What Is the Meaning of Cryptojacking?
Cryptojacking is a threat that implants itself within a mobile device or computer and then employs measures to mine cryptocurrency. Cryptocurrency is virtual or digital money, which adopts the form of coins or tokens. The most prominent example is Bitcoin, however there are around 3,000 other types of cryptocurrency. While certain cryptocurrencies have moved into the physical world via credit cards and the like, the majority remain virtual.
Cryptocurrencies operate using a distributed database called a blockchain. The blockchain is updated regularly with information about the transactions that have occurred since the previous update. Every set of recent transactions is merged into a “block” as determined through a complex mathematical process.
For cryptocurrencies to be able to create new blocks, individuals need to provide computing power. Cryptocurrencies offer rewards to people who provide the required computer power. Individuals who provide computing resources in exchange for currency are known as cryptominers.
Larger cryptocurrencies typically make use of teams of miners who run dedicated computer rigs to carry out the required mathematical calculations. This process demands a significant amount of electricity—for instance, the Bitcoin network today uses over 73TWh of energy every year.
What Does Cryptojacking Malware Mean for Your Business?
Although malicious mining is less destructive than other cyber threats such as ransomware, this doesn’t mean that it is something to dismiss. Cryptojacking attacks might result in both indirect and direct losses for an organization. In the end, the targets are the ones who must pay for the computing power.
Besides a noticeable increase in electrical consumption, mining contributes to the aging of hardware by overworking processing cores, including cores belonging to discrete graphics cards, to enable malicious extraction of cryptocurrency. These costs are compounded because cryptojacking attacks tend to go undetected for several months, and it is often difficult to determine their true cost.
Research suggests that after maliciously mining cryptocurrency for two consecutive days using mobile mining malware, the batteries of the infected devices may begin to expand to the point where the affected phones are physically deformed.
This wasted bandwidth also decreases the efficiency and speed of genuine computing workloads. Many organizations have experienced the situation where computers stop because a program consumes all the available resources. Although there are several legitimate reasons for this, including resource-intensive background tasks or automatic updates, malicious mining should not be included.
When cryptojacking malware overwhelms a system, it can result in severe performance issues, which will have an immediate impact on your customers and end-users. If, for instance, a healthcare provider is the victim, staff could be unable to access critical patient health data. Attacks have also targeted essential infrastructure, such as a European water company.
Cryptojacking could at first appear to be a simple hack, but the cybercriminal who carries out such attacks may be more dangerous than an opportunistic parasite. As with ransomware, cryptojacking could be used as a decoy to detract attraction from more serious threats.
Attacks could also be combined with fake antivirus software to assail victims with ads stating that they must pay to have their devices cleaned. This is a troubling blend of ransomware and malicious mining. Attacks could appear to be financially motivated, but the true aim of using cyptojacking malware could be to overload infected systems and cause physical damage.
How Do Cryptojacking Attacks Work?
Hackers have two key strategies to get a target computer to secretly mine cryptocurrencies, and may use a combination of both strategies:
- Download – one way is to persuade victims to load cryptomining code onto their devices. This is achieved through social-engineering methods like phishing, where the victims get an email that looks legitimate and encourages them to activate a link. The link runs a malicious code, which adds the cryptomining script to the device. The script then runs in the background while the targeted individual works.
- Injection – the other strategy is to inject a script into an ad or website, which is distributed to multiple websites. Once the victim views the website or the infected ad appears on their browser, the script is executed automatically. The victim’s computer does not store any code. In both strategies, the code executes complex mathematical problems on the target computer and passes the results to a server controlled by the hacker.
- Hybrid – attackers may combine the two strategies to maximize their gains. For instance, out of hundreds of devices mining cryptocurrencies for an attacker, 10% could be receiving income from code on the target machines, while 90% do so via their web browsers.
