Low Orbit Ion Cannon (LOIC) is a popular open-source network stress testing and denial-of-service (DoS) attack tool. Attackers can use LOIC to flood networks and websites with traffic, often as part of coordinated Distributed Denial of Service (DDoS) attacks.
What is LOIC?
LOIC performs a DoS attack by flooding the target with TCP, UDP, or HTTP requests. This can overwhelm the server’s resources like CPU, memory, and bandwidth – resulting in slow response or unavailability for legitimate users.
Here are some key features of LOIC:
- Open-source tool available for Windows and Linux
- Allows users to control rate and duration of attack
- Supports UDP, TCP, and HTTP flooding attacks
- Optional encryption via ZOMBIE messages
- Built-in support for orchestrating attacks via IRC channels
- User-friendly GUI and command-line interfaces
Attackers commonly use LOIC to carry out DoS attacks against websites, applications, and networks. The tool is popular among hackers as well as activist groups like Anonymous who have coordinated LOIC attacks for political reasons.
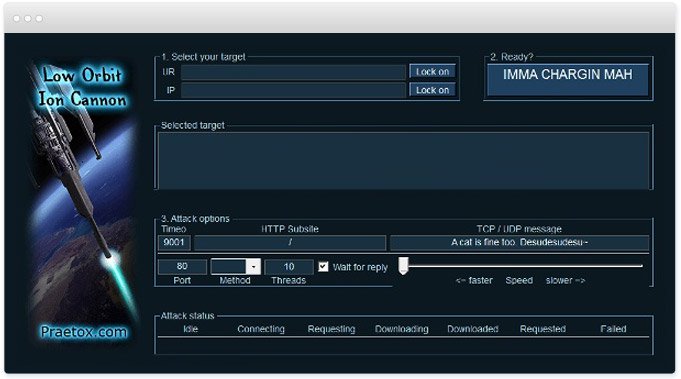
The LOIC application interface.
How Does LOIC Work?
LOIC works by sending a high volume of TCP, UDP, or HTTP requests to the target server. The exact working mechanism depends on the protocol used:
TCP Flood
A TCP flood attack establishes multiple half-open connections that consume resources on the target server waiting to complete the handshake. This can overwhelm networks and load balancers.
UDP Flood
In a UDP flood, LOIC sends a stream of UDP packets to random destination ports on the target. This can saturate the network capacity.
HTTP Flood
An HTTP flood sends continual HTTP GET or POST requests to specific URLs on the target website. This can consume web server resources or bandwidth.
In all cases, the goal is to overload capacity and prevent the server from responding to legitimate requests. LOIC also has a “Zombie mode” which allows anonymizing attacks using a layer of indirect LOIC instances.
Uses of LOIC
Some common uses of the LOIC tool include:
- Stress testing websites and applications to uncover weaknesses
- Carrying out DoS attacks for ideological, political or criminal reasons
- Participating in voluntary botnets to attack targets selected by organizers
- Causing financial damage and loss of reputation to organizations
- Disrupting operations and denying access to critical infrastructure
- Censorship resistance by taking down government websites
- Extortion by threatening DDoS attacks unless ransom is paid
While LOIC can be used for legitimate stress testing, most uses are malicious. Unintentional damages can also result from misuse by inexperienced users.
LOIC Attack Stages
A typical LOIC attack proceeds through several stages:
Target Selection
The attacker selects a website, server or network to disrupt. Common targets are business sites, critical infrastructure, and government networks.
Weaponization
LOIC is downloaded and configured for the attack. Settings are tuned, including: attack duration, rate limits, and spoofing parameters.
Attack Launch
The attacker launches the LOIC tool against the target. For larger attacks, multiple LOIC instances and botnets are coordinated.
Attack Impact
The target experiences denial of service, unavailability of resources and services for end users. Financial, operational and reputational damages can occur.
Attack Stop
The attack is stopped by stopping the LOIC tool. Backup servers may be deployed to restore services. Forensics are done to trace the attack sources.
Notable LOIC Attack Instances and Events
LOIC has been used in many high-profile cyberattacks, including:
- Krebs on Security DDoS (2016) – Prominent industry news site was targeted with a record 620Gbps DDoS powered, in part, by LOIC reflections.
