The Industrialization of Hacking: How to Stop Automated Attacks
Get Your Infographic
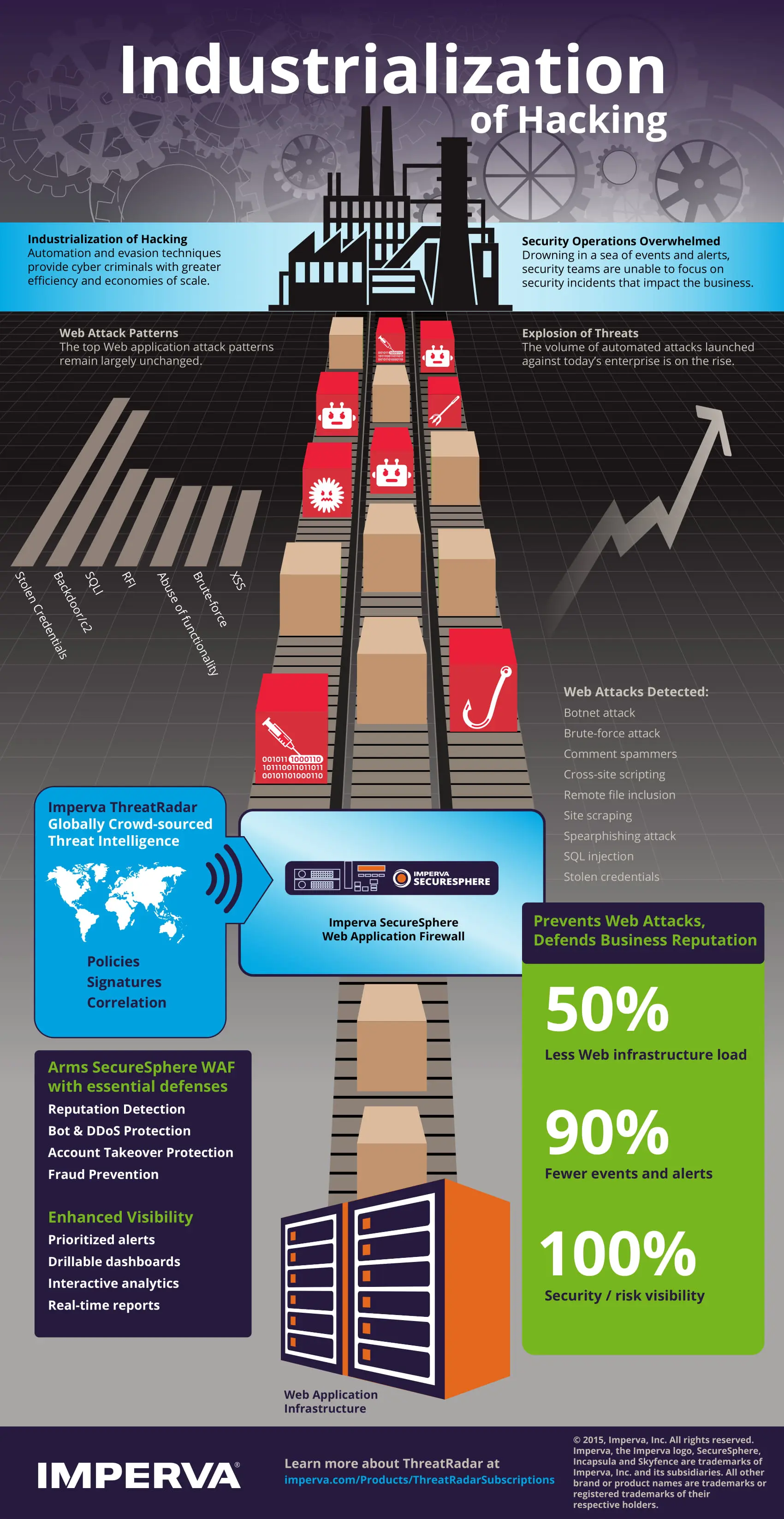
The industrialization of hacking has created a more effective and efficient way for hackers to profit from attacks on business critical applications and assets exposed to the Internet. This era of automated attacks that exploit application vulnerabilities and abuse application functionality has profoundly changed how we must protect these assets. A continuous threat intelligence feed, from a trusted globally crowd-sourced platform, has become vital to defend against such advanced Web-based attacks.




