What Is a Vishing Attack?
Vishing, also known as voice phishing, is a cybercrime whereby attackers use the phone to steal personal information from their targets. In a vishing attack, cybercriminals use social engineering tactics to persuade victims to provide personal information, typically with the goal of accessing financial accounts.
Like traditional phishing (based on email messages) or smishing (based on text messages), with vishing, the attacker must convince the victim that they are doing the right thing by cooperating with the cybercriminal. The attacker might pretend to represent the police, government, tax department, bank, or the victim’s employer.
The following image shows an example of a vishing attack. It illustrates how an attacker can obtain a bank customer’s details, contact them over the phone, and convince them to transfer funds.
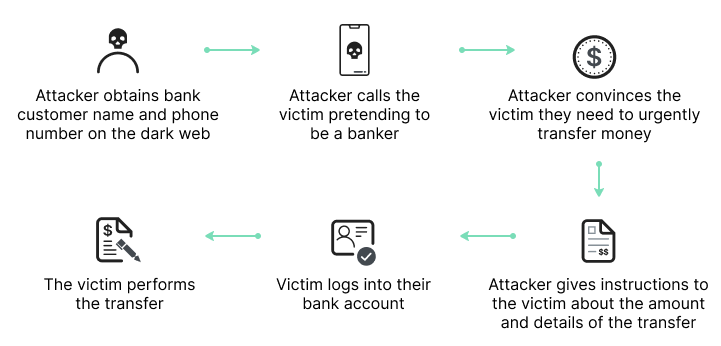
Cybercriminals use persuasive language and threats to make the victim believe they have no other option than to hand over the requested details. Certain cybercriminals use forceful language, others suggest helping the victim avoid criminal charges, and others pretend to be IT staff conducting maintenance on a user’s device. Another tactic cybercriminals use to leave voicemails telling the victim that if they don’t call back, they risk serious consequences.
The most effective way to prevent vishing is to invest in security awareness, training employees to recognize vishing schemes and avoid cooperating with the attackers.
Vishing vs Phishing: What Is the Difference?
Vishing and phishing have the same aim: to gain sensitive information from users that cybercriminals can use for monetary gain, identity theft, or account takeover. The major difference between vishing and phishing attacks is the methods attackers employ to target victims: phishing is mainly an email-based attack, whereas vishing uses a phone line.
Usually, both phishers and vishers bombard their targets with large volumes of messages. A phishing attacker might send a high volume of emails to a list of possible targets. Attackers who decide to target a particular organization might target email addresses belonging to high-privileged users from that organization.
Phishers tend to use compelling messages to persuade users to reply with sensitive data or to convince them to click a link connected to malware. Some phishing attackers will use malicious attachments.
A visher could first send a high volume of text messages to possible victims from a list of phone numbers. The message might prompt the victim to call the cybercriminal’s phone. Alternatively, visher attackers could create an automated message that robo-calls possible victims. This method relies on computer-generated voice messages, removing accents and establishing trust.
The attacker then tricks victims into following the instructions in the voice message, which connects them to a human agent. The agent might continue the scam or direct users to set up a website that the attacker controls.
Individuals who know about phishing might not know about vishing, so by employing this newer technique, cyber criminals increase their chances of success.
Vishing Attack Examples
Most incidents of fraud in the US involve telephone-based communication. Here are some examples of common vishing attacks:
Banking Scams
Vishing attackers attempt to steal financial information such as bank account and credit card numbers. One method they use to trick their victims is ID spoofing, where they impersonate a legitimate entity using an ID that looks authentic. For example, a scammer might pose as a CFO or employee in the financial department and try to persuade the target to transfer funds to an offshore account.
Unsolicited Investment and Loan Offers
Scammers often call their targets offering unrealistically enticing deals, such as quick fixes to pay off debts or get-rich-quick schemes. These offers tend to require immediate action accompanied by a fee. A legitimate lender or investor does not initiate unsolicited contact or make overly optimistic offers.
Social Security and Medicare Scams
Phone calls are the preferred method for scamming older targets. Scammers often pose as representatives from Medicare or the Social Security Administration. They may try to steal personal information such as Medicare or Social Security numbers or threaten to suspend or stop benefits. Scammers can use the stolen information to steal money or redirect benefits.
Tax Scams
Scammers often send a prerecorded message, ostensibly from the IRS, informing victims of a supposed issue with their tax returns. Spoofed caller IDs often make it look like the call is from the IRS.
Vishing Prevention
Cybersecurity Awareness
You should include the following points your cybersecurity awareness training:
- Never reveal personal data—vishing attacks are designed to trick the target into revealing personal information, which attackers can use for other attacks or fraud. Never give a multi-factor authentication (MFA) number, password, financial data, or similar details over the phone.
- Always check phone numbers—vishers may call you posing as representatives of a legitimate organization. Before you provide any personal information or follow a caller’s instructions, get their name and make sure you can contact them through an official company number. If the caller attempts to dissuade you from doing this, it’s likely a scam.
- Organizations do not accept payment via prepaid or gift cards—vishers often ask for payment for amounts the victim supposedly owes in the form of prepaid cards or gift cards. No legitimate organization will request a prepaid credit or gift card as payment.
- Never give remote computer access—vishers could request remote access to your computer under the guise of removing malware or fixing some issue. You should never grant anyone access to your computer, unless they are a verified member of an IT department.
- Report suspicious incidents—vishers typically repeat the same scam on several targets. Report suspected vishing attacks to authorities or security staff at your organization, ensuring they can protect other targets.
Mitigating Additional Attack Vectors
Unlike phishing, vishing is hard to stop using technology. Because vishing takes place over the phone, an organization would need to eavesdrop on all phone calls and find warning signs to detect an attack.
Due to this, organizations should build a threat model and focus on the attacker’s objectives when preventing vishing attacks. For example, a vishing attack targeting an organization may have one of several goals:
- Infecting an employee’s computer with malware
- Compromising an employee’s access credentials
- Gaining access or control over a user’s device
By isolating each of these threat scenarios, the organization can implement solutions that stop attackers in later stages of the attack—even if the initial vishing call remains undetectable.
Vishing Prevention with Imperva
Imperva provides a Web Application Firewall, which prevents attacks with world-class analysis of web traffic to your applications. A WAF can detect and mitigate unauthorized access, for example using credentials obtained by vishing, using device threat intelligence.
In addition to account takeover protection, Imperva provides comprehensive protection for applications, APIs, and microservices:
Runtime Application Self-Protection (RASP) – Real-time attack detection and prevention from your application runtime environment goes wherever your applications go. Stop external attacks and injections and reduce your vulnerability backlog.
API Security – Automated API protection ensures your API endpoints are protected as they are published, shielding your applications from exploitation.
Advanced Bot Protection – Prevent business logic attacks from all access points – websites, mobile apps and APIs. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping.
DDoS Protection – Block attack traffic at the edge to ensure business continuity with guaranteed uptime and no performance impact. Secure your on premises or cloud-based assets – whether you’re hosted in AWS, Microsoft Azure, or Google Public Cloud.
Attack Analytics – Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns.
Client-Side Protection – Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks.













