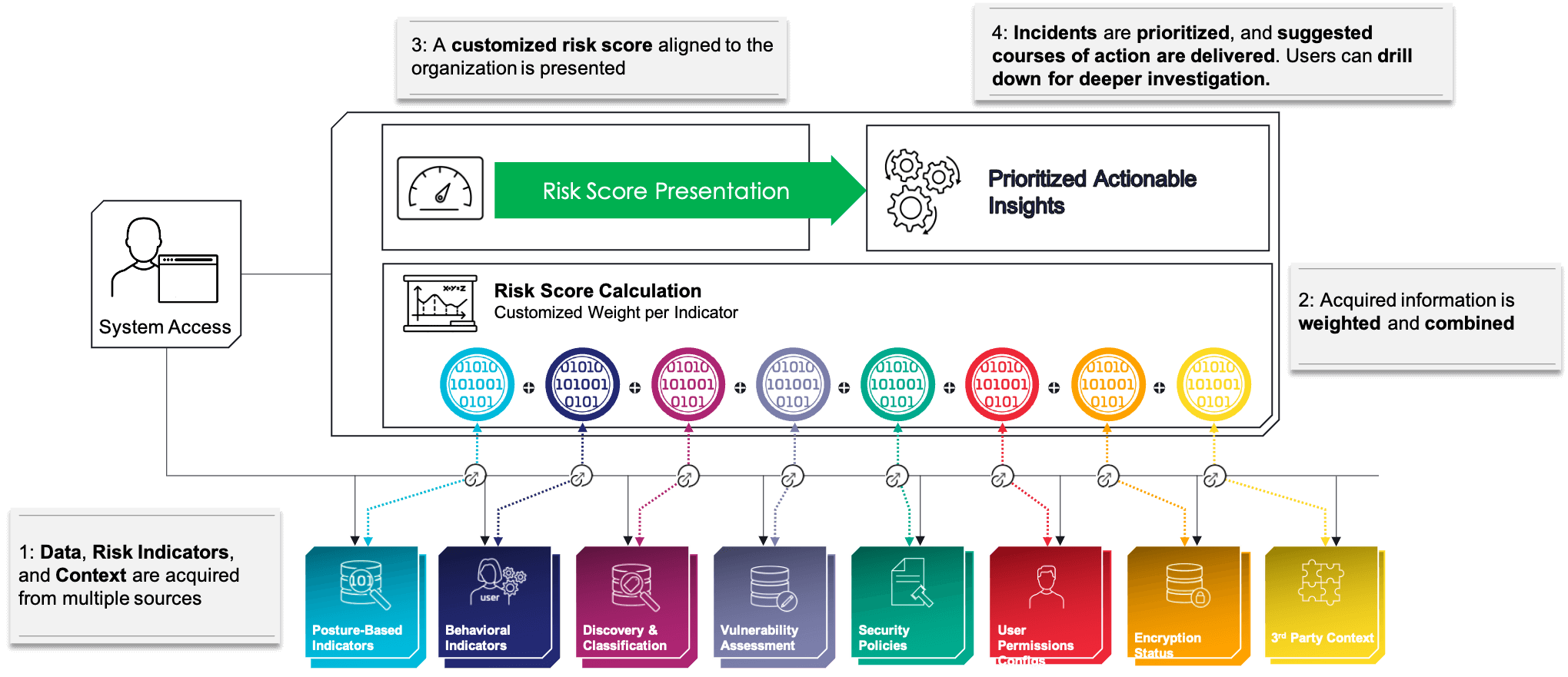
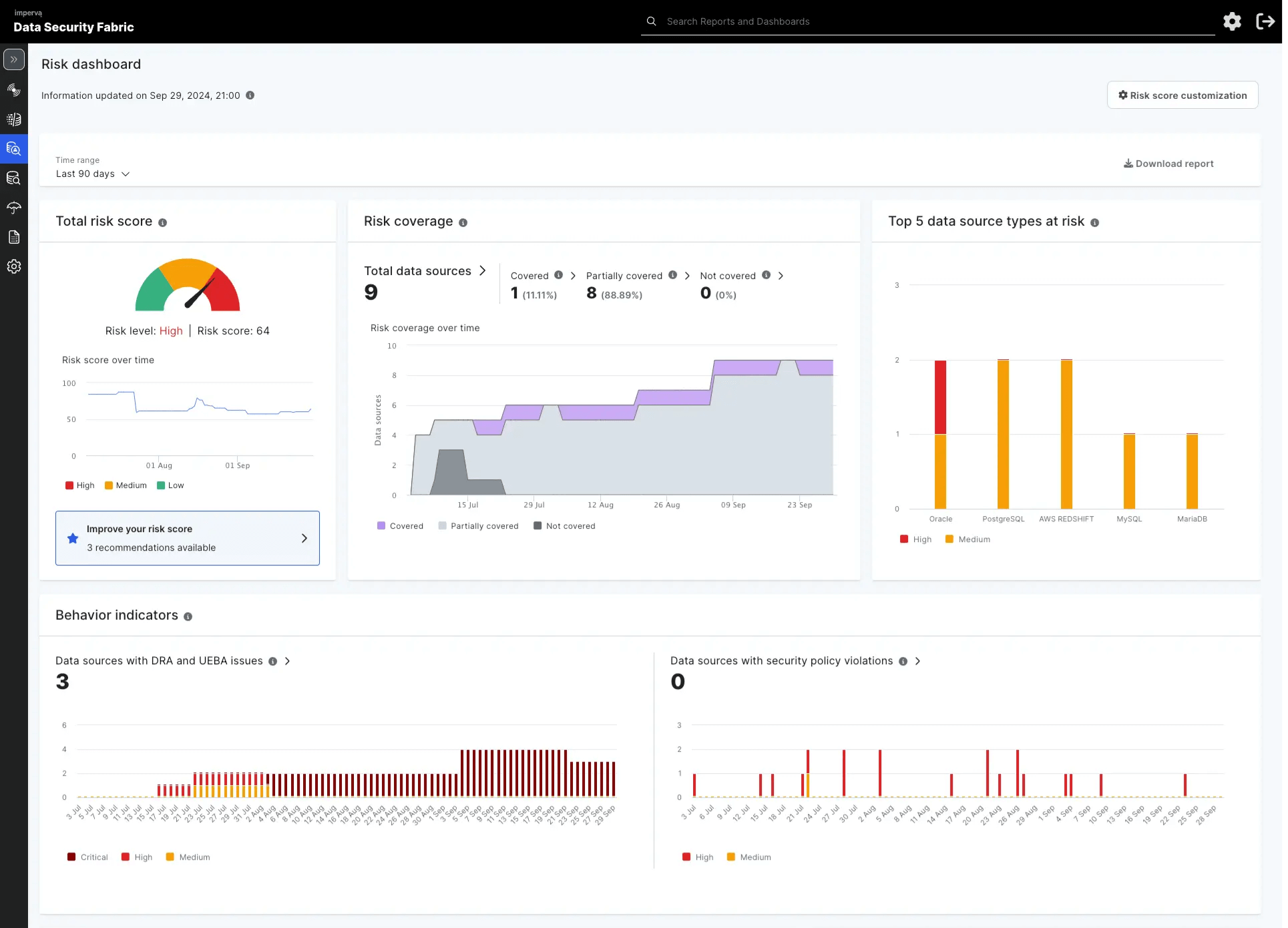
Know where to focus your efforts
Ease the day-to-day activities with precise, prioritized, and actionable insights.
CIOs, CISOs, and Data Risk Experts must identify the most significant data risks by severity and likelihood to prioritize mitigation and effectively align resources.
DSF Data Risk Intelligence works across your data security systems to deliver specialized insights from a wide-ranging set of data risk indicators through advanced analytics. These indicators encompass user permissions, data source vulnerabilities, encryption status, suspicious activities, and an all-encompassing organizational risk factor. DSF Data Risk Intelligence furnishes clear-cut recommendations for necessary action following this thorough analysis.
DSF Data Risk Intelligence provides a unified view of essential data risk metrics that are transparent, flexible, and customizable. This ensures a thorough understanding of your risk profile and identifies critical areas where resources should be allocated to optimize efficiency and effectiveness.
Imperva delivers end-to-end protection and compliance for critical healthcare data and applications.
Imperva protects banks, insurance companies, payments providers, and financial exchanges with data security for on-premises, cloud, or hybrid data stores.
Defense-in-depth security for government organizations and agencies. Imperva helps authorities prevent cyber attacks, identify insider threats, and achieve data compliance.
Imperva Data Security Fabric is the first data-centric solution that enables your organization's security and compliance teams to quickly and easily secure sensitive data, no matter where it resides, with an integrated, proactive approach to visibility and predictive analytics.
Imperva Data Security Fabric is composed of cutting-edge orchestrated technical capabilities that work in unison to protect your data across your entire organization:
Get a unified view of essential data risk metrics that are transparent, flexible, and customizable to understand your risk profile and mitigate gaps.
Learn moreDiscover ungoverned data, classify all data, and assess vulnerabilities.
Learn moreGain complete visibility and ensure compliance with continuous monitoring, auditing and analyzing all data store and data types.
Learn moreDetect and report non-compliant, risky, or malicious data access behavior across all of your data repositories enterprise-wide to accelerate remediation.
Learn moreMeet any data archiving requirement using the most cost efficient storage technology available.
Learn moreEnhance the value of your existing technology investments - for both incident context and additional data capabilities.
Learn moreProtect critical data with encryption, key management, and tokenization wherever it resides.
Learn moreModify sensitive data so it is of no value to unauthorized users while still being usable by your systems.
Learn moreAchieve higher scale and increase DevOps efficiency through the use of automated workflows delivered through trusted repositories.
Learn more