Account Takeover is a type of identity theft where a bad actor gains unauthorized access to an account belonging to someone else. Also known as brute force login, dictionary attack, credential stuffing, or credential cracking. If successful, the aftermath entails many unpleasant implications for customers and businesses alike. One of the tell-tale signs of an Account Takeover attack is spikes in failed login attempts. Yet, have you ever wondered about the meaning of a spike in successful logins? Did you know that many successful logins for one user can indicate fraud?
Don’t Ignore Successful Login Data
Securing the login functionality is a key component in preventing account fraud. But we must handle this functionality as a whole, and forge a better understanding of the stories behind all logins. Adding on to the existing security benefits of Imperva’s Advanced Bot Protection – Account Takeover, the Successful Users dashboard provides a new perspective into successful login activity that can indicate fraudulent behavior. This easy to access and understand dashboard, brings visibility to the usernames with the highest amount of successful logins to your website.
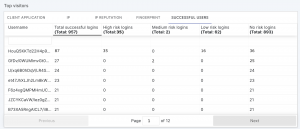
Red Flags You Should Be Aware Of
- Increased successful login activity for certain users within a set period of time. For example, a 25 percent increase over 24 hours. This calls for further investigation into the accounts’ activity.
- Groups of similar usernames (e.g. ArthurSmith vs. SmithArthur10) or dubious usernames (e.g. Hackerman101) topping the successful logins list should be looked into.
- Investigate the correlation between your known compromised users and the Successful Users dashboard. Compromised users are accounts that might have already been taken over. Imperva’s Account Takeover easily identifies these accounts and presents them on the dashboard. Investigating this may reveal compromised accounts that are being used to commit fraud.
Enabling A Comprehensive Fraud Investigation
Our customers have found exceptional success using the feature to uncover accounts that were created for fraudulent purposes as well as restore compromised users’ accounts. Lacking the knowledge of successful login activity, these accounts would go undetected for long periods of time, committing fraud without interruption. Let’s dive into the use cases where successful logins led to the uncovering of fraudulent activity.
Exposing Canary Accounts
Bad actors aren’t only using the login functionality of websites to test stolen credentials. They are now using it to identify when they have been detected too. Data from the dashboard helped security teams uncover this new type of account fraud: Canary Accounts. These accounts are created for the sole purpose of testing whether a security rule has been triggered. They serve as a tool for attackers looking to commit fraud, rather than being the direct source of fraud. Attackers would try out 4-5 bad credentials before attempting to login to their Canary Account again. If they were unable to login, they now know that they have indeed triggered a security rule. These accounts allow them to optimize their brute force capabilities. Armed with data from the Successful Users dashboard, security teams have been able to identify and remove these Canary Accounts.
Assisting with Loss Prevention
Loss Prevention teams use the feature to detect two different types of account fraud:
- New accounts being created in order to test stolen credit cards (carding).
- Accounts that have been compromised in data breaches or leaks, and are being used to make purchases using the saved credit card, gift card balance or loyalty points.
Leveraging data from the report, the teams were able to focus on suspicious accounts. Next, they looked into the transaction history in those accounts that were marked suspicious. Have they made any orders? Did they process orders? Were the orders shipped to different locations? Once the team was able to confirm an account was created for fraudulent reasons, they used that data to validate deleting the account.
Protect Logins And Eliminate Account Fraud With Imperva
Advanced Bot Protection – Account Takeover provides login protection with no added latency and minimal user disruption. It enables security teams to take swift, informed action against malicious, bot-driven Account Takeover attacks by producing insights that are easy to understand and act upon. The intuitive dashboards provide visibility into attack attempts, users at risk and compromised user accounts. And with the recent addition of the Successful Users dashboard, we are broadening the scope of fraudulent behavior investigation and detection, bringing the focus to the login functionality as a whole.
Advanced Bot Protection – Account Takeover is a part of Imperva’s Application Security platform. Start your Application Security Free Trial today to begin protecting your logins.
Try Imperva for Free
Protect your business for 30 days on Imperva.











