What is ISO/IEC 27001
ISO/IEC 27001, also known as ISO 27001, is a security standard that outlines the suggested requirements for building, monitoring and improving an information security management system (ISMS). An ISMS is a set of policies for protecting and managing an enterprise’s sensitive information, e.g., financial data, intellectual property, customer details and employee records.
ISO 27001 is a voluntary standard employed by service providers to secure customer information. It requires an independent and accredited body to formally audit an organization to ensure compliance.
The benefits of working with an ISO 27001 certified service provider include:
- Risk management – An ISMS helps govern who within an organization can access specific information, reducing the risk that said information can be stolen or otherwise compromised.
- Information security – An ISMS contains information management protocols detailing how specific data needs to be handled and transmitted.
- Business continuity – To remain ISO 27001 compliant, a service provider’s ISMS must be continuously tested and improved upon. This helps prevent data breaches that could impact your core business functions.
For service providers, compliance provides peace of mind to your customers, while allowing you to maintain due diligence regarding data security.
ISO compliance and information security governance
ISO 27001 compliance can play an integral role in creating an information security governance policy-the plans, tools and business practices used by an enterprise to secure their sensitive data.
Creating an ISO compliant ISMS is a comprehensive process that includes scoping, planning, training and support. Below are some of the most important elements to be addressed before an enterprise can become certified.
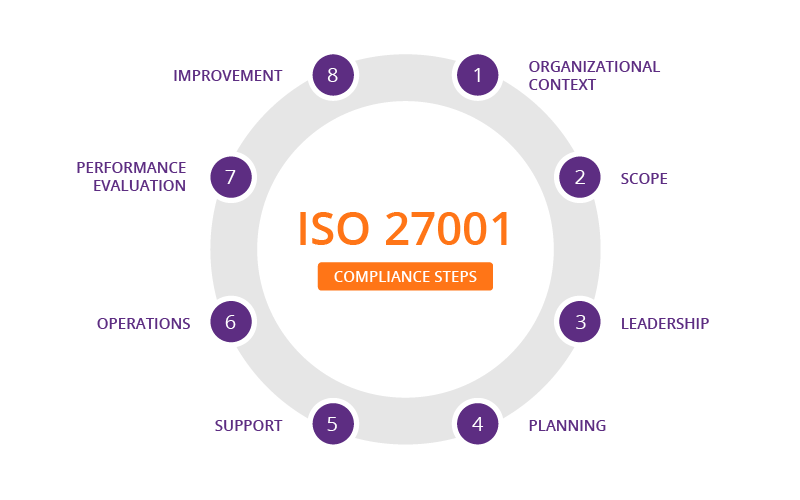
1. Organizational context
Internal and external issues that can affect an enterprise’s ability to build an ISMS, e.g., information security, as well as legal, regulatory and contractual obligations, need to be identified.
2. Scope
The information defined in step one is then used to document the scope of the ISMS, outlining relevant areas, as well as boundaries. The ISMS than needs to be implemented, maintained and continually improved according to specific information security risks and ISO 27001 requirements.
The scope emphasizes the importance of integrating the ISMS as part of an overall management structure and process. Requirements apply to all organizations, regardless of type, size or industry.
3. Leadership
The enterprise’s management needs the necessary leadership skills to maintain the ISMS. This includes:
- Creating an information security policy in line with the strategic direction of the organization.
- Integrating the ISMS into standard organization processes.
- Communicating the details of the information security policy and highlighting the importance of ISMS requirements.
- Promoting the continual improvement to the ISMS.
- Ensuring adequate support for staff who work to improve the system.
4. Planning
A plan for addressing information security risks needs to be integrated into the ISMS process. This involves:
- Establishing and applying a detailed information security risk management process that includes risk criteria, the identification of information security threats, risk analysis and the evaluation of risks relative to the established criteria.
- Defining and applying a process for mitigating threats that includes controls needed to implement each risk treatment option.
5. Support
The enterprise needs to obtain the resources, people, and infrastructure to effectively implement an ISMS.
Support involves training and mentoring staff to deal with sensitive information. Additionally, employees need to be informed as to how they can contribute to the effectiveness of the ISMS and the implications of not conforming to information security policies.
Lastly, internal and external communication policies relevant to the ISMS need to be established. Policies should include the definition of issues that need to be communicated, with whom these issues should be communicated and the methods of communication.
6. Operations
This step focuses on executing the plans and processes defined in previous sections. The organization needs to document all actions carried out to ensure that processes are executed as planned.
Additionally, outsourced processes need to be identified to evaluate and control information security risks.
7. Performance evaluation
Performance evaluations ensure the continued effectiveness and future improvement of the ISMS. It also regularly identifies areas for potential improvement in information security.
Internal audits and management reviews need to be conducted and documented at defined regular intervals to evaluate ISMS performance.
8. Improvement
Nonconformities with ISO 27001 requirements need to be addressed immediately upon discovery. Organizations need to identify and execute the steps to ensure that the same issues don’t recur.
Additionally, enterprises must continually attempt to improve the suitability, adequacy and effectiveness of their ISMS.
Information security policy standards
ISO 27001 is one of several information security policy standards used to secure data. In addition, PCI DSS, SOC 2, SOX, HIPAA and the Information Governance Toolkit play an important role in how your service executes its information security governance policies.
As an ISO 27001 certified service provider, Imperva consistently updates its information security policies, ensuring all customer data is handled properly.



