What Is Cobalt Strike?
Cobalt Strike is a cybersecurity tool designed for red teams and penetration testers to conduct advanced threat simulation and reconnaissance within network environments. Its extensive features enable users to emulate a full attack chain, similar to that of real-world adversaries, thereby helping organizations strengthen their defenses.
Developed as a commercial product to assist in security training and assessment, Cobalt Strike has gained popularity for its robust capabilities in simulating complex cyberattacks. Its ability to mimic the tactics, techniques, and procedures (TTPs) of advanced persistent threats (APTs) makes it a useful tool for testing and improving security measures.
While Cobalt Strike is a powerful tool in the hands of red teams and ethical hackers, it can become a major threat to organizations when in the hands of attackers. We’ll discuss the tool’s capabilities and how to defend organizations against malicious Cobalt Strike attacks.
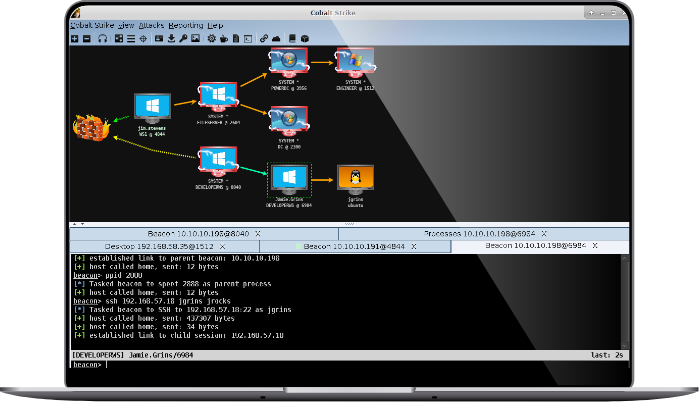
Cobalt Strike user interface (Source)
How Cobalt Strike Works: Key Features
Here are some of the main features and capabilities of Cobalt Strike.
Covert Communication
Cobalt Strike leverages covert communication channels to bypass network defenses and maintain access to compromised systems. It uses techniques like data exfiltration over DNS or HTTP(S) to simulate stealthy movements within a network.
This capability enables attackers to remain undetected while executing commands, moving laterally, and extracting information. It helps testers understand how malicious actors exploit communication mechanisms and for developing countermeasures against similar tactics.
Attack Packages
Attack packages in Cobalt Strike refer to custom payloads used to exploit vulnerabilities within a target network. These include spear-phishing campaigns, drive-by downloads, and the delivery of malware via social engineering tactics.
Each package can be tailored to fit a specific target environment, increasing the effectiveness of simulated attacks. This functionality aids in identifying how adversaries customize their payloads to breach networks, offering insights into strengthening an organization’s email and web defenses.
Beacon Configuration
Beacon is a central component of Cobalt Strike, acting as a backdoor for establishing persistence in a target network. It allows for the remote control of compromised systems, executing commands, and relaying information back to the attacker.
Configuring Beacon involves setting communication intervals, data exfiltration methods, and other operational parameters. This customizability is useful for mimicking varied attacker profiles and understanding how to detect and mitigate covert channels within a network.
Post-Exploitation Modules
Post-exploitation modules in Cobalt Strike, in particular the Empire payload which enables post-exploitation with Windows Powershell commands, provide a suite of tools for further exploitation after initial access. These include privilege escalation, lateral movement, and credential harvesting functionalities, simulating an attacker’s next steps within a penetrated network.
The modules offer insights into defending against further intrusion, emphasizing the importance of early detection and response to an initial breach. They inform the development of comprehensive security protocols that span prevention, detection, and remediation.
Command and Control (C2)
The command and control (C2) feature of Cobalt Strike is essential for managing compromised systems and conducting operations discreetly. It allows testers to establish a communication channel with the infected hosts, facilitating the execution of commands, exfiltration of data, and deployment of additional payloads.
This C2 capability is designed to mimic sophisticated threat actors, providing realistic simulations of how adversaries maintain control over breached networks. Cobalt Strike’s flexibility in C2 configurations enables it to mimic a variety of threat actor behaviors. This includes varying the frequency of communications, employing encryption to hide command and control traffic, and using domain fronting to mask the true destination of C2 communications.
Custom Scripts
Cobalt Strike supports the integration of custom scripts, enhancing its adaptability for various attack scenarios. These scripts can automate tasks, modify behaviors, and introduce new capabilities, aligning with specific objectives of a simulation.
