What is a backdoor
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
Backdoor installation is achieved by taking advantage of vulnerable components in a web application. Once installed, detection is difficult as files tend to be highly obfuscated.
Webserver backdoors are used for a number of malicious activities, including:
- Data theft
- Website defacing
- Server hijacking
- The launching of distributed denial of service (DDoS) attacks
- Infecting website visitors (watering hole attacks)
- Advanced persistent threat (APT) assaults
Backdoor trojan installation
The most prevalent backdoor installation method involves remote file inclusion (RFI), an attack vector that exploits vulnerabilities within applications that dynamically reference external scripts. In an RFI scenario, the referencing function is tricked into downloading a backdoor trojan from a remote host.
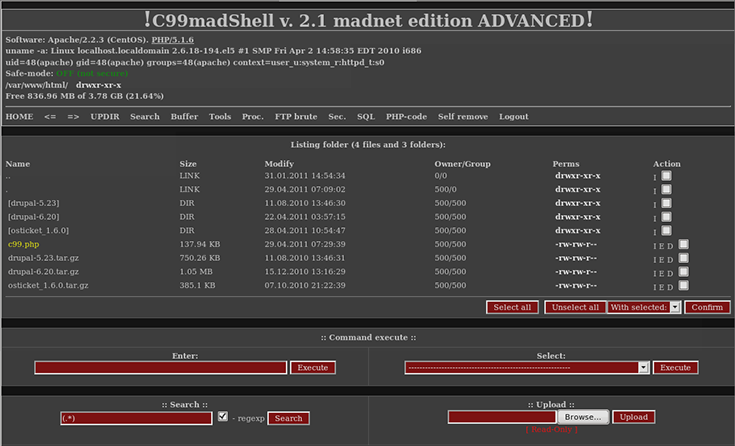
Example of a backdoor dashboard with command execute capabilities.
Perpetrators typically identify targets using scanners, which locate websites having unpatched or outdated components that enable file injection. A successful scanner then abuses the vulnerability to install the backdoor on the underlying server. Once installed, it can be accessed at any time, even if the vulnerability enabling its injection has since been patched.
Backdoor trojan injection is often done in a two-step process to bypass security rules preventing the upload of files above a certain size. The first phase involves installation of a dropper—a small file whose sole function is to retrieve a bigger file from a remote location. It initiates the second phase—the downloading and installation of the backdoor script on the server.
The challenge of backdoor shell removal
Once installed, backdoors are very hard to weed out. Traditionally, detection involves using software scanners to search for known malware signatures in a server file system. This process is error prone, however. Backdoor shell files are almost always masked through the use of alias names and—more significantly—code obfuscation (sometimes even multiple layers of encryption).
Detection is further complicated since many applications are built on external frameworks that use third-party plugins; these are sometimes laden with vulnerabilities or built-in backdoors. Scanners that rely on heuristic and signature-based rules might not be able to detect hidden code in such frameworks.
Even if a backdoor is detected, typical mitigation methods (or even a system reinstallation) are unlikely to remove it from an application. This is particularly true for backdoors having a persistent presence in rewritable memory.
Mitigating backdoor shell attacks with Imperva
At Imperva, we use a combination of methods to prevent backdoor installation, as well as to detect and quarantine existing backdoor shells.
On one hand, the Imperva cloud web application firewall (WAF) uses a combination of default and user-defined security rules to prevent RFI attacks from compromising your application. The WAF is deployed as a secure proxy at the edge of your network, ensuring that malicious requests are blocked before they’re able to interact with your application. As a result, your site is secured from the moment you onboard our service.
If your webserver was already compromised before onboarding, the Imperva backdoor protection solution lets you detect and remove shells from your file system.
The solution takes the novel approach of intercepting connection requests to malicious shells—a preferable alternative to scanning a server for backdoor files. Unlike backdoor files, which are easily hidden, connection requests cannot be obfuscated to hide their malicious intent.
https://youtu.be/fnVCUDitolY
By tracing back such communication attempts, the Imperva cloud service can identify any backdoor shell, even if its source code was encrypted to avoid scanners.













