Protecting web applications and server infrastructures from DDoS attacks is no longer a choice for organizations having an online presence. The advent of DDoS-for-hire services has effectively lowered the bar for those capable of executing an assault, making all web entities a potential target.
A successful DDoS attack negatively impacts an organization’s reputation, in addition to damaging existing client relationships. Significant financial losses can amount to as much as $40,000 per hour for major enterprises. Smaller entities can face tens of thousands of dollars in damages, while longer, unmitigated assaults have the potential to be business-ending events.
Broadly speaking, there are several approaches to stopping DDoS attacks. The most common solutions rely on do-it-yourself (DIY) methods, on-premise mitigation appliances and off-premise cloud-based solutions.
While each offers its own benefits, their overall effectiveness in stopping DDoS is based on a number of factors. These include scalability and filtering capabilities, cost and ease of integration, as well as ease of use and hosting compatibility.
This is part of an extensive series of guides about Network Security
| Do It Yourself | On-Premise | Off-Premise | |
| CAPEX | None | Expensive | Moderate |
| OPEX | Minimal | Expensive | Moderate |
| Deployment method | On demand | On demand | On demand /always on |
| Time to mitigation | Significant | Significant | Moderate /none |
| Scalability | None | Limited | Virtually unlimited |
| Filtering | Limited | Significant | Significant |
| Ease of use | Complex | Moderate | Very easy |
| Integration | Complex | Moderate | Easy |
| Compatibility with hosting options |
Anything | Owned and dedicated | Anything |
DIY protection
DIY protection is widely considered to be a weak approach to DDoS mitigation. In practical terms, it relies on setting static traffic thresholds (e.g., using mod_evasive) and indiscriminate IP blacklisting rules. It is mostly preferred for budgetary reasons and rarely considered by online businesses.
A major drawback to DIY solutions is that they’re often employed as a reactive measure. Almost always, a configuration is manually tweaked after an initial attack wave has hit. While such a solution might stop similar future assaults, the successful first wave is usually enough to cause hours of downtime and other issues.
Moreover, perpetrators can easily modify their methods, attacking from disparate sources and using different vectors. This keeps your organization in a defensive position, where it has to repeatedly deploy additional configurations, while simultaneously attempting to recover from multiple downtime events. This can go on for days at a time.
The real issue with any DIY approach, however, is that it’s always constrained by network bandwidth, which severely limits the scalability required to stop network layer DDoS attacks.
With most assaults registering over 10Gbps and few organizations having more than a 10Gbps burst uplink, the DIY solution is almost always doomed to fail.
On-premise appliances
The on-premise approach to DDoS protection uses hardware appliances deployed inside a network, placed in front of protected servers.
Such appliances usually have advanced traffic filtering capabilities armed with a combination of geo-blocking, rate limiting, IP reputation and signature identification.
Typical mitigation appliances can be effectively used to filter out malicious incoming traffic. This makes them a viable option for stopping application layer attacks.
However, several factors make it unfeasible to rely on appliances:
- Scalability remains an issue. The ability of the hardware to handle large amounts of DDoS traffic is capped by a network’s uplink, which is rarely more than 10Gbps (burst).
- On-premise appliances need to be manually deployed to stop an attack. This impacts time-to-response and mitigation, often causing organizations to suffer downtime before a security perimeter can be established.
- Finally, the cost to purchase, install and maintain hardware is relatively high—especially when compared to a less costly and more effective cloud-based option. This makes mitigation appliances an impractical purchase, unless an organization is obligated to use on-premise solutions (e.g., by industry-specific regulations).
In the latter scenario, hardware is typically a part of a hybrid deployment, where it’s complemented by cloud-based solutions capable of defending against network layer attacks.
Off-premise, cloud-based solutions
Off-premise solutions are either ISP-provided or cloud-based. ISPs typically offer only network layer protection, while cloud-based solutions provide additional filtering capabilities required to stop application layer attacks. Both offer virtually limitless scalability, as they are deployed outside of a network and aren’t constrained by the previously-identified uplink limitations.
