Static data masking done right
Mage iScramble protects sensitive data in non-production environments while integrating seamlessly with Imperva Data Security Fabric (DSF). With over 60 data anonymization algorithms that include masking, encryption, and tokenization, Mage iScramble allows organizations to deploy the most suitable method for anonymization without compromising their sensitive data.
With data being used extensively for analytics and other value-added purposes, it has become increasingly important for organizations to balance security and usability. Anonymizing a name with many random characters and symbols will protect the data but will render the anonymized data useless for analytics. Mage iScramble anonymizes data to retain the data usability while providing actual security. The solution even lets users know the reversibility risk associated with a particular value so that security experts can make an informed decision on what needs to be prioritized – data security or data usability – allowing them to coexist in balance.
Key features and benefits
- Choose from 60+ different anonymization methods to protect your sensitive data effectively
- Maintain referential integrity between applications through anonymization methods that give you consistent results across applications and datastores
- Choose to encrypt, tokenize, or mask the data according to the use case that suits you
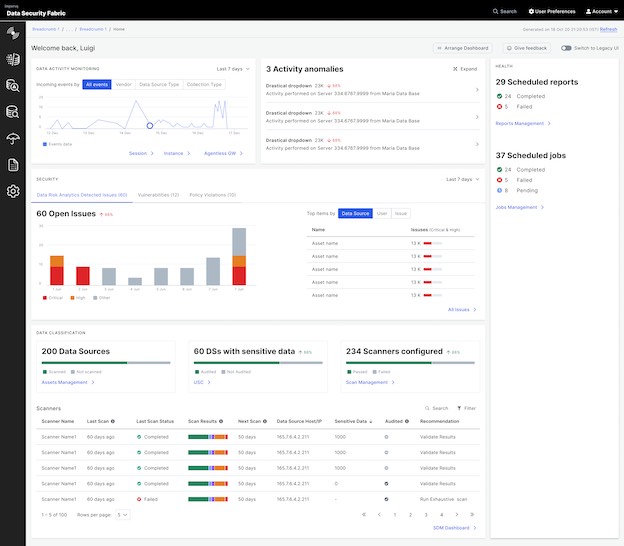
Imperva Data Security Fabric protects all data types with a single system that delivers multiple business capabilities
Imperva Data Security Fabric is the first data-centric solution that enables your organization's security and compliance teams to quickly and easily secure sensitive data, no matter where it resides, with an integrated, proactive approach to visibility and predictive analytics.
Imperva Data Security Fabric is composed of cutting-edge orchestrated technical capabilities that work in unison to protect your data across your entire organization:
Data Risk Prioritization
Get a unified view of essential data risk metrics that are transparent, flexible, and customizable to understand your risk profile and mitigate gaps.
Learn moreData Discovery & Classification
Discover ungoverned data, classify all data, and assess vulnerabilities.
Learn moreData Activity Monitoring
Gain complete visibility and ensure compliance with continuous monitoring, auditing and analyzing all data store and data types.
Learn moreData Risk Analytics
Detect and report non-compliant, risky, or malicious data access behavior across all of your data repositories enterprise-wide to accelerate remediation.
Learn moreData Retention & Archive
Meet any data archiving requirement using the most cost efficient storage technology available.
Learn moreEcosystem Integrations
Enhance the value of your existing technology investments - for both incident context and additional data capabilities.
Learn moreData Encryption & Tokenization
Protect critical data with encryption, key management, and tokenization wherever it resides.
Learn moreStatic Data Masking
Modify sensitive data so it is of no value to unauthorized users while still being usable by your systems.
Learn moreAutomated Workflows & Playbooks
Achieve higher scale and increase DevOps efficiency through the use of automated workflows delivered through trusted repositories.
Learn more