What is Bot Management?
Bot management is a strategy that enables you to filter which bots are allowed to access your web assets. With this strategy, you can allow useful bots, such as Google crawlers, while blocking malicious or unwanted bots, such as those used for cyberattacks. Bot management strategies are designed to detect bot activity, identify the bot’s source, and determine the nature of the activity.
Bot management is necessary to prevent performance and security impacts on your site. If malicious bots are allowed to access your assets, they can overload servers and cause legitimate users to be denied or slowed. Additionally, some bots are used to scrape your content and can be used to steal proprietary assets, credentials, or system files. These items can then be used to phish users, spam content, or plan cyber attacks.
At the same time, bot management systems that are too strict or falsely recognize bad bots can cause serious damage to an organization’s business. For example, blocking search engine bots can lead to loss of traffic, conversions, and revenues, and blocking home-grown bots used for testing and automation can disrupt important business activities.
Bot management uses a range of security, machine learning, and web development technologies to accurately assess bots and block malicious activity while allowing legitimate bots to operate uninterrupted.
These technologies include bot pattern databases, user behavioral analytics (UBA), and Web Application Firewalls (WAF) that can intercept network traffic and block unwanted activity based on real-time analysis or business rules.
How Does Bot Management Work?
Bot management techniques have evolved to match the capabilities and uses of bots by attackers. Modern bot management faces a dual challenge: to identify attacker bots which are increasingly sophisticated at emulating human users and to distinguish malicious bots from legitimate bots, which can be very important for an organization’s day to day operations.
Currently, three main approaches are used to detect and manage bots.
- Static approach—uses static analysis tools to identify header information and web requests known to correlate with bad bots. This technique is passive and can only detect known and active bots.
- Challenge-based approach—uses active challenges or tests that are difficult or impossible for bots to perform to identify bots. Commonly used challenges include CAPTCHA verification, the ability to run JavaScript, of the acceptance of cookies.
- Behavioral approach—evaluates the activity of potential users and matches that activity against known patterns to verify user identity. This technique uses several profiles to classify activity and distinguish between human users, good bots, and bad bots.
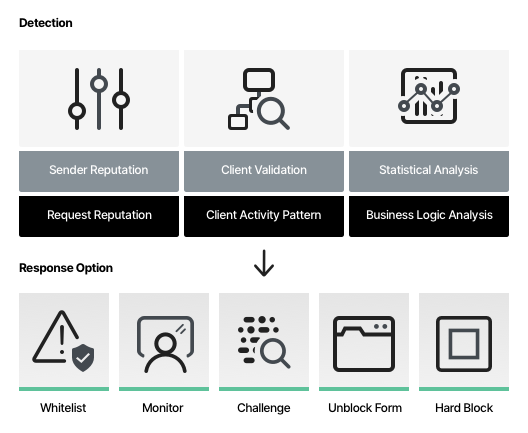
Bot management approaches
The most effective bot management strategies combine all three techniques to ensure that the largest possible number of bots is identified. By combining techniques, you increase your chances of identifying bots even if they are recently created or have dynamic behaviors.
In addition to the self-management of bots, there are also bot mitigation services you can use. These services use automated tools to apply the above techniques and identify bots. Services typically monitor your API traffic and implement rate-limiting to prevent API abuse. This rate-limiting enables services to restrict bots across your entire landscape rather than focusing on a single IP.
Why is Bot Management Important? Risks of Exposure to Malicious Bots
Prioritizing bot management as part of your security and operations processes is recommended for every organization. The impacts of bots can range from mild inconvenience to significant revenue loss and there is no reason to take a risk you don’t have to. Below are a few of the risks bot management can help you avoid.
Distributed denial-of-service (DDoS) attacks
DDoS attacks are attacks that use networks of bots or compromised devices to spam servers with requests and overwhelm bandwidth and processing resources. This can make sites, applications, or services unavailable. These attacks can use individual computers or Internet of things (IoT) devices. IoT devices are being used increasingly because of the sheer number of devices and their tendency to be less secure than workstations or other computers.
Credential stuffing
Credential stuffing is an attack where criminals use bots to automatically try lists of leaked or stolen credentials until one is accepted. These attacks enable attackers to brute force access to systems and take over user accounts. These attacks are frequently successful because users tend to use the same credentials for multiple accounts.
Gift and credit card fraud
Attackers can use bots to brute force their way into gift card creation accounts. Once in, they can create counterfeit cards and use those cards in exchange for cash value. Alternatively, attackers can use bots to test stolen credit card information with small purchases that are unlikely to be noticed. If credit cards are found to be valid, attackers can then use them for larger purchases.
Intelligence harvesting
Attackers can use bots to crawl or scan web sites, social media, or forums to find personal information about users. Attackers can then use this information to perform phishing attacks, using personal information to appear like an authority and tricking users into giving up confidential information.
Web scraping protected content
Web scraping attacks use bots to crawl scan and extract proprietary assets from sites or storage resources. These assets can include pricing data, logos or branding materials, product information, or hidden files. eCommerce websites and portals are particularly vulnerable to web scraping, including sites for ticketing, airlines, and online gaming.
Imperva Bot Management
Imperva’s bot management solution uses all three approaches covered above—static, challenge-based, and behavior-based—to investigate each visitor on your site, whether human or not, and match it with a behavioral ID. It can effectively protect against malicious bots while ensuring that legitimate bots and human users have uninterrupted access to your site.
In addition to helping mitigate bad bot activity, Imperva provides multi-layered protection to make sure websites and applications are available, easily accessible, and safe. The Imperva application security solution includes:
- DDoS Protection—maintain uptime in all situations. Prevent any type of DDoS attack, of any size, from preventing access to your website and network infrastructure.
- CDN—enhance website performance and reduce bandwidth costs with a CDN designed for developers. Cache static resources at the edge while accelerating APIs and dynamic websites.
- Cloud WAF—permit legitimate traffic and prevent bad traffic. Safeguard your applications at the edge with an enterprise‑class cloud WAF.
- Gateway WAF—keep applications and APIs inside your network safe with Imperva Gateway WAF.
- RASP—keep your applications safe from within against known and zero‑day attacks. Fast and accurate protection with no signature or learning mode.














