What Is HIPAA
The Health Insurance Portability and Accountability Act of 1996, known as HIPAA, is a set of regulatory standard that specifies the lawful disclosure and use of protected health information (PHI).
HIPAA is a mandatory standard for the health industry in the United States. It applies to hospitals, other healthcare institutions, and their service providers who have access to Protected Health Information (PHI).
The Need for HIPAA
Healthcare providers and other organizations are transitioning to fully computerized operations, including electronic health records (EHR), computerized physician order entry (CPOE) systems, and pharmacy, radiology, and laboratory systems.
In this environment, HIPAA is essential for protecting patient information, and protecting healthcare providers from security breaches that may harm their reputation. Breaches may also result in fines or disciplinary action from the USA Office of Civil Rights (OCR) or the Centers for Medicare and Medicaid Services (CMS).
If a breach occurs, the law demands that affected organizations submit disclosure documents, which may involve sending all subjects a mailed letter. An organization may also need to provide patients with a year of identity protection services. This is costly and comes on top of the cost of the breach to the organization.
HIPAA Covered Entities
HIPAA compliance is enforced by the OCR and regulated by the Department of Health and Human Services (HHS). To achieve HIPAA compliance, companies dealing with PHI should follow network, process, and physical security procedures.
Two types of organizations are required to be HIPAA compliant:
- Covered entity—a health plan, health care provider, or a health care clearinghouse who, in its everyday activities, maintains, transmits or creates PHI. Typically, health care providers employed by a hospital are not classified as covered entities. Rather, the hospital is the covered entity and HIPAA compliance occurs at the hospital level.
- Business associates—a business or person that carries out a certain activity or function for, or offers a service to a covered entity, when that activity, function or service requires the business associate to have access to PHI stored by the covered entity.
HIPAA Privacy and Security Rules
Every business associate and a covered entity that has access to PHI must adhere with all HIPAA rules. This includes ensuring that the physical, technical and administrative measures are established and followed and that they comply with the HIPAA Privacy Rule.
If a breach of PHI takes place, the associates and entities should adhere to the procedure in the HIPAA breach notification rule.
HIPAA Privacy Rule (for Covered Entities only)
Requires organizations to provide safeguards to protect the privacy of personal health information. It also places conditions and limits on the disclosure and use of PHI, without patient permission.
Standards specified by the HIPAA privacy rule include the health care provider’s rights to prevent access to PHI, patient rights to obtain PHI, the content of notices of privacy practices, and the use and disclosure forms. All employees should be trained annually on these policies and procedures. This training should be documented.
HIPAA Security Rule (for Covered Entities and electronic PHI only)
A subcategory of the HIPAA privacy rule. It includes the standards that must be adhered to, to protect electronic Private Health Information (ePHI) when it is in transit or at rest. The rules are relevant to any system or any individual that has access to confidential patient information.
HIPAA Requirements In Depth: Additional Rules
HIPAA Breach Notification Rule
This rule draws a distinction between two types of breaches: minor breaches and meaningful breaches. Organizations need to report all breachers, irrespective of size, to the HHS, but there are special protocols for disclosure, depending on the type of breach. The breach notification rule safeguards PHI by making sure that covered entities remain liable for it. It also makes sure that patients are contacted if their personal health information has been put at risk.
HIPAA Omnibus Rule
This rule clarifies policies and procedures, amends definitions and increases the scope of the HIPAA compliance checklist to cover business associates and their subcontractors. It demands compliance from business associates and specifies the rules surrounding business associate agreements (BAAs).
These are contracts that are required between a covered entity and a business associate, or between two business associates because they can exchange PHI or ePHI.
HIPAA Enforcement Rule
This rule provides parameters used to investigate companies for alleged or potential breaches of HIPAA policy. It governs the penalties that may be given in case of a preventable breach of ePHI, investigations in case of a breach of ePHI, and the course of action for hearings.
Penalties can reach a maximum fine of $1,500,000 per year, per violation category. Penalties for intentional neglect can also result in criminal charges. Civil lawsuits for damages can also be filed by individuals personally affected by the breach.
HIPAA Security Safeguards
Entities that require HIPAA compliance need to adhere to all of the following safeguards:
-
Technical safeguards
The technology used to protect ePHI and to grant access to the information. HIPAA compliant entities must implement policies and procedures to ensure that ePHI is protected when being used, stored or transmitted. Technical safeguards are divided into four categories:
- Access control—only authorized individuals can access sensitive and confidential information.
- Audit control—entities need to use software, hardware and procedures to note attempted access to ePHI, record ePHI, and note what happens to the data after it has been accessed.
- Integrity controls—entities need to implement procedures to ensure that ePHI is not altered or destroyed improperly. This can be done by using a mechanism to verify ePHI.
- Transmission security—entities need to protect ePHI that is received or transmitted via an electronic network.
-
Physical safeguards
Entities need to prevent physical access to ePHI, regardless of its location. ePHI can be stored in the cloud, in a remote data center, or on servers located on the entity’s premises. Facility access needs to be confined to authorized personnel. Only authorized personnel should be able to obtain and use electronic media and workstations.
-
Administrative safeguards
Procedures and policies that link the Security Rule and Privacy Rule. These safeguards require an entity to appoint a privacy officer and security officer responsible for ePHI, and define how to govern the workforce. Additional requirements include: identifying and analyzing potential security risks, workforce training, sanctions for policy violations, and an evaluation system.