Generally, off-premise mitigation solutions are managed services. They don’t require any of the investment in security personnel or upkeep required by DIY solutions and on premise hardware. They’re also significantly more cost-effective than on-premise solutions, while providing better protection against both network and application layer threats.
Off-premise solutions are deployed either as an on-demand or always-on service, with most market-leading vendors offering both options.
On-demand option
Enabled by BGP rerouting, the on-demand option stops network layer attacks—including those directly targeting the origin server and other components of core network infrastructure. These include SYN or UDP floods, which are volumetric attacks designed to clog network pipes with fake data packets.
Always-on option
The always-on option is enabled through DNS redirection. It stops application layer assaults attempting to establish TCP connections with an application in an effort to exhaust server resources. These include HTTP floods, DNS floods and various low-and-slow attacks (e.g., Slowloris) .
Imperva DDoS protection
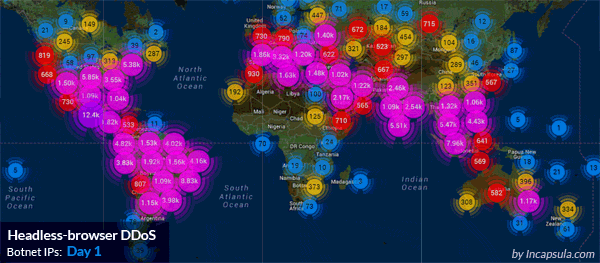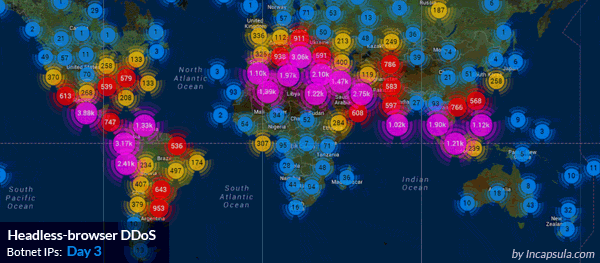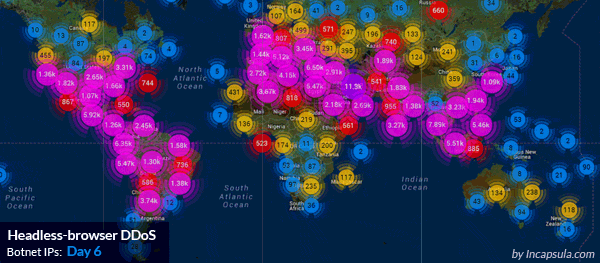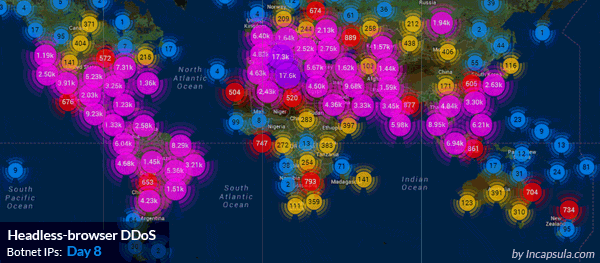
Imperva mitigates a massive HTTP flood: 690,000,000 DDoS requests from 180,000 botnets IPs.
Imperva provides easy to use, cost-effective and comprehensive DDoS protection that pushes the envelope for cloud-based mitigation technology.
Through a combination of on-demand and always-on solutions, a global network that offers near-limitless scalability and award winning filtering solutions for transparent mitigation, Imperva completely protects its customers from any type of DDoS attack.
Visit here to learn more about Imperva DDoS protection services.
See Additional Guides on Key Network Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of network security.
Microsegmentation
Authored by Tigera
- What is Microsegmentation? The Basics and Key Best Practices
- Application Segmentation: The Engine Behind Zero Trust
- Microsegmentation Security: The Evolution of Cybersecurity
SIEM
Authored by Exabeam
- What Is SIEM? Uses, Components, and Capabilities
- SIEM Log Management: The Complete Guide
- SIEM Architecture: Technology, Process and Data
AWS Security
Authored by NetApp