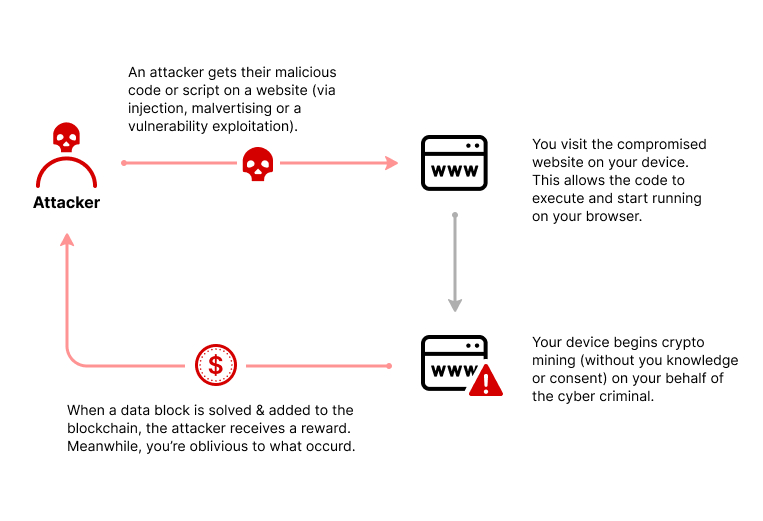
Browser-based cryptojacking
How do cryptominers spread?
Certain cryptomining scripts have worming abilities that let them infect other servers and devices on a target network. This also makes them difficult to isolate and remove—maintaining persistence on a network is in the best financial interest of a cryptojacker.
To maximize their capacity to spread across a network, cryptomining code could include multiple versions that leverage weaknesses in different network protocols. In some cases, the cryptomining code downloads multiple versions and tries to execute them, until one is successful.
Quick Cryptojacking Test: How to Detect Cryptojacking
Cryptojacking attempts are often masked as standard, normal behavior. This makes this malicious activity difficult to detect – but not impossible. Here are several methods you can use to detect cryptojacking:
- Decreased performance – cryptojacking causes decreased performance on computing devices. You should watch out for slower system performance, as well as devices that run slowly, crash, or exhibit unusually poor performance. Another indicator is a battery that drains more quickly than it usually would.
- Overheating cryptojacking – this term refers to a resource-intensive process that may cause a computing device to overheat. Overheating cryptojacking may cause damage to your computers or shorten the lifespan of the device. A fan that runs faster than usual may indicate that a cryptojacking website or script is overheating the device. The fan, in this scenario, is running excessively in order to prevent fire or melting.
- Central processing unit (CPU) usage – if you browse a site with little or no media content, an increase in CPU usage may indicate that there are cryptojacking scripts running. You can run a cryptojacking test by checking the central processing unit (CPU) usage of the device. You can check this by using either the Task Manager or Activity Monitor. However, this might not yield complete results, because processes can hide or mask themselves as something that looks legitimate. Additionally, a computer running at maximum capacity runs very slowly – this can make troubleshooting more difficult.
Cryptojacking Prevention: Tips and Tactics
Although it is hard to discover if your computer system has been compromised by crytojacking, there are some measures you can take to prevent these attacks and protect your networking systems and computer, as well as your crypto-assets:
- Instruct your IT team—IT staff should be trained to detect and understand cryptojacking. They must be aware of any initial signs of an attack and be prepared to respond immediately with a further investigation.
- Educate your employees—IT teams rely on employees informing them when computers are overheating or running slowly. Employees must have an understanding of cyber security and know to avoid clicking on links in emails that may contain cyptojacking code and only download from known links.
- Use anti-cryptomining extensions—cryptojacking scripts are generally deployed in web browsers. Use browser extensions, including No Coin, minerBlock, and Anti Minder, to block cryptominers across the web.
- Use ad-blockers—cryptojacking scripts are often embedded in web ads. Use an ad-blocker to block and detect malicious cyptomining code.
- Disable JavaScript—when surfing online, disable JavaScript to prevent cryptojacking code from infecting your organization’s computers. Remember that disabling JavaScript will also block some of the functions you require when browsing.
Imperva Cryptojacking Protection
Imperva provides its industry-leading Web Application Firewall, which can prevent cryptojacking and many other attacks with world-class analysis of web traffic to your applications.
Beyond Cryptojacking protection, Imperva provides comprehensive protection for applications, APIs, and microservices:
Runtime Application Self-Protection (RASP) – Real-time attack detection and prevention from your application runtime environment goes wherever your applications go. Stop external attacks and injections and reduce your vulnerability backlog.
API Security – Automated API protection ensures your API endpoints are protected as they are published, shielding your applications from exploitation.
Advanced Bot Protection – Prevent business logic attacks from all access points – websites, mobile apps, and APIs. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping.
DDoS Protection – Block attack traffic at the edge to ensure business continuity with guaranteed uptime and no performance impact. Secure your on-premises or cloud-based assets – whether you’re hosted in AWS, Microsoft Azure, or Google Public Cloud.
Attack Analytics – Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns.
Client-Side Protection – Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks.