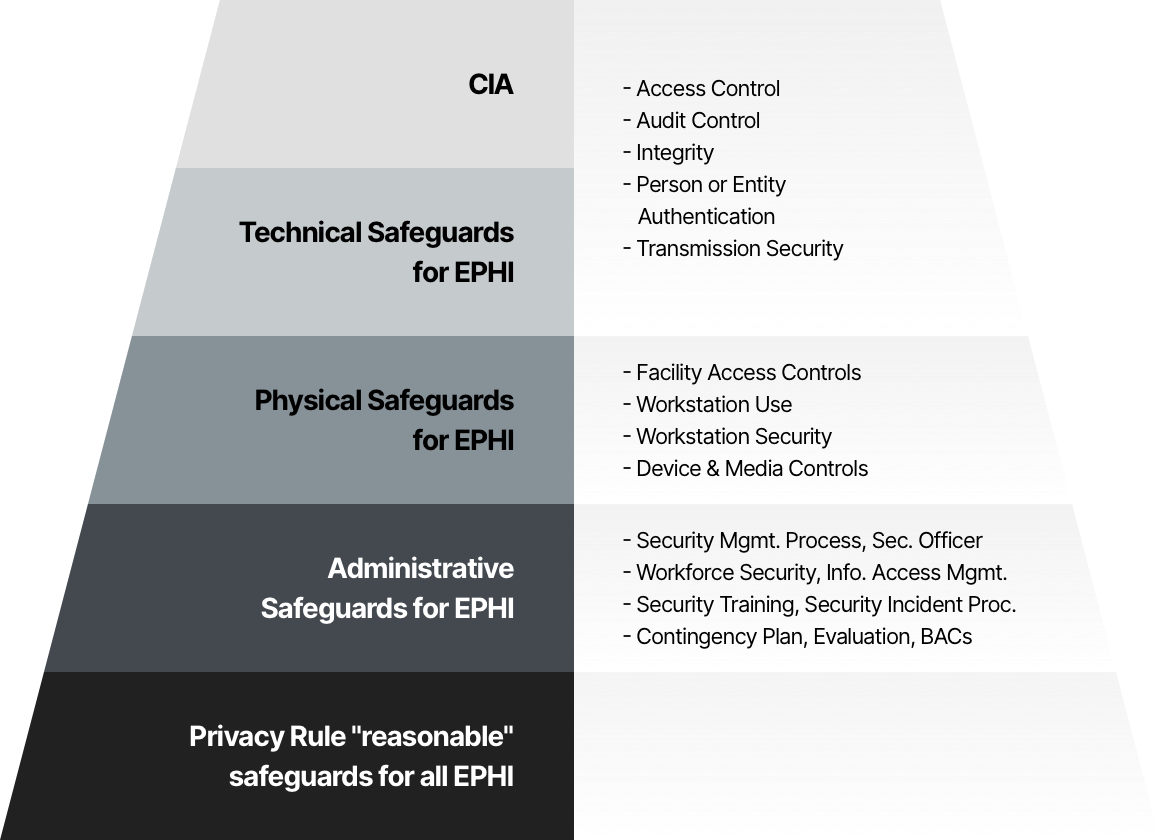
HIPAA safeguards by tier
A HIPAA Compliance Checklist
An organization will need to use a HIPAA compliance checklist to make sure its service or product meets all the administrative, physical and technical safeguards of the HIPAA security rule. They also need to fulfill all the requirements of the HIPAA privacy and breach notification rules.
The following is a brief checklist for complying with basic HIPAA requirements.
| Safeguard | Action |
| Self-audits | Carry out annual audits to evaluate technical, administrative, and physical gaps in compliance with HIPAA privacy and security standards. |
| Remediation plans | Apply remediation plans to counter compliance violations. These remediation plans should be entirely documented, including which gaps were fixed and calendar dates. |
| Policies, procedures, employee training | Create policies and procedures in keeping with HIPAA regulatory standards as specified by the HIPAA rules. Regularly update these procedures and policies to make room for changes to the organization. Train staff annually. |
| Documentation | Document all steps taken to become HIPAA compliant. This documentation is essential during a HIPAA investigation with the HHS. |
| Business associate management | Document all organizations with whom you share PHI. Execute business associate agreements to mitigate liability and make sure PHI is managed securely. |
| Incident management | Create a process to document the breach and let patients know their data has been leaked, in accordance with the HIPAA breach notification rule. |
How Imperva Can Help You Secure PHI for HIPAA Compliance
Imperva data security solutions can help you comply with several HIPAA provisions:
- HIPAA §164.306 Security Standard – our data masking solution ensures the confidentiality and integrity of ePHI and protects against threats and hazards. In addition, it enables the central management of information access and provides out-of-the-box HIPAA-compliant security policies.
- §164.308 Administrative Safeguards – our data masking service lets you conduct an assessment of potential risks and vulnerabilities, so you can, for example, manage vulnerabilities, respond in real time, perform user access management and apply sanctions against violating users.
- §164.312 Technical Safeguards – our service provides universal user tracking capabilities, automated tracking of activity in databases and file servers, ensures data integrity, and authenticates users trying to access ePHI.
- §164.502 Uses and Disclosures of Protected Health Information – our solution discovers where sensitive health data lives and secures it through sophisticated transformation techniques.
- §164.514 Other Requirements Relating to Uses and Disclosures of Protected Health Information – our data masking solution pseudonymizes sensitive data, to create data consistent with the HIPAA limited data set implementation specification.
For more details on HIPAA compliance and how Imperva solutions can help automate and simplify it, see our white paper: Compliance with the HIPAA Security Rule.



