What is R.U.D.Y?
R.U.D.Y., short for “R-U-Dead-Yet?”, is a distributed denial-of-service (DDoS) attack tool used to execute slow-rate denial-of-service (DoS) attacks that gradually overwhelm web servers. The attack tool is named after an album by the Finnish death metal band Children of Bodom. The tool first emerged in hacking forums around 2010.
R.U.D.Y. implements a type of attack known as a low and slow DDoS. The goal is to open a relatively small number of connections to the target over an extended period of time and keep those sessions open as long as possible. This eventually consumes all available connections and resources on the server, making it inaccessible to legitimate users.
-
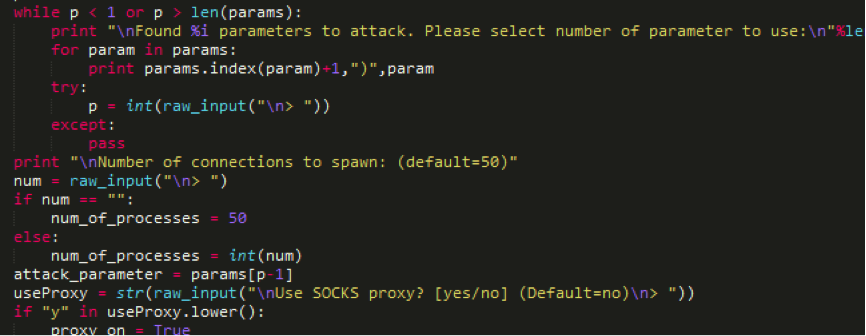
Excerpt from R.U.D.Y. v2.2 script
How R.U.D.Y. Works
The R.U.D.Y. tool carries out its attack by exploiting web forms on a target’s site. It first scans the website to detect and catalog web-based forms that can be used for malicious submissions.
Once target forms are identified, R.U.D.Y. sends crafted HTTP POST requests to those forms with a Content-Length header specifying an extremely large amount of data will be transmitted. However, instead of sending the data immediately, it begins transmitting the form data one byte at a time, with long ~10-second delays between each byte.
This opens connections very slowly while indicating a huge amount of data is still coming. The long Content-Length header tricks the server into keeping these connections open indefinitely while waiting for the rest of the data to be transmitted. Eventually, the application handling each request begins to back up, and resources are exhausted.
By precisely controlling the timing and spacing of packets, R.U.D.Y. makes the attack very difficult to detect. The connections persist by re-initiating whenever they time out. Eventually, the server’s connection table fills up completely, crashing the web application due to resource starvation.
Latest R.U.D.Y. Variants
The latest variants of the R.U.D.Y. tool have added features to make the attacks more effective. R.U.D.Y. can now use randomized time intervals between sending bytes to better avoid detection. It also supports using SOCKS proxies — a network protocol for facilitating communication with a server through a firewall by routing traffic to the server on behalf of the client — to mask the attacker’s real IP address.
For web apps that use session cookies, R.U.D.Y. can maintain and reuse session cookies to look more like a legitimate user. These enhancements make R.U.D.Y. attacks harder to detect and allow for it to bypass common countermeasures.
Dangers of R.U.D.Y. Attacks
R.U.D.Y. and other slow-rate DDoS attacks are dangerous for several reasons. Sending a small volume of packets across a limited number of connections in a slow manner makes these attacks nearly invisible to many DDoS detection solutions that are designed to identify sudden volumetric spikes.
The attacks can also persist for a very long period of time by re-initiating connections when they time out, allowing the attack to continue for days or weeks. Keeping a multitude of connections open simultaneously steadily exhausts critical server resources like memory, sockets, threads, and file handles.
Web applications and sites can be made completely inaccessible to users while under a R.U.D.Y. attack. Prolonged outages due to successful attacks can undermine customer confidence and cause substantial reputational harm.
Mitigating R.U.D.Y. DDoS Attacks
There are several technical methods available to detect and mitigate R.U.D.Y. DDoS assaults:
Monitoring for Attacks
Carefully monitoring server resources like memory utilization, concurrent connections, idle threads, and other metrics can reveal abnormal exhaustion, This can be an indicator that an attack is occurring.
Behavioral analysis can also simulate application stack resource requirements without directly connecting to the server itself. Any detected misuse can then be traced back and mitigated.
