, including cloud WAAP services.
Some of the key challenges include:
- Allowing a third-party cloud solution to decrypt TLS connections, deal with application secret keys, and log sensitive client data, which can be subject to data residency conditions.
- Adapting budgets to the provider’s SLAs and pricing model.
- Integrating the cloud WAAP solution in the current incident response workflow, which tends to be founded on a security information and event management (SIEM) tool.
Solution Maturity
Many Cloud WAAP services are missing some WAF appliance characteristics— URL and form protection, cookie signing, and cross-site request forgery (CSRF) tokens. This slows uptake in organizations already using this method and searching for a lift-and-shift approach to their cloud application security strategy.
Technical Architecture
WAAP services that are built from scratch, and not based on established WAF solutions, tend to miss out on integration with the enterprise ecosystem, including application security testing (AST) and SIEM. They may also provide limited log retention and configuration options. Cloud WAAP service monitoring consoles may not offer real-time entry to logs.
Imperva Web Application and API Protection Platform
Imperva pioneered the WAAP market, providing a mature, full-featured Web Application and API Protection platform. Imperva WAAP is based on its industry-leading next-generation WAF, used by thousands of organizations in the cloud and also on-premises. The solution is based on three pillars: application security, data security, and application delivery.
Application Security
Imperva’s WAAP provides comprehensive protection for applications, APIs, and microservices:
Web Application Firewall – Prevent attacks with world-class analysis of web traffic to your applications.
Runtime Application Self-Protection (RASP) – Real-time attack detection and prevention from your application runtime environment goes wherever your applications go. Stop external attacks and injections and reduce your vulnerability backlog.
API Security – Automated API protection ensures your API endpoints are protected as they are published, shielding your applications from exploitation.
Advanced Bot Protection – Prevent business logic attacks from all access points – websites, mobile apps and APIs. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping.
DDoS Protection – Block attack traffic at the edge to ensure business continuity with guaranteed uptime and no performance impact. Secure your on premises or cloud-based assets – whether you’re hosted in AWS, Microsoft Azure, or Google Public Cloud.
Attack Analytics – Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns.
Client-Side Protection – Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks.
Data Security
Imperva protects all cloud-based data stores to ensure compliance and preserve the agility and cost benefits you get from your cloud investments:
Cloud Data Security – Simplify securing your cloud databases to catch up and keep up with DevOps. Imperva’s solution enables cloud-managed services users to rapidly gain visibility and control of cloud data.
Database Security – Imperva delivers analytics, protection, and response across your data assets, on-premise and in the cloud – giving you the risk visibility to prevent data breaches and avoid compliance incidents. Integrate with any database to gain instant visibility, implement universal policies, and speed time to value.
Data Risk Analysis – Automate the detection of non-compliant, risky, or malicious data access behavior across all of your databases enterprise-wide to accelerate remediation.
Application Delivery
The Imperva secure Content Delivery Network (CDN) delivers content caching, load balancing, and failover built natively into a comprehensive Web Application and API Protection (WAAP) platform, so your applications are securely delivered across the globe:
Imperva Load Balancing – enables you to gain even greater operational efficiency for your application delivery stream.
Local Server Load Balancer – Imperva’s content delivery network delivers dedicated load balancing for your website or application, ensuring traffic is distributed across multiple servers within your data center according to a user-defined distribution policy.
Global Server Load Balancer – The global secure CDN serves as a gateway for all incoming application-layer traffic, which is then balanced among multiple data centers to ensure optimal performance. Rerouting occurs on the CDN level and is free of TTL (Time to Live)-induced delays.
Automatic Site Failover – In disaster recovery scenarios, Imperva performs server health checks to accurately pinpoint a failover. A backup site automatically kicks in and the failover solution instantly reroutes traffic without any TTL (Time to Live)-related delays.