About six months ago, we first brought attention to the increasing number of high Mpps (high-rate) assaults DDoS perps are using—putting a new twist on tried-and-true attack vectors.
In our Global DDoS Threat Landscape report, we described such attacks as a double threat:
“Such assaults force operators to think in terms of forwarding rates rather than throughputs, when considering the soft spots of their network infrastructure.”
With the first quarter of 2016 now behind us, we’re again compelled to warn you about these attack scenarios, as they’ve become even more prevalent in the passing months.
To understand the threat posed by high Mpps attacks, it’s important to grasp the difference between forwarding and throughput rates, as well as the current state of DDoS mitigation equipment.
Forwarding Rate vs. Throughput Rate
Of these two terms, you’re likely more familiar with throughput rate. Also referred to as bandwidth or capacity it’s the amount of data that can travel through your connection and is measured in bits per second (bps). For example, a 5 Gbps network can handle 5 billion/giga bits traveling through it every second.
Forwarding rate, on the other hand, refers to the number of network packets that can be processed by your networking equipment (e.g., your switch or router). Forwarding rate is measured in packets per second (pps) and DDoS mitigation gear typically handles rates in multiples of a million/mega packets per second (Mpps).
Figuratively speaking, throughput rate is similar to the weight capacity of an elevator car, while the forwarding rate can be thought of as the maximum number of people permitted inside.

Thinking in such terms helps understand why, while closely related, throughput and forward rates are not directly convertible.
Just like people, network packets come in different shapes and sizes. As a result, there is no real way of knowing how many packets make a gigabit, just like there is no way of knowing for sure how many people can fit into an elevator before exceeding its weight capacity.
What you can do is make an assumption about network packet size. However, because that size can be anywhere between 512 bits (64 bytes) and 12,000 bits (1,500 bytes), doing so still leaves plenty of room for uncertainty.
To put things in perspective, this means that handling 1 Gbps of traffic requires processing rates of ~83Kpps to ~1.9Mpps.
In elevator terms, that’s like saying that capacity is between 10 and 220 people. That leaves quite a gap, one which DDoS attackers are now learning to exploit.
No Elevators for 220 People
What attackers are now discovering is that most standard DDoS mitigation appliances, commonly found on-prem and in the scrubbing centers of service providers, were never built for the “220 people” scenario.
Until recently, mitigation solution vendors and their buyers were mostly concerned about high throughput attacks; the 300 and 400 Gbps monsters that grabbed headlines and took down gaming networks.
These attacks were mostly executed via amplification attack vectors (e.g., DNS amplification) and methods such as using abnormally large SYNs. In either case, the attacks owned their size to the use of artificially inflated network packets.
Oftentimes these supersized packets were 500 bytes (4,000 bits) or larger. This means that the overall forwarding-to-throughput conversion rate was on the low side—somewhere at 0.2 – 0.4 Mpps/1 Gbps.
Mirroring this, security appliances were built to sustain unusually high throughputs, but not abnormally high forwarding rates. The general assumption was that 1 Mpps/1 Gbps is a good ratio to have. This is why many mitigation appliances today have specs like 60 Gbps/60 Mpps. This also made the job easier for marketers who don’t enjoy confusing folks with too many different numbers.
However, while the mitigation industry kept to its methods, DDoS offenders continued to stockpile botnet resources. On one hand, they actively continued to compromise additional devices. On the other, they also passively benefited from the organic evolution of Internet connectivity (as per Nielsen’s Law).
In the second half of 2015, we noticed that things had reached a turning point. Suddenly, certain DDoS thugs had enough botnet muscle to mount a 100 – 200 Gbps attacks, without the use of amplification vectors or abnormally large network packets.
This resulted in high Mpps/Gbps DDoS floods, like the one below.
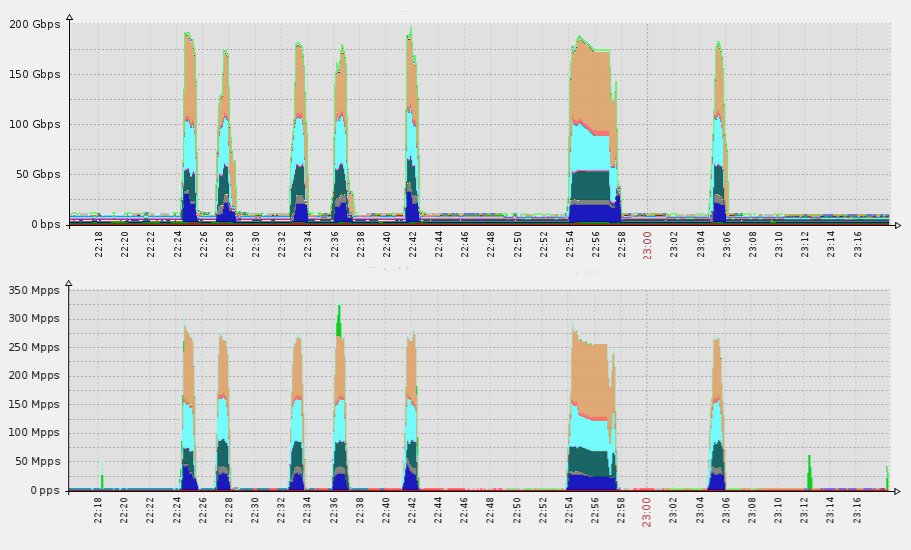
What you see is a 200 Gbps assault generated via a 300+ Mpps, making the conversion rate flip towards 1.5 Mpps/1 Gbps. The average packet size here is only ~85 bytes.
Still remember that elevator sign? Notice how it says “1600 KG or 21 PERSONS”. This is exactly how mitigation equipment works. For the equipment to fail, an attack has to exceed either the throughput rate or the forwarding rate.
This is why we refer to these attacks as a double threat. With them, perpetrators try to double their chances by attacking on both fronts: saturating uplinks with high Gbps attacks while trying to crash network switches with high Mpps rates.
Start Thinking Mpps
Today high Mpps attacks are more common than ever before. To put things in numbers, in the first quarter of 2016, on average, we mitigated a 50+ Mpps attack every four days and an 80+ Mpps every eight days. More than a few of these exceeded 100 Mpps.
In the interest of toning down the FUD, it should be said that—for now—only the most capable botnets have the muscle to mount such an assault. In the coming years, however, these capabilities will become more common due to an imminent expansion of botnet resources.
To assess the threat to your organization, review the Mpps limitation of your mitigation solution and ensure that you’re covered against high-rate attacks. The best scenario is to have a solution that can handle 300 – 400 Mpps or more, especially if your business is likely to draw the interest of professional DDoS offenders.
For the moment you can settle for an 80 – 100 Mpps forwarding rate, as long as you know that this is something that demands further attention down the road.
The same advice also applies to mitigation providers. High Gbps assaults will likely continue to be the predominant threat. That said, the security industry needs to start thinking in terms of Mpps when developing next gen of DDoS mitigation solutions and services.
Try Imperva for Free
Protect your business for 30 days on Imperva.












