Distributed Denial of Service Attack (DDoS) Definition
A distributed denial of service (DDoS) attack is a malicious attempt to make an online service unavailable to users, usually by temporarily interrupting or suspending the services of its hosting server.
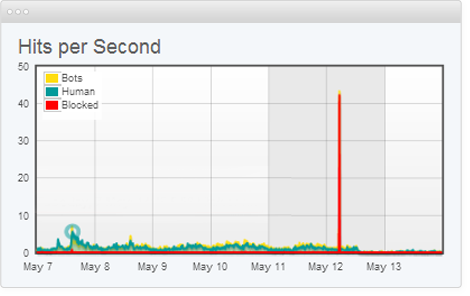
A DDoS attack is launched from numerous compromised devices, often distributed globally in what is referred to as a botnet. It is distinct from other denial of service (DoS) attacks in that it uses a single Internet-connected device (one network connection) to flood a target with malicious traffic. This nuance is the main reason for the existence of these two somewhat different definitions.
This is part of an extensive series of guides about network security
“And that concludes our DDoS party: Escapist Magazine, Eve Online, Minecraft, League of Legends + 8 phone requests.” Tweeted by LulzSec – June 14, 2011, 11:07PM
Broadly speaking, DoS and DDoS attacks can be divided into three types:
Volume Based Attacks
Includes UDP floods, ICMP floods, and other spoofed-packet floods. The attack’s goal is to saturate the bandwidth of the attacked site, and magnitude is measured in bits per second (Bps).
Protocol Attacks
Includes SYN floods, fragmented packet attacks, Ping of Death, Smurf DDoS, and more. This type of attack consumes actual server resources, or those of intermediate communication equipment, such as firewalls and load balancers, and is measured in packets per second (Pps).
Application Layer Attacks
Includes low-and-slow attacks, GET/POST floods, attacks that target Apache, Windows, or OpenBSD vulnerabilities, and more. Comprised of seemingly legitimate and innocent requests, these attacks aim to crash the web server, and the magnitude is measured in Requests per second (Rps).
Common DDoS Attack Types
While a DDoS attack intends to disrupt some or all of its target’s services, not all DDoS attacks are the same. They feature unique characteristics, methods, and attack vectors. There are three common types of DDoS attacks:
- Volumetric (Gbps)
- Protocol (pps)
- Application layer (rps) attacks.
Since these three are categorized as DDoS attacks, the terms are often confused or used interchangeably by accident. Complicating matters, there are times when these types of DDoS attacks overlap during a single attack to generate greater impact.
Attackers don’t make clean distinctions between these three types of DDoS attacks. Their goal is to disrupt your business. When attacking their target, they’ll combine volumetric, protocol, and application layer attacks into a multi-vector attack. Multi-vector attacks hit the target in varying forms and disrupt the processes at a higher level.
What is a Gbps or Volumetric DDoS Attack
A volumetric DDoS attack is what most people associate with the term “DDoS” because it is the most common. The first volumetric DDoS attack made headlines in the late 1990s and has since spawned an army of copycats.
Volumetric attacks can also be called “floods” because an attack floods a target’s server with requests, like unwanted pings. Attacks are measured in bits per second (bps) or Gigabits per second (Gbps).
The concept of a volumetric attack is simple: send as much traffic as possible to a site to overwhelm the server’s bandwidth. Volumetric attacks are typically produced using amplification techniques. DNS amplification is one of the more common techniques attackers use to carry out a volumetric attack. The bad actor sends small DNS requests with the victim’s spoofed source IP address to a DNS server. When the server receives the request, it responds to the victim with a large response.
Attackers also create volumetric attacks using botnets made up of exploited IoT devices. Connected devices usually lack basic security defenses, but because they’re connected to the Internet and can execute code, they can be easily exploited.
