What is a fork bomb?
A fork is a system call used in Unix and Linux systems that takes an existing process (a.k.a, a parent) and replicates it, forming a new process (a.k.a, a child). This allows both processes to carry out unique tasks simultaneously.
A fork bomb (also known as a “rabbit virus”) is a denial of service (DoS) attack in which the fork system call is recursively used until all system resources execute a command. The system eventually becomes overloaded and is unable to respond to any input.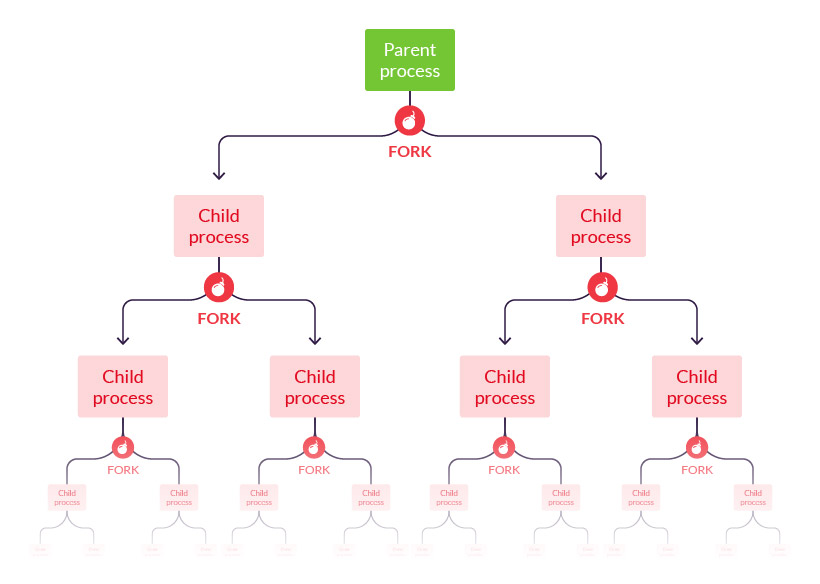 In contrast to most DoS assaults, which often occur by flooding network or computer resources externally, a fork bomb uses commands within the system it’s attempting to bring down. Sometimes it can even be self-inflicted.
In contrast to most DoS assaults, which often occur by flooding network or computer resources externally, a fork bomb uses commands within the system it’s attempting to bring down. Sometimes it can even be self-inflicted.
Attack description
In a fork bomb attack, self-replicating child processes consume system resources, blocking legitimate programs from running and preventing the creation of new processes. During an attack, keyboard inputs (e.g., logout attempts) are ignored, essentially locking the system.
Because a fork loop consumes CPU and memory, system resources are typically depleted long before an operating system reaches the maximum allowed processes. This results in “kernel panic”, i.e., the core operating system (the kernel) cannot cope and crashes.
For the majority of systems, a freeze lasts until a machine is restarted, and often a hard reboot is required to regain control. Data loss is highly likely. Some kernels might have pre-set limits that eventually allow an administrator access to the system
Vulnerable operating systems
All Unix, Linux, or Unix-like operating systems are potentially vulnerable to a fork bomb attack, including Ubuntu, Debian, Red Hat, or AIX.
Windows operating systems are not vulnerable to a traditional fork bomb attack, as they are unable to fork other processes. To create an attack similar to a fork bomb on Windows, a set of new processes needs to be rapidly created. This requires more complex programming than a traditional fork bomb.
Fork bomb examples
The following characters comprise a basic Linux shell script used to launch a fork bomb:
- :() – defines a function in Linux function, named :
- { } – encloses the commands that a function will run
- :|: – runs the command recursively, meaning the output is piped to another version of the command that runs in a subshell
- & – runs the preceding command in the background
- ; – separates the function defining command to the left from the next command
- : – runs the command, which is the newly created function – :
Executing the command creates a child process, which then repeats itself in an infinite loop. The result is a system that cannot respond, because all its resources are used creating these empty processes.
Code examples for fork bomb attacks in common programming languages include:
Example – Python Fork Bomb
#!/usr/bin/env python
import os
while True: os.fork()
Example – Java Fork Bomb
/** A basic forkbomb */
public class Bomb {
/** Utility class */
private Bomb() {}
/** CLI entry point
@param args CLI flags
*/
public static void main(final String[] args) throws IOException {
while (true) {
Runtime.getRuntime().exec(
String.format("javaw -cp %s us.yellosoft.forkbombs.Bomb", System.getProperty("java.class.path"))
);
}
}
}
Example – Ruby Fork Bomb
#!/usr/bin/env ruby
loop { fork { bomb } }
Example – C Fork Bomb
#include <unistd.h>
int main(void) {
for (;;) {
fork();
}
}
Mitigation methods
Preventing fork bombs is done by limiting the maximum number of processes a user can own. This is accomplished by:
- Using the Unix/Linux ulimit parameter to cap the number of processes a user can create. For example, ulimit=30 limits a user to owning 30 processes. However, the command is session-specific—the limit is reset after a session ends.
- Setting process limits across a system using the /etc/security/limits.conf file. This is the preferred method since the setting can be applied across all profiles, thus mitigating the risk in editing each user’s .profile settings.
It should be noted that even if the correct limits.conf setting is in place, a superuser and any process with administrative privileges can still initiate a fork bomb attack.
Even with modern operating systems, there is no perfect way to prevent a fork bomb. However, enforcing general security best practices and preventing untrusted software to run on root can block the vast majority of fork bomb attack scenarios.













