What is SNMP Reflection / Amplification
A Simple Network Management Protocol (SNMP) reflection/amplification attack is a distributed denial of service (DDoS) technique that exploits misconfigured SNMP servers to overwhelm victims with user datagram protocol (UDP) traffic. Attackers spoof the IP address of a target device or network and send SNMP queries to broadcast addresses, generating high volumes of reflected traffic.
SNMP Protocol Overview
SNMP is a protocol used to monitor and manage network-connected devices like routers, servers, switches, printers, and more. It uses UDP port 161/162 for communication. Network management systems send SNMP query packets like GET, GETNEXT, SET to poll managed devices for status and configurations. Managed routers, switches, servers, printers, and other SNMP-enabled devices receive the queries and respond with requested status data, configuration details, performance metrics, etc.
SNMP utilizes connectionless UDP transport for queries and responses, with no transport session or handshake required prior to data exchange. Importantly, SNMP responses frequently contain much more data than the original queries, as configuration and status data can far exceed the query packet size. These inherent SNMP protocol traits of UDP transport and asymmetric response sizes make it a prime vector for DDoS reflection and amplification attacks.
SNMP Attack Mechanism
Carrying out an SNMP reflection attack involves the attacker spoofing the victim’s IP address as the source IP address in the SNMP query packet. Large volumes of SNMP GET or GETNEXT query packets are sent to the broadcast addresses of networks known to contain many SNMP-enabled devices. Thousands of routers, switches, servers, and other SNMP-managed devices on those networks receive the query and automatically respond as designed. Because the source IP is spoofed, the devices send their larger SNMP response packets back to the victim’s IP address. The victim’s network is overwhelmed by massive floods of inbound UDP traffic generated from the responses. By abusing broadcast networks and reflecting traffic from many distributed devices, attackers can direct huge volumes of traffic at their target(s).
Amplification Factor
- 5-10X – Even basic SNMP status queries often result in 5 to 10 times more response data.
- >50X – Large device configurations or requested SNMP data can reflect responses over 50 times the query size.
- >100X – SNMP bugs like the counter overflow result in enormous responses, yield extreme amplification factors that can multiply by hundreds.
This makes even very small SNMP query volumes capable of triggering floods well exceeding 1Gbps, or more, when reflected by enough devices.
Characteristics of SNMP Attacks
Some key traits of SNMP reflection/amplification DDoS attacks include the spoofing that hides the true source IP of the attacker, obstructing tracing and blocking. The asymmetric SNMP response sizes multiply traffic volumes directed at victims. SNMP abuses stateless UDP for reflection, unlike transmission control protocol’s (TCP) handshake requirements. It leverages responses from many devices spread across multiple networks. Operating at the network layers, it overwhelms network capacity and it masks the attacker’s location by obscuring the attack source.
-
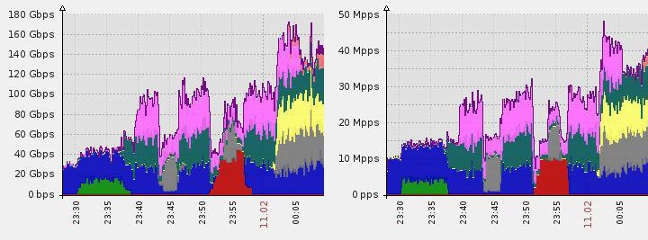
Imperva protects against a volumetric DDoS attack: 180Gbps and 50 million packets per second
The Impact of SNMP Attacks
The crippling effects on targeted networks and applications include complete service disruptions from the traffic floods that lead to website, app, and infrastructure outages. The downtime caused by an attack translates directly into lost business revenue. Users often lose trust as a result of an outage. Further, employees cannot work during outages, which impedes operations. For security and forensic teams, extensive DDoS mitigation services may be required to scrub the attack traffic.
SNMP DDoS Attacks through Time
- 2022 – Major infrastructure providers impacted by large SNMP DDoS attacks.
- 2002 – The SNMPReflector tool emerges, making it easier for bad actors to launch SNMP DDoS attacks.
- 2009 – Massive SNMP DDoS attacks target government sites in South Korea leveraging huge amplification factors.
- 2013 – The hacktivist group Anonymous heavily abuses SNMP reflection in DDoS attacks that disrupted banking sites.
- 2016 – A record-setting 400+ Gbps SNMP amplification DDoS attack impacts DNS provider Dyn.
Defending Against SNMP Attacks
Organizations can implement several protections to mitigate the risk of an SNMP attack:
- Restrict SNMP to dedicated secure management networks only, avoiding public exposure.
- SNMP should be disabled completely on all devices if not strictly required, and functionality should be limited to the most secure configurations.
- Employ active traffic monitoring to identify spikes in outbound SNMP traffic, which may indicate exploitation.
- Filter spoofed carrier SNMP and block customer networks that have participated in attacks.
- Use on-premise or upstream scrubbing services that are designed to detect and mitigate high-volume SNMP attacks.
Ongoing Threats
There are several factors contributing to the continued SNMP reflection attacks that threaten organizations:
- The yearly growth of overall DDoS attack bandwidths and packet volumes
- Mass proliferation of poorly secured SNMP-enabled IoT devices
- Wider IPv6 deployment enables new protocol attack vectors
- User-friendly attack tools simplify launching even for unskilled attackers
How to Mitigate an SNMP Attack
To mitigate reflective DDoS threats like SNMP amplification:
- Devices should be patched to eliminate firmware-level protocol flaws that increase amplification factors
- Enable access restrictions to reduce exposure by limiting management services to dedicated secure networks
- Actively scrutinize traffic patterns for abnormal reflection indicators, which can enable earlier detection
- Significantly over-provisioning network capacity and DDoS mitigation capabilities to absorb attacks
- Filter collaboratively across multiple networks and providers