The proliferation of cheap IoT devices like toys, small appliances, thermostats, security cameras, and Wi-Fi routers makes it easy to launch an effective attack with just a few clicks. A hacker can easily leverage the extensibility of the internet to launch a successful volumetric DDoS attack with few resources.
The Mirai botnet is an example of the devastation of leveraged, unsecured IoT devices. Mirai targeted IoT devices, using each infected device to join a volumetric DDoS attack. It resulted in successful attacks against some of the world’s largest organizations.
What is a PPS or Network Protocol DDoS Attack?
An internet protocol is a discrete set of rules for exchanging information across the internet. TCP/IP is one of the most well-known rules for exchanging requests and data. A bad actor can severely disrupt an online service by exploiting these rules.
Protocol attacks often work at layers 3 and 4 of the OSI model on network devices like routers. Because they are on the network layer, they are measured in packets per second (pps).
Below is a sampling of different network-layer DDoS attack types:
- UDP floods
- SYN floods
- NTP amplification
- DNS amplification
- SSDP amplification
- IP fragmentation
- SYN-ACK floods
Examples of a Network Protocol DDoS Attack
- The ping of death (POD) is an IP fragmentation attack that exploits the inherent size limitation of a packet. By manipulating parts of the packet or fragments, the exploit can overflow the memory buffers allocated to that packet and then deny service to legitimate packets.
- A TCP SYN flood is another common protocol attack. Here, a surge of TCP SYN requests directed towards a target overwhelms the target and makes it unresponsive.
What is an RPS or Application Layer DDoS Attack
While volumetric attacks and — to a lesser extent — protocol attacks compromise a service with the sheer number of requests, application layer attacks, or layer 7 attacks, target an edge server that executes a web application.
These threats are harder to detect because attackers usually make requests like legitimate users. Consequently, these attacks often show up as smaller traffic spikes and do not require the assistance of a botnet.
Application layer attacks are measured in requests per second (RPS) — the number of requests an application makes. An application layer attack is considered a resource-based attack; therefore, it takes fewer requests to bring down an application because the attack is focused on overwhelming the CPU and memory.
An application layer attack typically includes hitting the web server, running PHP scripts, and contacting the database to load web pages. A single HTTP request, which is simple to execute on the client side, can cause a server to execute many internal requests and load numerous files to fulfill the request, which slows the system.
An application layer attack can also be a multi-vector attack that uses a combination of volumetric and protocol attacks to increase the likelihood of taking a service offline. Because of their complexity and effectiveness, multi-vector attacks are increasingly popular among cybercriminal groups.
| DDoS Attack Type | Metric | Category | Characteristics | Examples | Mitigation |
| Volumetric Attack | Bits per second (bps), Gigabits per second (Gbps), flood | Connectionless | High volume, using bots | UDP flood | Volumetric attacks are absorbed in a global network of scrubbing centers that scale on demand to counter multi-gigabyte DDoS attacks. |
| Protocol Attack | Packets per second (PPS) | Connection-based | Attacks the network layer | Syn flood, ping of death | This type of attack is mitigated by blocking “bad” traffic before it reaches the site. Uses visitor identification technology to differentiate legitimate website visitors (humans, search engines) and automated or malicious clients. |
| Application layer attack | Requests per second (RPS), low-rate | Connection-based | Difficult to detect | SQL injection, XSS | Application layer attacks are blocked by monitoring visitor behavior, blocking known bad bots, and challenging suspicious or unrecognized entities with JS test, cookie challenge, and even CAPTCHAs. |
The Motivation Behind DDoS Attacks
DDoS attacks are quickly becoming the most prevalent type of cyber threat, growing rapidly in the past year in both number and volume, according to recent market research. The trend is towards shorter attack duration but bigger packet-per-second attack volume.
Attackers are primarily motivated by:
- Ideology – So-called “hacktivists” use DDoS attacks to target websites they disagree with ideologically.
- Business feuds – Businesses can use DDoS attacks to strategically take down competitor websites, e.g., to keep them from participating in a significant event, such as Cyber Monday.
