Denial-of-service (DoS) attacks are one of the most disruptive and pervasive security threats that organizations face on a regular basis. One such variant, the UDP Flood attack, has gained notoriety for its ability to overwhelm systems swiftly. This article provides an in-depth look at UDP Flood attacks, their mechanisms, and the countermeasures that can be employed to mitigate their impact.
What is a UDP Flood Attack?
A UDP Flood attack is a type of volumetric DoS attack that exploits the User Datagram Protocol (UDP). Unlike the Transmission Control Protocol (TCP), UDP is sessionless and connectionless, making it a unique vector for attackers.
In a UDP Flood attack, the attacker sends a massive number of UDP packets to random ports on the target host. This barrage of packets forces the host to:
- Check for applications listening at each port.
- Realize that no application is listening at many of these ports.
- Respond with an Internet Control Message Protocol (ICMP) Destination Unreachable packet.
The high volume of UDP packets compels the targeted system to send out a multitude of ICMP packets. This can render the system unreachable to legitimate clients. To further disguise their malicious behavior, attackers may spoof the IP address of the UDP packets. This ensures that the flood of return ICMP packets doesn’t reach them, effectively anonymizing their location. Modern operating systems have implemented measures to mitigate this aspect of the attack by limiting the rate of ICMP responses.
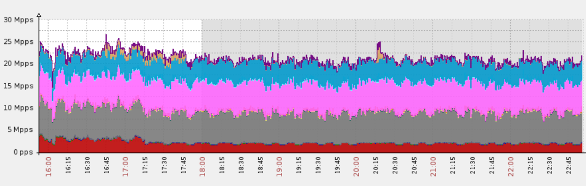
Imperva mitigates a massive UDP (DNS) flood, peaking at over 25 million packets per second
Tools Used in UDP Flood Attacks
Several tools have been developed to facilitate UDP Flood attacks. Some of the most notable include:
- Low Orbit Ion Cannon (LOIC): A popular tool among hacktivist groups, LOIC is capable of launching UDP, TCP, and HTTP floods.
- UDP Unicorn: A Win32 UDP flooding/DoS utility.
Countermeasures Against UDP Flood Attacks
Protection against UDP Flood attacks requires a multi-faceted approach. Here are some effective countermeasures:
ICMP Rate-Limiting
By limiting the rate at which ICMP responses are sent at the operating system level, systems can prevent being overwhelmed by the flood of return packets.
Firewall-Level Filtering
Deploying firewalls at strategic points in a network can filter out malicious traffic. With this approach, the potential victim neither receives nor responds to the malicious UDP packets. However, firewalls, being stateful, can also be susceptible to flood attacks if they become overwhelmed by the sheer volume of sessions.
Filtering UDP Packets at the Network Level
DNS requests typically use UDP. Therefore, any other source generating vast amounts of UDP traffic can be deemed suspicious. Such traffic can be filtered and rejected at the network level.
The Importance of Vigilance
While the above countermeasures can significantly reduce the risk of a UDP Flood attack, no system can be deemed entirely invulnerable. Regular network monitoring, combined with up-to-date security protocols, is essential for quickly detecting and responding to anomalies.
The Evolution of UDP Flood Attacks
Over the years, as technology advanced, so have the tactics employed by cybercriminals. UDP Flood attacks, which were once considered rudimentary, have evolved in sophistication. Today, attackers can combine UDP Flood with other attack vectors to maximize disruption. This hybrid approach can be particularly challenging to defend against, as it targets multiple vulnerabilities simultaneously.
Amplification Attacks
One of the more recent evolutions in UDP Flood attacks is the use of amplification techniques. In an amplification attack, the attacker leverages vulnerable third-party servers to amplify the volume of traffic directed at the target. The attacker sends a small request to these servers with a spoofed IP address . In response, these servers send a significantly larger amount of data to the target, amplifying the attack’s impact.
DNS servers, NTP servers, and SSDP devices have all been exploited in amplification attacks. The amplification factor can vary, but in some cases, it can increase the attack volume by a factor of 50 or more.
The Economic Impact of UDP Flood Attacks
The consequences of a successful UDP Flood attack extend beyond just technical disruptions. For businesses, the economic ramifications can be severe.
Downtime Costs
When critical systems or websites go offline, businesses can lose significant revenue, especially if its operations are online. For example, eCommerce can experience substantial losses every minute they’re offline.
Reputation Damage
Beyond immediate financial losses, a UDP Flood attack can damage the organization’s reputation. Customers expect reliability, and repeated outages can erode trust, which leads to customer attrition.
Remediation Costs
After an attack, businesses will often incur hefty and unexpected expenses. They may need to invest in improved security infrastructure and forensic investigations, among other expenses.
The Global Landscape of UDP Flood Attacks
Cyberattacks, including UDP Flood, are a global concern. Certain regions have become hotspots for such activities, either as sources of attacks or as primary targets.
Attack Origins
Research shows that a significant portion of DDoS attacks, including UDP Flood, originate from countries like China, Russia, and the United States. The reasons vary, from the availability of vulnerable devices to state-sponsored activities.
Targeted Regions
While any organization worldwide can be a target, companies in North America and Europe often face a higher number of attacks, possibly due to the economic impact potential in these regions.
Conclusion
UDP Flood attacks, though simple in their execution, can cause significant disruption. By understanding their mechanics and implementing robust countermeasures, organizations can safeguard their digital assets and ensure uninterrupted service to their users.
How Imperva Mitigates UDP Attacks
UDP Flood attacks, though simple in their execution, can cause significant disruption. Imperva DDoS Protection proxies all incoming traffic to block layer 3/4 and layer 7 attacks, such as UDP Flood, from reaching origin servers.
Imperva secures websites, networks, DNS servers and individual IPs from the largest and most sophisticated types of DDoS attacks – including network, protocol and application level attacks – with minimal business disruption. The cloud-based service keeps online businesses up and running at high performance levels even under attack, avoiding financial losses and serious reputation damage.
The high-capacity global network holds more than six Terabits per second (6 Tbps) of scrubbing capacity and can process more than 65 billion attack packets per second. It scales as needed to absorb the largest attacks that can overwhelm legacy appliances. Imperva incorporates crowdsourced learnings from emerging attack methods across our network, utilizing machine learning for the most up-to-date, accurate, and advanced protection.