Traffic Inspection and Filtering
Proxy-based DDoS protection services provide another very effective solution. By inspecting all traffic on its way to the server, a secured proxy system can easily identify and block the anomalous partial connections and headers used in R.U.D.Y. attacks.
IPS devices can be configured with signature detection to recognize R.U.D.Y. and other low and slow attack patterns and block them.
Reducing the Impact of a R.U.D.Y. Attack
For an added layer of protection, restricting the number of connections per source IP address can help reduce the impact if any attacks do get through. Setting lower TCP timeouts can prevent connections from persisting as long.
DDoS mitigation services that scrub attack traffic while still allowing legitimate users to access the site can provide protection during an active assault.
A layered security strategy combining monitoring, analysis, and proxy techniques gives the best protection against R.U.D.Y. and other stealthy DDoS threats.
-
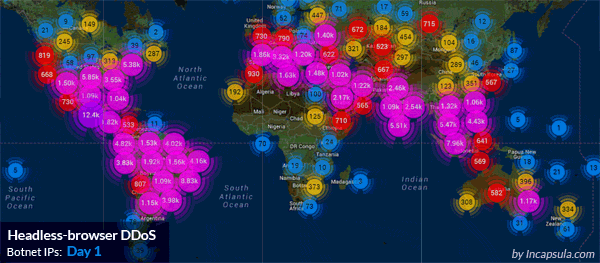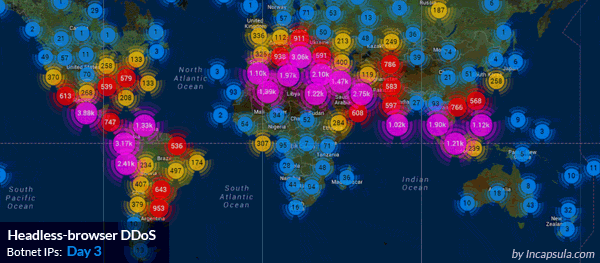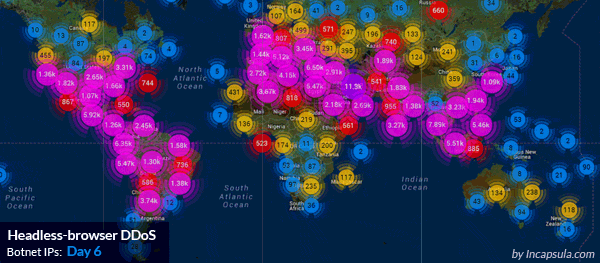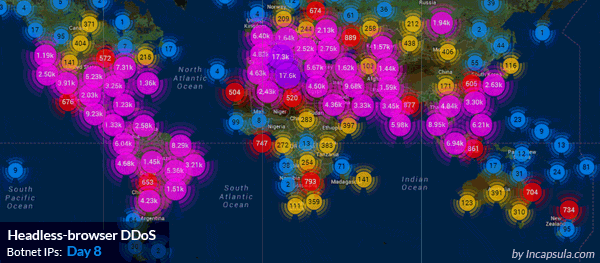
Imperva mitigates a massive HTTP flood: 690,000,000 DDoS requests from 180,000 botnets IPs.
The Continuing Threat of R.U.D.Y.
While R.U.D.Y. attacks have been around for over a decade, they remain a persistent threat to organizations. There are a few reasons for this:
- Source Code Leaks – The R.U.D.Y. source code has leaked online, allowing anyone to easily build their own attack tool.
- Growth of IoT Devices – The volume of insecure IoT devices provides an expanding pool of machines to compromise and launch attacks from.
- DDoS-as-a-Service – The emergence of DDoS booter/stresser services has put simple R.U.D.Y. attack tools in the hands of unskilled attackers.
- Cryptocurrency Mining – Threat actors are increasingly using DDoS extortion and ransom demands to mine cryptocurrency.
Conclusion
R.U.D.Y. and other low and slow attacks represent a serious threat to online services due to their stealthy and persistent nature that enables them to exhaust resources.
By leveraging traffic inspection, behavior analysis, and attack scrubbing techniques, organizations can secure their applications and infrastructure against these types of DDoS weapons even as they evolve. Due to the increasing availability of R.U.D.Y. and the growth of disruptive threat actors, vigilance and proactive measures are required to stay protected.













