What is Website Defacement
Web defacement is an attack in which malicious parties penetrate a website and replace content on the site with their own messages. The messages can convey a political or religious message, profanity or other inappropriate content that would embarrass website owners, or a notice that the website has been hacked by a specific hacker group.
Most websites and web applications store data in environment or configuration files, that affects the content displayed on the website, or specifies where templates and page content is located. Unexpected changes to these files can mean a security compromise and might signal a defacement attack.
Common causes of defacement attacks include:
- Unauthorized access
- SQL injection
- Cross-site scripting (XSS)
- DNS hijacking
- Malware infection
Examples of Website Defacement Attacks
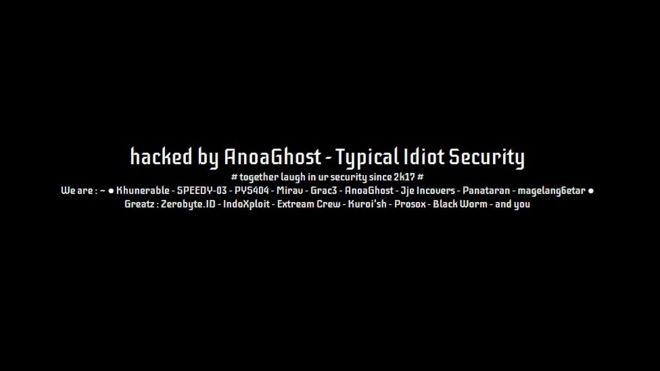
Message displayed during defacement of a UK National Health Services website in 2018. Source: BBC.
Some of the world’s biggest websites have been hit by defacement attacks at some point. A defacement attack is a public indicator that a website has been compromised, and causes damage to the brand and reputation, which lasts long after the attacker’s message has been removed.
NHS defacement attack
In 2018, the BBC reported that a website hosting data from patient surveys, operated by the UK National Health Service (NHS), was defaced by hackers. The defacement message said “Hacked by AnoaGhost.” The message was removed within a few hours, but the site may have been defaced for as long as five days. The attack raised concerns about the safety of medical data controlled by the NHS.
Google.ro and PayPal.ro
In 2012, users could not access Google Romania, and instead were taken to a defacement screen posted by MCA-CRB, the “Algerian Hacker”. The defacement was in place for at least an hour. The attack was performed by DNS hijacking—attackers managed to falsify DNS responses and redirect users to their own server instead of Google’s. The same attack was carried out against the domain paypal.ro. The MCA-DRB hacker group was responsible for 5,530 website defacements across all five continents, many of them targeting government sites.
Largest cyber attack in Georgia’s history
In 2019, Georgia, a small European country, experienced a cyber attack in which 15,000 websites were defaced, and then knocked offline. Among the websites affected were government websites, banks, the local press and the large television broadcasters. A Georgian web hosting provider called Pro-Service took responsibility for the attack, releasing a statement that a hacker breaches their internal systems and compromised the websites.
Website Defacement Prevention: DIY Best Practices
The following are simple best practices you can implement today to protect your website and minimize the chances of a successful defacement attack.
Use the Principle of Least Privilege (POLP)
By limiting privileged or administrative access to your websites, you reduce the chance that a malicious internal user, or an attacker with a compromised account, can do damage.
Avoid giving administrative access to your site to individuals who don’t really need it. Even for users like webmasters and IT staff, give them only the privileges they actually need to perform their roles. Pay careful attention to contractors and external contributors, ensure they don’t receive excessive privileges, and revoke their privileges when they stop working on the site.
Avoid default admin directory and admin email
Never use the default name for your admin directory, because hackers know the default names for all common website platforms and will attempt to gain access to them. Similarly, avoid using the default admin email addresses, because attackers will try to compromise them using phishing emails or other methods.
Limit the use of add-ons and plugins
The more plugins or add-ons you use on platforms like WordPress, Drupal of Joomla, the more likely you are to face software vulnerabilities. Attackers may discover zero-day vulnerabilities, and even if a security patch is available, upgrades will not be instantaneous, exposing the website to risk. Needless to say, carefully maintain and upgrade all website plugins and quickly apply security updates.