- Boredom – Cyber vandals, a.k.a. “script-kiddies,” use prewritten scripts to launch DDoS attacks. The perpetrators of these attacks are typically bored, would-be hackers looking for an adrenaline rush.
- Extortion – Perpetrators use DDoS attacks, or the threat of DDoS attacks, to extort money from their targets.
- Cyber warfare – Government-authorized DDoS attacks can be used to both cripple opposition websites and an enemy country’s infrastructure.
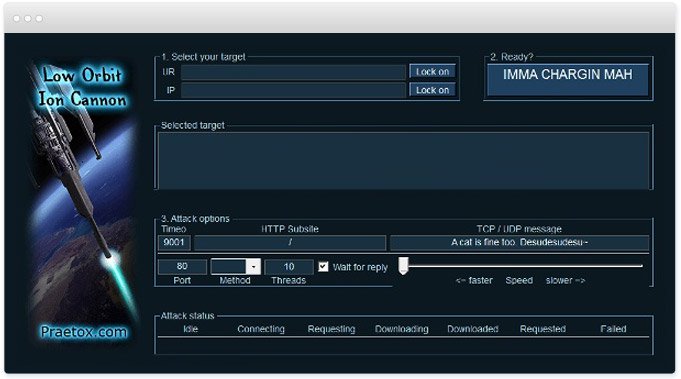 LOIC (Low Orbit Ion Cannon): an “entry-level” DoS attack tool used for cyber vandalism
LOIC (Low Orbit Ion Cannon): an “entry-level” DoS attack tool used for cyber vandalism
Imperva solutions mitigate DDoS damage
Imperva seamlessly and comprehensively protects websites against all three types of DDoS attacks, addressing each with a unique toolset and defense strategy:
Volume Based Attacks
Imperva counters these attacks by absorbing them with a global network of scrubbing centers that scale, on-demand, to counter multi-gigabyte DDoS attacks.
Protocol Attacks
Imperva mitigates this type of attack by blocking “bad” traffic before it even reaches the site, leveraging visitor identification technology that differentiates between legitimate website visitors (humans, search engines, etc.) and automated or malicious clients.
Application Layer Attacks
Imperva mitigates Application Layer attacks by monitoring visitor behavior, blocking known bad bots, and challenging suspicious or unrecognized entities with JS tests, Cookie challenges, and even CAPTCHAs.
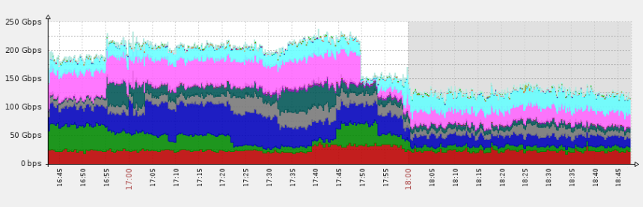
Imperva mitigates a 250GBps DDoS attack—one of the Internet’s largest.
In all these scenarios, Imperva applies its DDoS protection solutions outside your network, meaning only filtered traffic reaches your hosts. Moreover, Imperva maintains an extensive DDoS threat knowledge base, which includes new and emerging attack methods. This constantly updated information is aggregated across our entire network – identifying new threats as they emerge, detecting known malicious users, and applying remedies in real time across all Imperva-protected websites.
See Additional Guides on Key Network Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of network security.
Microsegmentation
Authored by Tigera
- What is Microsegmentation? The Basics and Key Best Practices
- Application Segmentation: The Engine Behind Zero Trust
- Microsegmentation Security: The Evolution of Cybersecurity
SIEM
Authored by Exabeam
- What Is SIEM? Uses, Components, and Capabilities
- SIEM Log Management: The Complete Guide
- SIEM Architecture: Technology, Process and Data
AWS Security
Authored by NetApp














