Imperva Research Labs finds the average database has 26 Common Vulnerabilities and Exposures
SAN MATEO, CA — September 14, 2021 — Imperva, Inc., (@Imperva) the cybersecurity leader whose mission is to help organizations protect their data and all paths to it, releases the findings of new threat intelligence research showing that nearly half (46%) of all on-premises databases globally are vulnerable to attack. A five-year longitudinal study conducted by Imperva Research Labs comprising nearly 27,000 scanned databases discovered that the average database contains 26 existing vulnerabilities.1
More than half (56%) of the Common Vulnerabilities and Exposures (CVEs) found were ranked as ‘High’ or ‘Critical’ severity, aligned with guidelines from the National Institute of Standards and Technology (NIST). This indicates that many organizations are not prioritizing the security of their data and neglecting routine patching exercises. Based on Imperva scans, some CVEs have gone unaddressed for three or more years.
“While organizations heavily invest in security, our extensive research shows that most have neglected the basics,” says Elad Erez, Chief Innovation Officer, Imperva. “Security patches of endpoints and applications are usually deployed in a relatively quick and frequent manner, yet too often, organizations tend to delay their database security patches out of concern for application downtime or application business logic failure. Although these concerns are valid from an application owner’s standpoint, this situation actually leaves an organization’s most critical assets vulnerable. Although we continue to see a major shift to cloud databases, the concerning reality is that most organizations rely on on-premises databases to store their most sensitive data. Given that nearly one out of two on-prem databases is vulnerable, it is very likely that the number of reported data breaches will continue to grow, and the significance of these breaches will grow too.”
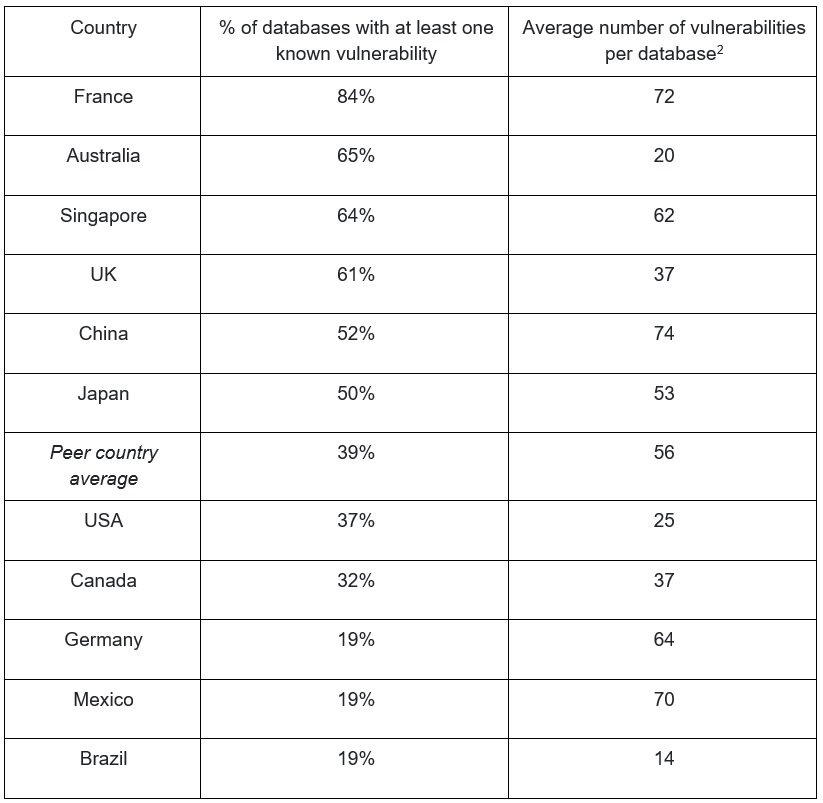
Regional analysis uncovers significant disparities between nations, with countries such as France (84%), Australia (65%) and Singapore (64%) having much higher incidences of insecure databases. However, for countries such as Germany and Mexico, while the number of insecure databases is relatively low, those that are vulnerable are well above the average when it comes to the number of vulnerabilities capable of exploitation.
The unprecedented number of database vulnerabilities offers attackers a vast landscape of opportunity. A separate study by Imperva Research Labs earlier this year found that the number of data breaches is growing by 30% annually while the number of records compromised increases by an average of 224%.
For non-publicly accessible databases, attackers can use a range of tools such as SQL injections (SQLi) to exploit vulnerabilities in web applications that are connected to a database. This remains a consistent business threat as nearly 50% of breaches in the past several years originate at the application layer. Separately, attackers may use phishing and malware to gain a foothold in the internal network and then move laterally to the vulnerable database.
Erez mentions that one of most concerning problems today is that it is way too easy for attackers to exploit known vulnerabilities. Once a database is found with a vulnerability, finding its exploit code is as easy as searching through exploit search engines. Once an attacker is inside, they can perform full data exfiltration, conduct a ransomware attack, or use the database as a foothold into the internal network to move laterally.
“This research is based on scans of real on-prem databases used by organizations around the world,” says Erez. “That’s what makes it so unique: it is a close representation of true business realities. It’s also important to note that while conducting the study, privacy and security remained our top priority, so all data was collected in an anonymized manner.”
Given the staggering number of vulnerabilities that exist in on-premises databases, it should come as no surprise that the number of data leakage incidents has increased 15% over a 12-month average. An analysis of data breaches since 2017 shows that a majority (74%) of the data stolen in a breach is personal data, while login credentials (15%) and credit card details (10%) are also lucrative targets.
“We are in the midst of similar research for cloud databases, and what we’re seeing is that while there are fewer vulnerabilities in cloud databases, security misconfigurations in cloud databases tend to happen more frequently,” Erez adds. “This is because it is very easy to mistakenly apply a wrong configuration or to disable a security feature in a cloud database. It will be interesting to see what other security differences exist between the two deployment models.”
Additional Information
- Interested in what is happening with data breaches? Read Imperva Research Labs’ Lessons Learned From Analyzing 100 Data Breaches report
- Learn how Imperva Database Security tools can provide visibility and protection for all data assets, whether on-premises or in the cloud
- Check out the Imperva Blog for the latest products and solutions news and threat intelligence from Imperva Research Labs
1Data inclusive from 2017 – 2021
2Figure calculated from databases that have at least one known vulnerability
About Imperva
Imperva is the cybersecurity leader whose mission is to help organizations protect their data and all paths to it. Customers around the world trust Imperva to protect their applications, data and websites from cyber attacks. With an integrated approach combining edge, application security and data security, Imperva protects companies through all stages of their digital journey. Imperva Research Labs and our global intelligence community enable Imperva to stay ahead of the threat landscape and seamlessly integrate the latest security, privacy and compliance expertise into our solutions.
© 2021 Imperva, Inc. All rights reserved. Imperva is a registered trademark of Imperva, Inc.