Lack of guidelines
Unaware of my unknowns. What rules should the security team establish?
Organizations need advanced data risk analytics to eliminate the noise and help security staff gain actionable threat insights to accelerate risk mitigation and breach detection
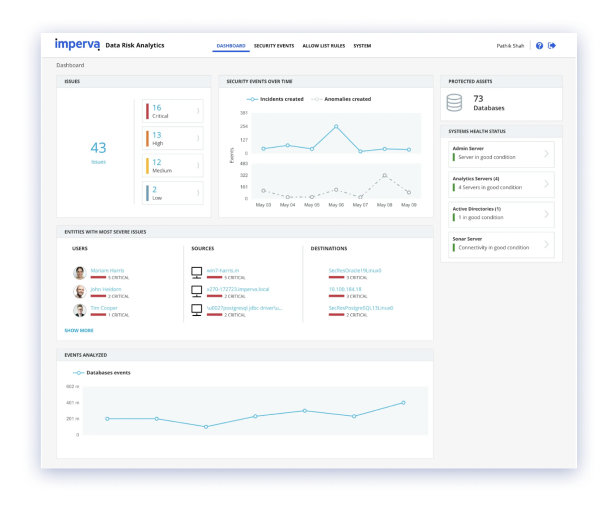
Imperva Data Risk Analytics (DRA) identifies abnormal user behavior that can lead to bad practices, hostile intrusions, and data compromise. Imperva DRA translates complex technical events into plain language that IT operations teams and security staff members can immediately understand. Imperva DRA provides an intuitive dashboard that provides a prioritized incident summary of questionable events that anyone can click through, which in turn provides a complete description of the threat with actionable intelligence for remediation.
Imperva Data Risk Analytics (DRA) prioritizes critical incidents by applying grouping and scoring algorithms that factor in variables such as sensitive data type, privileged account, amount of data involved, and more. Suppose multiple incidents are related (e.g., all associated with the same user account, or multiple users are abusing the same service account). In that case, Imperva DRA groups the incidents into one issue, prominently showing security staff the high-risk incident and suppressing false positive noise.
In today's world, CIOs and CISOs face a harsh reality regarding the security staff shortage. With the deflating economy, nationalism, cybercrime, and nation-led adversaries, the demand for security personnel has increased, making it challenging for organizations to find and retain skilled security staff.
Customers are also looking for solutions to offload tasks from their security staff, and this is where Imperva DSF Data Risk Analytics (DRA) comes in. With Imperva DSF DRA, most cases related to bad practices and insider threats can be handled and resolved by other non-security teams in the organization. Imperva DSF DRA, when integrated with ServiceNow, can automatically triage data risk incidents to different members or groups like data experts, access experts, direct managers, and database owners who can receive and resolve incidents directly and immediately without expensive human intervention, freeing security specialists to work on high stake data risk issues.
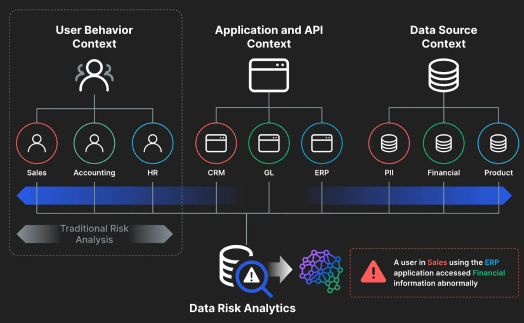
Imperva Data Risk Analytics (DRA) protects enterprise data stored in enterprise databases and file shares from theft and loss caused by compromised, careless or malicious users. By dynamically learning users' standard data access patterns and then identifying inappropriate or abusive access activity, DRA proactively alerts IT teams to dangerous behavior.
Imperva Data Risk Analytics (DRA) protects various user-related security threats via statistical models created and configured directly in Imperva Data Security Fabric (DSF). Imperva DRA User Entity and Behavior Analytics (UEBA) models in the platform detect and flag outlier activity within large datasets and generate automatic alerts as needed.
Preconfigured DRA UEBA models
These detection models can be used to understand how to build automated logic that analyzes audit data from all sources across your data estate. It is possible to clone and customize these pre-configured models to detect user-related security events tailored to your organization. Each preconfigured DRA model represents a different threat vector.
Imperva Data Security Fabric is the first data-centric solution that enables your organization's security and compliance teams to quickly and easily secure sensitive data, no matter where it resides, with an integrated, proactive approach to visibility and predictive analytics.
Imperva Data Security Fabric is composed of cutting-edge orchestrated technical capabilities that work in unison to protect your data across your entire organization:
Get a unified view of essential data risk metrics that are transparent, flexible, and customizable to understand your risk profile and mitigate gaps.
Learn moreDiscover ungoverned data, classify all data, and assess vulnerabilities.
Learn moreGain complete visibility and ensure compliance with continuous monitoring, auditing and analyzing all data store and data types.
Learn moreDetect and report non-compliant, risky, or malicious data access behavior across all of your data repositories enterprise-wide to accelerate remediation.
Learn moreMeet any data archiving requirement using the most cost efficient storage technology available.
Learn moreEnhance the value of your existing technology investments - for both incident context and additional data capabilities.
Learn moreProtect critical data with encryption, key management, and tokenization wherever it resides.
Learn moreModify sensitive data so it is of no value to unauthorized users while still being usable by your systems.
Learn moreAchieve higher scale and increase DevOps efficiency through the use of automated workflows delivered through trusted repositories.
Learn more