The use of custom scripts provides flexibility in simulating complex threats and tailoring tests to an organization’s unique environment.
Why Is a Cobalt Strike Attack So Dangerous?
Cobalt Strike attacks, when carried out by malicious attackers, are particularly dangerous due to their sophistication, stealth, and the tool’s extensive capabilities in carrying out cyber threats:
- Sophisticated attack capabilities: The ability of Cobalt Strike to carry out the tactics, techniques, and procedures (TTPs) of advanced persistent threats (APTs) allows attackers to conduct highly targeted and complex operations. This level of sophistication makes it challenging for organizations to detect and respond to attacks before significant damage is done.
- Stealthiness: Cobalt Strike uses covert communication channels, such as beaconing and data exfiltration over DNS or HTTP(S). These techniques enable attackers to maintain a low profile, avoiding detection by traditional security measures. The stealthy nature of these communications means that breaches can go unnoticed for extended periods, allowing attackers to escalate privileges and move laterally with little resistance.
- Post-exploitation and C2: The tool’s post-exploitation modules and customizable command and control (C2) capabilities allows attackers to adapt their strategies to the specific environment they are targeting. This adaptability makes Cobalt Strike attacks highly effective, as they can bypass security defenses tailored to more generic threat profiles.
The combination of sophistication, stealth, and adaptability makes Cobalt Strike a formidable tool in the hands of malicious actors, posing a significant threat to organizations worldwide.
5 Ways to Protect Against a Cobalt Strike Attack
There are several measures that can help protect systems against the attacks enabled by Cobalt Strike.
1. Assess SSL/TLS Certificates
Inspecting SSL/TLS certificates can uncover anomalies indicative of malicious C2 traffic. Attackers often use forged or stolen certificates to mask their communications, making certificate analysis a key defense strategy. Regularly auditing certificates for irregularities helps identify potential breaches early.
2. Perform Network Monitoring and Anomaly Detection
Effective network monitoring combined with anomaly detection algorithms can identify unusual activities that may signal a Cobalt Strike attack. This includes spikes in data traffic, unexpected communication patterns, and unauthorized access attempts. Advanced monitoring tools and a keen understanding of normal network behavior are essential for early detection of threats.
3. Implement Network Segmentation and Access Control
Implementing network segmentation and strict access controls limits the movement of attackers within a network, even if they breach the perimeter defenses. By dividing the network into smaller, controlled segments, the impact of an attack can be contained. Access controls ensure that only authorized users can access sensitive areas of the network, hindering attackers’ attempts to escalate privileges and move laterally.
4. Conduct Threat Hunting
In the face of a potential Cobalt Strike attack, proactive threat hunting is imperative, because of the elusive and covert nature of the threat. Threat hunting involves actively looking for indicators of compromise that may elude traditional detection tools, focusing on identifying the tactics, techniques, and procedures (TTPs) associated with Cobalt Strike usage.
5. Consider Managed Detection and Response (MDR)
Managed detection and response (MDR) services provide continuous monitoring and expert analysis to identify and respond to threats quickly. MDR teams are equipped to recognize the subtle indicators of a Cobalt Strike attack and can provide rapid incident response. This external expertise supports internal security efforts when dealing with complex threats like Cobalt Strike.
Related content: Read our guide to penetration testing
Cobalt Strike Attack Prevention with Imperva
Imperva provides a Web Application Firewall, which can prevent attacks, including some types of malicious Cobalt Strike traffic, with world-class analysis of web traffic to your applications.
Imperva provides several other security features that can help detect and prevent elements of Cobalt Strike attacks:
Runtime Application Self-Protection (RASP) – Real-time attack detection and prevention from your application runtime environment goes wherever your applications go. Stop external attacks and injections and reduce your vulnerability backlog.
API Security – Automated API protection ensures your API endpoints are protected as they are published, shielding your applications from exploitation.
Advanced Bot Protection – Prevent business logic attacks from all access points – websites, mobile apps and APIs. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping.
DDoS Protection – Block attack traffic at the edge to ensure business continuity with guaranteed uptime and no performance impact. Secure your on premises or cloud-based assets – whether you’re hosted in AWS, Microsoft Azure, or Google Public Cloud.
Attack Analytics – Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns.
Client-Side Protection – Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks.















