What is Extended Detection and Response (XDR)?
Enhanced Detection and Response (XDR) is a new type of security platform, which provides unified visibility into multiple attack vectors across security silos. It collects data from networks, endpoints, cloud resources, email systems, and more, combining it into a unified attack story, using advanced analytics and machine learning.
XDR simplifies analyst workflow and improves productivity for security teams. It eliminates simple or repetitive tasks needed to investigate incidents, and provides one interface that lets analysts view all the data related to an attack, and respond to it—regardless of which IT system it is targeting. Most importantly, it can help uncover evasive threats that would not be possible to detect with siloed security solutions.
XDR: the Evolution of Endpoint Security Solutions
Most modern security organizations use a layered approach, also known as Defense in Depth. They use multiple security solutions, such as Endpoint Detection and Response (EDR), Network Traffic Analysis (NTA), and Security Information and Event Management (SIEM), to secure different parts of the IT environment, such as endpoints, cloud systems, and networks.
While a Defense in Depth approach is effective, it has limitations. Because security is organized into silos, typically with security analysts responsible for a specific silo (for example, endpoint or network security), there is a limited ability to detect and respond to attacks that move between silos, or target several IT systems in parallel.
XDR solves this problem by providing a unified security platform across security silos, tying together or replacing previous generation solutions like EDR, NTA, and SIEM.
Key Features of XDR
The key capabilities of XDR platforms include detection, investigation, smart recommendations, and threat hunting.
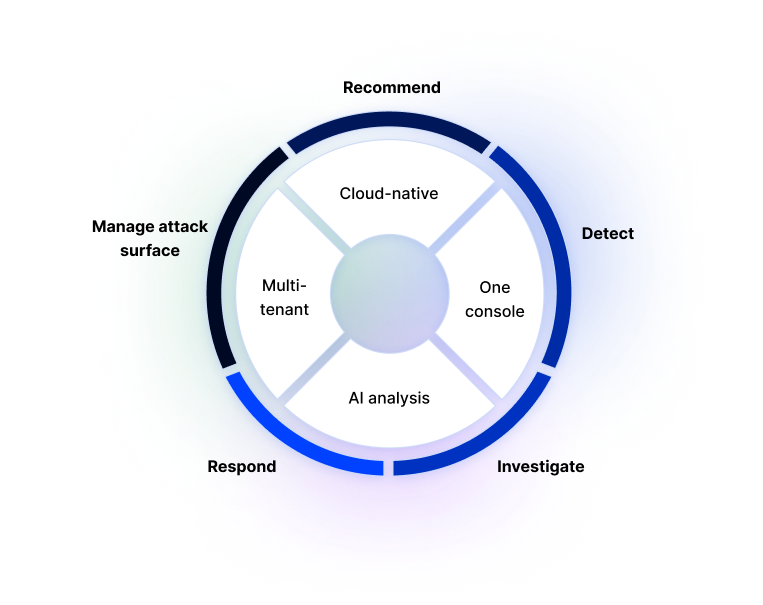
XDR key capabilities
Detection
Extended Detection and Response systems combine endpoint telemetry with data from a wide range of security tools, as well as data from logs and security information platforms. This allows XDR to detect a larger number of threats and to identify evasive threats, which would be invisible using other investigation methods.
Investigation
The human security team partners with machine-driven analytics to determine which threat information is relevant and apply situational security context. This reduces noise and makes it possible to quickly identify the root cause of a threat.
Recommendations
XDR software offers analysts smart recommendations for further investigation, providing guidelines for queries and other response actions. This allows security teams to contain or remediate detected threats more effectively, without requiring a time-consuming forensic investigation.
Threat hunting
XDR stores security data in a modern, large-scale data lake infrastructure, allowing analytics to perform query on data across security silos. This allows them to locate evasive and sophisticated threats hiding in the environment.
Response orchestration
An XDR vendor must be able to provide integrations with a broad partner ecosystem. To be effective, XDR must coordinate and process multiple alerts and extract meaning from security events. XDR should be able to prioritize risks and guide your response, allowing you to understand the context and orchestrate security across your organization more easily.
What are the Benefits of XDR Security?
XDR security platforms provide significant benefits compared to previous generations of security tooling. It can:
- Streamline a large volume of alerts by converting them to a smaller number on incidents for manual investigation
- Integrate incident response strategies informed by advanced context from security components
- Improve the speed and effectiveness of Security Operations Center (SOC) incident response
- Provide more sophisticated response mechanisms than traditional infrastructure control points, such as network and endpoints
- Provide automated detection of complex threats with minimal tuning required
- Automate repetitive tasks and save time for analysts
- Provide a common workflow and management for all analyst tiers
Requirements for XDR in the Enterprise
Here are a few important requirements and considerations when implementing XDR in a large enterprise.
