Identity theft has come a long way in the age of technology. The more data is available online, the greater the threat. In this blog we will dive into the different characteristics and statistics of real world Account Takeover attacks as recorded and mitigated by Imperva’s Advanced Bot Protection – Account Takeover.
What is Account Takeover?
Account Takeover is a form of identity theft in which bad actors gain illegal access to user accounts belonging to someone else. This is usually achieved using brute force login techniques such as Credential Stuffing, Credential Cracking or Dictionary attack. A successful attack can result in extensive damage to customers and businesses alike: account lockouts, financial fraud, theft of Personally Identifiable Information (PII) as well as sensitive business information and much more. Unmitigated Mega Account Takeover attacks can even overwhelm web servers and lead to a Denial of Service.
What does an Account Takeover attack look like?
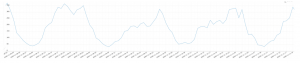
Let’s take a look at the usual daily login traffic to a certain website. Notice the clear pattern with regular peak hours and low-activity hours:
Now let’s take a look at an Account Takeover attack that targeted the same website:
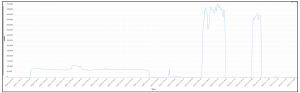
Notice the attack traffic looks very different; there is no daily pattern repetition. While the legitimate login rate ranges between 50 and 350 logins per hour, the malicious login rate ranges between 75,000 and 700,000 during the attack. Looking at the graph reveals four different Account Takeover attacks:
- The first one looks low and wide, it lasted 6 days with a fairly stable login rate of 75,000 logins per hour.
- The second is a small “burst” attack with 80,000 login attempts and it lasts only one hour (on 2021-01-03 at 23:00).
- The third is one of the most intensive ATO attacks we saw in January: 700,000 login attempts per hour! It lasted 29 hours!
- The fourth looks similar to the third, but it is slightly less intense and shorter in duration.
Account Takeover by the numbers
Of all login attempts in the previous months, a staggering 33.8 percent were malicious attempts originating from bad bots. This is a third of all login activity consisting of bad bots attempting to take over accounts. On average, websites were under an Account Takeover attack for 16 percent of the time. These numbers reveal just how common and frequent Account Takeover attacks have become.
What industries were mostly affected by Account Takeover attacks?
According to the 2021 Bad Bot Report, The computing & IT sector was the most targeted by Account Takeover attacks. In many cases, the thought process behind gaining access to user accounts in this sector is that it may provide access to sensitive information about clientele. The travel industry came in second, with loyalty programs and air miles being the main targets. Entertainment & arts which include ticketing and streaming services was also high up the list of targeted industries.
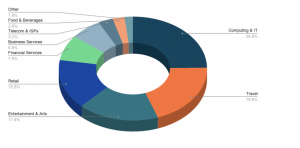
Where do Account Takeover attacks originate from?
Generally, Account Takeover attacks originate from various sources, such as cloud hosting servers, ISPs, botnets and anonymous proxies. When dissecting the attacks by country, 45 percent of Account Takeover attacks originate from the US. Brazil, China, Russia and the UK follow with significantly lower percentages. Many Account Takeover attacks are launched from proprietary bot engines or tools, but the majority are still trying to impersonate legitimate browsers, mainly Chrome (47.2 percent).
Do Account Takeover attacks have set time patterns?
The following graph represents legitimate logins and Account Takeover attempts over a 24-hour period:
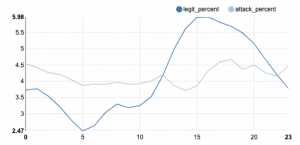
Notice that legitimate logins follow a regular time pattern with clear peak hours around the afternoon, as expected from legitimate users showing normal human behavior. In contrast to that, it is clear that Account Takeover attacks do not follow specific time patterns as humans do.
What does a sophisticated Account Takeover attack look like?
Automated Browser ATO attack
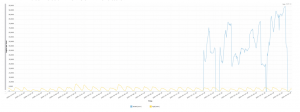
In this medium-sized attack, the sophisticated attacker used an automated browser, with full JavaScript support, making his requests appear exactly as legitimate Chrome requests.
The attack lasted for a period of 11 days, during which 12 million malicious login requests were sent, with up to 95,000 login requests per hour. During the attack 10.8 million usernames were used from 61,500 distinct IP addresses.
“Low & Slow” evasive ATO attack
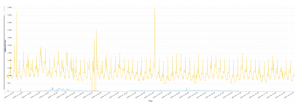
This sophisticated attacker chose a “low & slow” Account Takeover attack style to go under the radar without being detected. His login rate was always well under the usual legitimate login rate. That way, by looking at the login graph pattern or trying to measure the failed logins, he wouldn’t be detected.
We have managed to isolate this attack from the rest of the login traffic by applying unique signatures and filters to the logins traffic.This attack was executed in two waves: the first wave lasted for 15 days and after a timeout of one week, a second wave of 25 days. During those 40 days, 51,800 login requests were sent with an average low rate of 50 login requests per hour. During this attack, 21,000 usernames were used from 75 distinct IP addresses which were used by anonymous proxies.
Conclusions
Behind every bad bot operation, there are human beings looking to make a profit. If there is money to be made by taking over user accounts on your site, the probability of an attack is very high. Account Takeover attacks vary by their sophistication, evasiveness and intensity. From low, unnoticed attacks to intensive attacks, which if not mitigated may cause Denial of Service due to the sheer amount of requests pounding the web server. The characteristics and statistics of Account Takeover attacks that were described in this blog may change and evolve over time, as attackers improve their techniques and change their tactics.
This is why having an advanced solution matters. Imperva’s Advanced Bot Protection – Account Takeover leverages our global network to track new and emerging techniques and incorporate those into the solution using machine learning. The solution provides login protection without adding latency or impacting the user experience.
Learn more about Account Takeover in the 2021 Bad Bot Report. Download your copy here.
Start protecting your logins today. Begin your Application Security Free Trial.
Try Imperva for Free
Protect your business for 30 days on Imperva.