- OpIsrael (2013) – Attacks coordinated by Anonymous to protest Israel’s Gaza policies, targeting finance and government sites.
- Operation Megaupload (2012) – Anonymous launched LOIC attacks against DOJ, RIAA, MPAA, and others after the shutdown of file hosting site Megaupload.
- Occupy Nigeria (2012) – Activists used LOIC to attack Nigerian government sites and banks to protest fuel subsidy removal.
- Scientology websites in protest of the Church.
- Operation Payback (2010) – Anonymous used LOIC to launch DDoS attacks against organizations opposing WikiLeaks like Mastercard, Visa, and PayPal. This brought LOIC into prominence.
- Project Chanology (2008) – Early Anonymous operation that used LOIC to attack.
- Habbo Hotel Raids (2006) – 4chan users flooded the Habbo Hotel site with bots using early LOIC variants to block users and depict swastika formations.
- World of Warcraft Funeral Raid (2006) – Habbo raiders also disrupted a World of Warcraft online funeral using LOIC attacks.
LOIC’s adoption by Anonymous hacktivists marked a shift toward political activism uses of the tool. However, LOIC also enabled recreational and criminal attacks over time.
LOIC Detection
LOIC attacks can be detected using traffic monitoring and analysis:
- Bandwidth spikes – Sudden surge in traffic beyond normal levels indicates a possible flood attack.
- Protocol anomalies – Unusual TCP and UDP traffic patterns like anomalous ports or malformed packets may signal LOIC.
- Request heuristics – In HTTP floods, common request patterns and repetitive URLs point to LOIC.
- IP reputation – Sources involved in past malicious LOIC activity can be identified via threat feeds.
- Behavioral analysis – Machine learning models can identify traffic indicative of DoS flooding.
Timely detection allows mitigating the effects before significant damage occurs.
Mitigating LOIC DDoS Attacks
Here are some ways to defend against LOIC DDoS:
- Blackhole traffic – Drop traffic from known malicious IP addresses at the edge network.
- Rate limiting – Limit TCP, UDP, and HTTP requests from individual sources.
- Increase capacity – Scale up network bandwidth and server resources to handle larger volumes.
- Load balancers – Distribute traffic across multiple servers to dampen attack impact.
- Traffic shaping – Prioritize legitimate user traffic over attack traffic using QoS mechanisms.
- Anti-DDoS services – Redirect traffic through DDoS mitigation service providers.
- Server rules – Block IP addresses conducting suspicious requests in web server configs.
Legal Implications of LOIC Attacks
Although LOIC is easily accessible, launching DDoS attacks can lead to legal consequences:
- Violates laws like the Computer Fraud and Abuse Act (CFAA) against unauthorized access/damage of computers.
- Can result in federal prosecution for criminal acts like extortion through DDoS threats.
- Civil lawsuits possible from organizations suffering financial harm due to attacks.
- Participants in voluntary botnets also face CFAA prosecution.
The “free speech” and “civil disobedience” defenses rarely hold up in court against LOIC attacks. Anyone involved in planning, coordinating or launching LOIC attacks can face legal action.
Conclusion
LOIC enables users to overwhelm targets with a flood of traffic easily but comes with high risks of unlawful activity. While LOIC may seem like a convenient tool for activists, the reality is participating in attacks can lead to serious criminal prosecution. Network operators should have safeguards in place to detect and mitigate LOIC DDoS attacks. Ultimately, the only responsible use of LOIC is for authorized stress testing against isolated test environments.
How to Mitigate and Protect Systems from LOIC
Implementing a DDoS protection solution and web application firewall (WAF) can help filter out and manage high volumes of malicious traffic while ensuring that legitimate users can still access the website or application.
Imperva DDoS Protection proxies all incoming traffic to block DDoS attacks from reaching your origin servers.
Imperva secures websites, networks, DNS servers, and individual IPs from network and application layer DDoS attacks. The cloud-based service keeps business operations running at high-performance levels, even during an attack.













