What Is BGP?
Border Gateway Protocol (BGP) is the routing method that enables the Internet to function. Without it, it would not be possible to search on Google or send an email.
BGP is a routing protocol. Here is a simple definition of network routing from John F. Shoch, an American computer scientist who developed the predecessor to TCP/IP:
“The name of a resource indicates what we seek, an address indicates where it is, and a route tells us how to get there”.
The BGP protocol helps find the best route for network traffic seeking to reach an autonomous system (AS). An AS can be an Internet Service Provider or a large organization that controls a network prefix, representing a range of IP addresses. An autonomous system has a unique number called an ASN. BGP determines the best path to the ASN, depending on the topology of network nodes and current network conditions.
To use an analogy, an AS is like a city with many streets. A network prefix is one street, and an IP address is one particular house. Network packets are like cars traveling from one house to another, and BGP is like a navigation app that helps them take the best possible route.
A Brief History of Internet Traffic Routing
In the early days of the Internet, there were only a few networks connected to each other. As a result, routing between network nodes was quite static. All that needed to be done to set up routing was to define network nodes and make connections between them as needed.
However, the Internet grew quickly, adding more and more networks, which necessitated a more dynamic routing system. EGP (External Gateway Protocol) was invented to do the job.
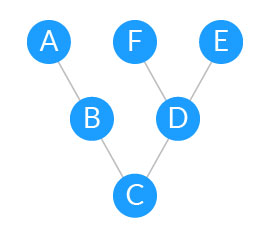
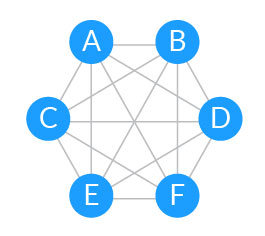
EGP is a simple routing protocol based on tree-like hierarchical topologies. In modern networks, tree topologies have become fully connected mesh topologies to allow for maximum scalability.
Tree-like vs. full mesh topologies
 |
 |
|
| In a tree-like topology, to reach E or F, A will have to go through B, C and D. | In a full mesh topology, nodes have many paths to reach each other. |
The Need for BGP
As the Internet continued to expand, it became increasingly difficult to keep track of all the routes from one network to another. The solution was to transition to an Autonomous System (AS) architecture.
An AS can be an Internet Service Provider, a university or an entire corporate network, including multiple locations (IP addresses). Each AS is represented by a unique number called an ASN. Each AS controls a collection of connected routing prefixes, representing a range of IP addresses. When traffic reaches the ASN, it determines the routing policy inside the network.
As the number of autonomous systems on the internet grew, the drawbacks of EGP became more pronounced. Its hierarchical structure hampered scalability and made it difficult to connect new networks in an efficient manner. It was necessary to define an exterior routing protocol that is more scalable and provides more advanced capabilities.
This new protocol, known as the Border Gateway Protocol, was formalized in 1989.
BGP Technical Deep Dive
BGP is designed to exchange routing and reachability information between autonomous systems on the Internet.
Each BGP speaker, which is called a “peer”, exchanges routing information with its neighboring peers in the form of network prefix announcements. This way, an AS doesn’t need to be connected to another AS to know its network prefix.
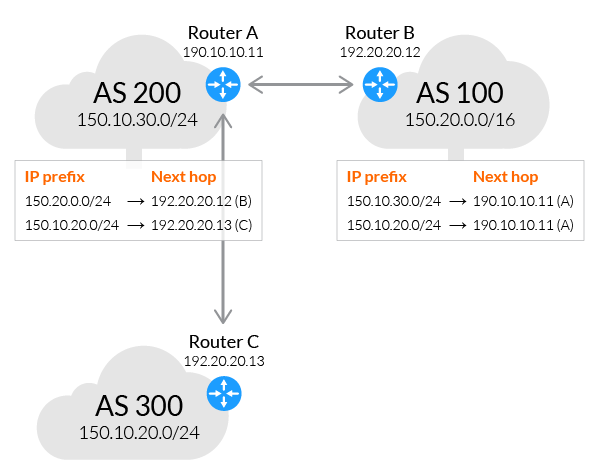
The BGP decision-making mechanism analyzes all the data and sets one of its peers as the next stop, to forward packets for a certain destination.
Each peer manages a table with all the routes it knows for each network and propagates that information to its neighboring autonomous systems.
In this way, BGP allows an AS to collect all the routing information from its neighboring autonomous systems and “advertise” that information further. Each peer transfers the information internally inside its own autonomous system.
Just like in real life, usually more than one route exists to reach a given destination. BGP is responsible for determining the most suitable route according to the information collected and an organization’s routing policy, which is based on cost, reliability, speed, and other factors.
Imperva DDoS Protection
BGP rerouting can enable powerful protection against distributed denial of service (DDoS) attaks. BGP rerouting can mitigate direct-to-origin DDoS attacks by screening all incoming network traffic before it reaches its target. It functions at the network level by rerouting malicious network packets to security providers before they can reach DNS servers or other computing resources.
BGP routers can redirect high volumes of traffic to centralized data scrubbing centers used by a security provider. The scrubbing center analyzes traffic and filters out malicious DDoS attack traffic using deep packet inspection. It then allows healthy traffic to pass through to the AS.
Imperva’s DDoS Protection solution is based on BGP routing. It blocks attack traffic at the edge to ensure business continuity with guaranteed uptime and no performance impact. Secure your on premises or cloud-based assets – whether you’re hosted in AWS, Microsoft Azure, or Google Public Cloud.
In addition, Imperva provides comprehensive protection for applications, APIs, and microservices:
Web Application Firewall – Prevent attacks with world-class analysis of web traffic to your applications.
Runtime Application Self-Protection (RASP) – Real-time attack detection and prevention from your application runtime environment goes wherever your applications go. Stop external attacks and injections and reduce your vulnerability backlog.
API Security – Automated API protection ensures your API endpoints are protected as they are published, shielding your applications from exploitation.
Advanced Bot Protection – Prevent business logic attacks from all access points – websites, mobile apps and APIs. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping.
Attack Analytics – Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns.