Error Messages
Avoid displaying overly detailed error messages on your site, because they can reveal weaknesses to an attacker, which can help them plan an attack.
Limit file uploads
Many websites enable users to upload files, and this is an easy way for attackers to penetrate your internal systems with malware. Ensure that user-uploaded files never have executable permission, and if possible, run virus scans on all files uploaded by your users.
Use SSL/TLS
Always enable SSL/TLS on all website pages, and avoid linking to unsecured HTTP resources. When SSL/TLS is used consistently across your site, all communication with users is encrypted, preventing many types of Man in the Middle (MITM) attacks which can be used to deface your website.
Advanced Website Defacement Prevention Measures
While security best practices are important, they cannot prevent many attacks. The following techniques are used by automated security tools to comprehensively protect websites against defacement.
Scan for vulnerabilities
Regularly scan your website for vulnerabilities, and invest time in remediating vulnerabilities you discover. This will often be time consuming, because upgrading a website platform or a plugin might break content or site functionality. But this is one of the best ways to improve security in general, and reduce the chance of penetration and defacement in particular.
Prevent SQL injection
Ensure that all forms or user inputs do not allow the injection of code into your internal systems. Sanitize your inputs to prevent regular expressions, or any characters or strings that may be used to execute code.
Defend against Cross Site Scripting (XSS)
XSS enables an attacker to embed scripts on a web page, which execute when a visitor loads the page, and can result in defacement, as well as other damaging attacks such as session hijacking or drive-by downloads.
Sanitizing inputs can help prevent XSS, and you should be careful not to insert user inputs or untrusted data into <script>, <style>, <div>, or similar tags in your HTML code. A web Application firewall (WAF) can also help prevent XSS by blocking communication with unknown or malicious external domains.
Bot management
Most defacement attacks are not the result of a manual, targeted attack. Instead, hackers use bots to automatically scan a large number of websites for vulnerabilities, and when a vulnerability is discovered, they automatically compromise and deface the site. Hackers can achieve dubious fame by launching a broad, automated attack against thousands or millions of sites.
Bot management technology uses multiple approaches to mitigate bad bots, such as: static inspection of traffic headers; challenge-based detection, identifying bots by asking them to process Javascript or interact with CAPTCHA; and behavior-based inspection of website visitors to uncover bot traffic. These techniques make it possible to protect against malicious bots, ensuring that legitimate traffic can access to your site uninterrupted.
Imperva Application Security
Imperva provides WAF provides robust protection against web application threats such as XSS and SQL injection, which can result in website defacement. Imperva’s solution also includes Bot Management, which detects anomalous bot behavior to identify automated assaults that can result in defacement.
In addition, Imperva provides multi-layered protection to make sure websites and applications are available, easily accessible and safe. The Imperva application security solution includes:
- DDoS Protection—maintain uptime in all situations. Prevent any type of DDoS attack, of any size, from preventing access to your website and network infrastructure.
- CDN—enhance website performance and reduce bandwidth costs with a CDN designed for developers. Cache static resources at the edge while accelerating APIs and dynamic websites.
- WAF—cloud-based solution permits legitimate traffic and prevents bad traffic, safeguarding applications at the edge. Gateway WAF keeps applications and APIs inside your network safe.
- Bot protection—analyzes your bot traffic to pinpoint anomalies, identifies bad bot behavior and validates it via challenge mechanisms that do not impact user traffic.
- API security—protects APIs by ensuring only desired traffic can access your API endpoint, as well as detecting and blocking exploits of vulnerabilities.
- Account takeover protection—uses an intent-based detection process to identify and defends against attempts to take over users’ accounts for malicious purposes.
- RASP—keep your applications safe from within against known and zero‑day attacks. Fast and accurate protection with no signature or learning mode.
- Attack analytics—mitigate and respond to real cyber security threats efficiently and accurately with actionable intelligence across all your layers of defense.