Unified Telemetry
While traditional security products focus on a single point of attack on a surface or network element, XDR spans a broad lifecycle, from EDR/EPP to email and web gateways to identity and access management (IAM).
In a complex enterprise environment including on-premise resources, cloud infrastructure, and SaaS applications, this can provide consistent telemetry across all enterprise systems, with the ability to rapidly investigate and investigate threats on one pane of glass.
Open Platform
Some cybersecurity solutions enable integration of third-party components, while some are tightly coupled to solutions from a single vendor. XDR solutions are also divided into these two camps—some are open and some require the entire solution stack to be purchased from the same vendor.
Single-vendor XDR platforms have limited support for existing tools your organization may have already invested in, and may have limited ability to respond to changing threat conditions. No one tool, however fully featured, can compare to an entire ecosystem of technologies.
To overcome these issues and avoid vendor lock in, enterprises should prefer the open XDR approach, which uses standard big data systems, standard data formats, and an architecture with plugins and connectors, enabling easy integration with other platforms.
Cloud-Native Architecture
XDR solutions must be based on a cloud native architecture, supporting elastically scalable storage and flexible deployment on any computing infrastructure. Cloud native does not mean XDR must be deployed on the public cloud—solutions can also be deployed on premises, or in a hybrid model, but managed using cloud native principles to ensure scalability and agility.
Proactive Analysis
Enterprise cybersecurity requires speed and scale. Attackers can move quickly, outpacing overloaded security teams. XDR solutions must act autonomously and take proactive steps to discover attacks in their early stages. XDR solutions should leverage machine learning analysis to discover indicators of attacker activity long before they penetrate key systems or cause actual damage.
XDR should leverage historical data, both from the organization, from other clients using the same XDR platform, and from threat intelligence feeds, to detect new combinations of known and unknown threats. An XDR platform should constantly expand its portfolio of attack stories, compare security events to these stories, and use it to discover real threats and reduce false positives.
Improving Alert Quality
XDR changes the nature and life cycle of alerts reaching the SOC. XDR does not simply pass on log data or forward alerts. It collects data, validates its significance, and calls out “weak signals” that may be important to understanding the attack story. This helps security analysts identify real attacks, and provides the data needed for speedy remediation.
XDR can complement, supplement, or replace security information and event management (SIEM) and security orchestration and automation (SOAR) tools. By incorporating a wide range of inputs and feeding them into trainable behavioral analysis, it provides more effective detection and response, especially for targeted attacks.
What Should You Look For In an XDR Solution?
For an XDR solution to be effective, it must support a comprehensive and accessible view of the entire network. XDR should be a single, integrated platform—avoid offerings that are simply a new packaging of point solutions.
A good XDR solution should have the following capabilities:
- Integration with existing tools—the XDR engine must be able to work seamlessly throughout your security stack and integrate with native tools.
- Out-of-the-box capabilities—XDR should provide cross-stack correlation, detection, prevention and response with no tuning or setup required.
- Customization—you should be able to customize your own cross-stack rules, building on the engine’s detection and response capabilities.
- Automation and AI—advanced machine learning algorithms are essential for combining security data into a cohesive attack story, which is the main value of XDR. Check that your vendor has experience in developing AI models and doesn’t rely primarily on legacy technologies
- Human-machine collaboration—just as you can customize your security strategy, you should also be able to work with the information provided by XDR and take advantage of automated detection and response to prioritize, prevent and remediate the threats deemed meaningful.
- Ease of use—a key value of XDR is that it should save time and improve productivity for security analysts. Ensure the solution is really easy to use and accessible to all analyst tiers, including Tier 1.
Imperva Data Security
XDR solutions must be complemented by robust data security controls. Imperva protects all cloud-based data stores to ensure compliance and preserve the agility and cost benefits you get from your cloud investments:
Cloud Data Security – Simplify securing your cloud databases to catch up and keep up with DevOps. Imperva’s solution enables cloud-managed services users to rapidly gain visibility and control of cloud data.
Database Security – Imperva delivers analytics, protection and response across your data assets, on-premise and in the cloud – giving you the risk visibility to prevent data breaches and avoid compliance incidents. Integrate with any database to gain instant visibility, implement universal policies, and speed time to value
Data Risk Analysis – Automate the detection of non-compliant, risky, or malicious data access behavior across all of your databases enterprise-wide to accelerate remediation.














