What Is a Data Breach
A data breach or data leak is the release of sensitive, confidential or protected data to an untrusted environment. Data breaches can occur as a result of a hacker attack, an inside job by individuals currently or previously employed by an organization, or unintentional loss or exposure of data.
Data breaches can involve information leakage, also known as exfiltration—unauthorized copying or transmission of data, without affecting the source data. In other cases, breaches incur complete loss of data—as in ransomware attacks, which involve hackers encrypting data to deny access by the data owner.
In other words, in a data breach, hackers or employees release or leak sensitive data. As a result, the data might be lost, or used by perpetrators for various malicious purposes.
Types of Information Leaked in a Data Breach
A data breach can result in the leak of several types of information:
- Financial data—such as credit card numbers, bank details, tax forms, invoices, financial statements
- Medical or Personal Health Information (PHI)—as defined in the US HIPAA standard, “information that is created by a health care provider [and] relates to the past, present, or future physical or mental health or condition of any individual”
- Personally Identifiable Information (PII)—information that can be used to identify, contact or locate a person
- Intellectual property—such as patents, trade secrets, blueprints, customer lists, contracts
- Vulnerable and sensitive information (usually of military or political nature)—such as meeting recordings or protocols, agreements, classified documents
Data Breach Costs
The cost of a data breach can be devastating for organizations—in 2017, the average data breach cost its victim $3.5 million.
The immediate business costs of a breach include:
- Customer breach notifications
- Government fines
- Public relations costs
- Attorney fees
- Cyber security investigations
- Operational disruption
- Drop in stock price
Data breaches also have indirect, long term costs:
- Damage to brand and reputation
- Reduced trust by customers and partners
- Loss of customer relationships
- Loss of intellectual property
- Insurance premium increases
Causes of Information Leakage
The following are common causes of information leaks at organizations.
Insider leaks
Insider threats include disgruntled employees, former employees who still retain credentials to sensitive systems, or business partners. They might be motivated by financial gain, commercially valuable information, or a desire for revenge.
Payment fraud
Payment fraud is an attempt to create false or illegal transactions. Common scenarios are credit card breach resulting in fraud, fake returns, and triangulation frauds, in which attackers open fake online stores with extremely low prices, and use the payment details they obtain to buy on real stores.
Loss or theft
Organizations store sensitive information on devices such as mobile phones, laptop computers, thumb drives, portable hard drives, or even desktop computers and servers. Any of these devices could be physically stolen by an attacker, or unwittingly lost by organization staff, resulting in a breach.
Unintended disclosure
Many data breaches are not caused by an attack, but rather by unintentional exposure of sensitive information. For example, employees might view sensitive data and save it to a non-secure location, or IT staff might mistakenly expose a sensitive internal server to the Internet.
Data Breach Cycle
An attacker planning a data breach will typically go through the following steps, until they successfully obtain the sensitive data:
- Reconnaissance—an attacker starts by identifying potential targets. These could be IT systems, ports or protocols that are accessible and easy to penetrate or compromise. The attacker can also plan a social engineering attack against individuals in the company who have privileged access to systems.
- Intrusion and presence—the attacker breaches the organization’s security perimeter and gains a foothold in the organization’s network.
- Lateral movement and privilege escalation—the attacker’s entry point may not allow them to immediately obtain the sensitive data. The attacker will attempt to improve their position by moving to other systems and user accounts, and compromising them, until they provide access to the desired data.
- Exfiltration—the attacker transfers the sensitive data outside the organization’s network, and either uses the data for personal gain, resells it on the black market, or contacts the organization to demand ransom.
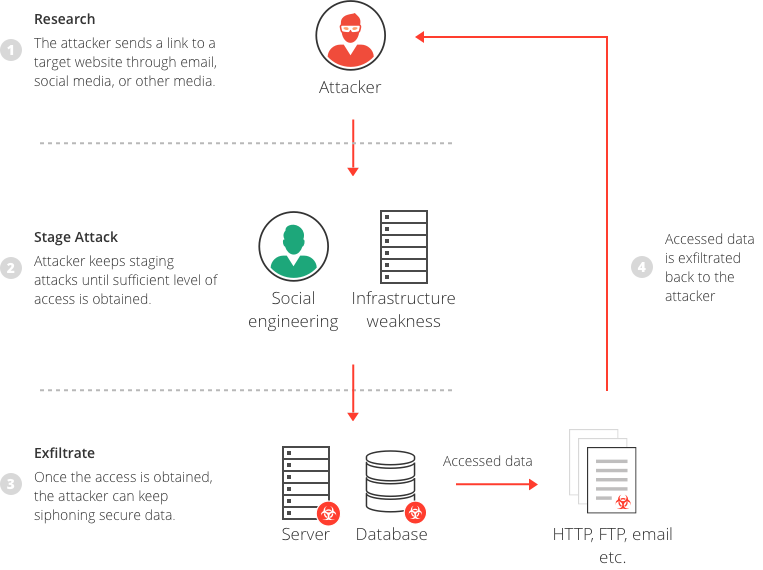
Example of data breach attack cycle
Data Leakage Prevention
In 2017, the average data breach in the United States took 206 days to detect. A data leak frequently occur without an organization’s knowledge, and security experts agree that data leaks are not completely preventable. Therefore, sound practices must be in place to detect, contain and remediate data breaches.
In addition, here are best practices organizations can use to prevent data breaches:
- Vulnerability assessments—systematic review of security weaknesses in organizational systems, with continuous action to remediate high priority security gaps.
- Penetration testing—simulated cyber attacks against IT systems to check exploitable vulnerabilities.
- Training and awareness—many breaches occur via unintentional or negligent exposure of data, or social engineering attacks such as Phishing. Preventive measures include training staff on security procedures, helping them avoid social engineering attacks, and clearly labeling sensitive data.
- Mitigation and recovery plans—security staff must document known threats to sensitive systems, and maintain plans for responding, containing, mitigating and recovering from security incidents.
- Defending the network perimeter—security tools can be used to deny unauthorized access and prevent many types of attacks against information systems. For example, Imperva’s Web Application Firewall protects from all common web application security threats such as SQL injection, Cross Site Scripting (XSS) and remote file inclusion (RFI).
Imperva Data Protection Solutions
Imperva’s industry-leading data security solution protects against data breaches, where your data wherever it lives—on premises, in the cloud and in hybrid environments. It also provides security and IT teams with full visibility into how the data is being accessed, used, and moved around the organization.
Our comprehensive approach relies on multiple layers of protection, including:
- Database firewall—blocks SQL injection and other threats, while evaluating for known vulnerabilities.
- User rights management—monitors data access and activities of privileged users to identify excessive, inappropriate, and unused privileges.
- Data masking and encryption—obfuscates sensitive data so it would be useless to the bad actor, even if somehow extracted.
- Data loss prevention (DLP)—inspects data in motion, at rest on servers, in cloud storage, or on endpoint devices.
- User behavior analytics—establishes baselines of data access behavior, uses machine learning to detect and alert on abnormal and potentially risky activity.
- Data discovery and classification—reveals the location, volume, and context of data on premises and in the cloud.
- Database activity monitoring—monitors relational databases, data warehouses, big data and mainframes to generate real-time alerts on policy violations.
- Alert prioritization—Imperva uses AI and machine learning technology to look across the stream of security events and prioritize the ones that matter most.



