What is spear phishing
Spear phishing is a social engineering attack in which a perpetrator, disguised as a trusted individual, tricks a target into clicking a link in a spoofed email, text message or instant message. As a result, the target unwittingly reveals sensitive information, installs malicious programs (malware) on their network or executes the first stage of an advanced persistent threat (APT), to name a few of the possible consequences.
While similar to phishing and whaling attacks, spear phishing is launched in a unique way and its targets differ from other social engineering assaults. As a result, the attack deserves special attention when formulating your application security strategy.
Spear phishing example
The following example illustrates a spear phishing attack’s progression and potential consequences:
- A spoofed email is sent to an enterprise’s sysadmin from someone claiming to represent www.itservices.com, a database management SaaS provider. The email uses the itservices.com customer mailing template.
- The email claims that itservices.com is offering a free new service for a limited time and invites the user to sign up for the service using the enclosed link.
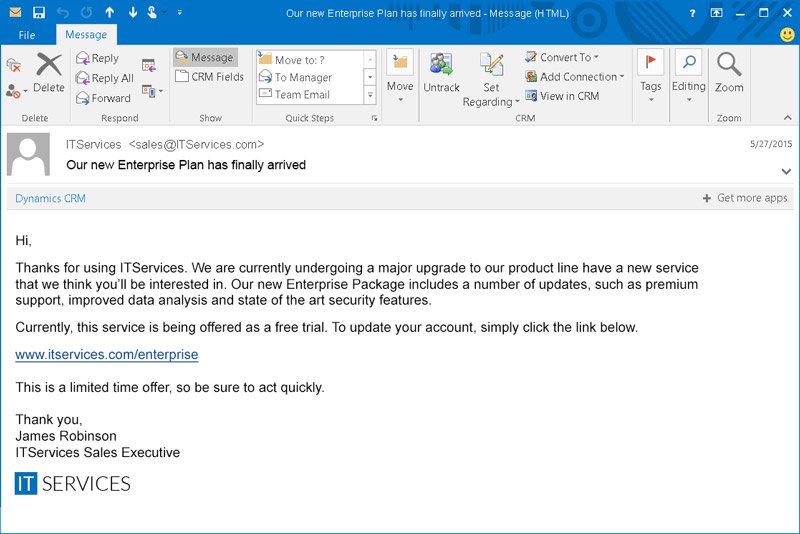
- After clicking on the link, the sysadmin is redirected to a login page on itservice.com, a fake website identical to the itservices.com registration page.
- At the same time, a command and control agent is installed on the sysadmin’s machine, which can then be used as a backdoor into the enterprise’s network to execute the first stage of an APT.
Spear phishing vs. phishing and whaling attacks
Spear phishing, phishing and whaling attacks vary in their levels of sophistication and intended targets. Their differences are highlighted below.
Phishing
Phishing involves sending malicious emails from supposed trusted sources to as many people as possible, assuming a low response rate. For example, a phishing email might purport to be from PayPal and ask a recipient to verify their account details by clicking on an enclosed link, which leads to the installation of malware on the victim’s computer.
Phishing emails are impersonal, sent in bulk and often contain spelling errors or other mistakes that reveal their malicious intent. The problem is that not everyone notices these subtle hints. Trusted logos and links to known destinations are enough to trick many people into sharing their details.
Spear phishing emails, on the other hand, are more challenging to detect because they appear to come from sources close to the target. Cyber-criminals send personalized emails to particular individuals or groups of people with something in common, such as employees working in the same department.
Whaling
Whaling uses deceptive email messages targeting high-level decision makers within an organization, such as CEOs, CFOs, and other executives. Such individuals have access to highly valuable information, including trade secrets and passwords to administrative company accounts.
The attacker sends emails on issues of critical business importance, masquerading as an individual or organization with legitimate authority. For example, an attacker may send an email to a CEO requesting payment, pretending to be a client of the company.
Whaling attacks always personally address targeted individuals, often using their title, position and phone number, which are obtained using company websites, social media or the press.
The difference between whaling and spear phishing is that whaling exclusively targets high-ranking individuals within an organization, while spear phishing usually goes after a category of individuals with a lower profile.
Spear phishing mitigation
The targeted nature of spear phishing attacks makes them difficult to detect. However, several risk prevention measures can help, including two-factor authentication (2FA), password management policies and educational campaigns.
Two factor authentication
2FA helps secure login to sensitive applications by requiring users to have two things: something they know, such as a password and user name, and something they have, such as a smartphone or cryptographic token. When 2FA is used, even if a password is compromised using a technique like spear phishing, it’s of no use to an attacker without the physical device held by the real user.
Password management policies
A prudent password management policy should take steps to prevent employees from using corporate access passwords on fake external websites.
One example of such a policy is to instruct employees to always enter a false password when accessing a link provided by email. A legitimate website won’t accept a false password, but a phishing site will.
Educational campaigns
At the organizational level, enterprises can raise awareness and actively train employees, highlighting spear phishing attacks as an important threat. Training materials can feature real-life examples of spear phishing, with questions designed to test employee knowledge. Employees who are aware of spear phishing are less likely to fall victim to an attack.
Spear phishing protection from Imperva
Imperva offers two solutions that can help secure against phishing attempts, including spear phishing:
- Imperva cloud Login Protect provides 2FA protection for URLs in a website or web application. The service works with web pages that have URL parameters or use AJAX, where 2FA can be harder to implement. Login Protect is deployed in seconds, doesn’t require hardware or software installation and provides easy management of roles and privileges directly from your Incapsula dashboard.
- Imperva’s cloud-based Web Application Firewall (WAF) blocks malicious requests at the network edge. It prevents malware injection by compromised user accounts and can block reflected XSS attacks deriving from a phishing episode.













