Imagine that your network is under attack. A couple of minutes ago, you detected a large burst of traffic, out of nowhere. Now it’s in excess of 60 Gbps, and overwhelming your network. Your mitigation service hasn’t picked up the attack yet, and you’re just about to take a closer look when it stops as fast as it started, like flicking a switch. You go grab a coffee and by the time you get back, the attack has started again. This time, it’s big and powerful enough to prevent your mitigation service from activating the cloud scrubbing platform. Once again, before you can even get a handle on it, it stops. Is it coming back? What’s going on?
If this scenario sounds familiar, your organization isn’t just a victim of a distributed denial of service (DDoS) attack – it’s part of a trend. Imperva’s 2021 DDoS Threat Landscape Report reveals a clear trend towards shorter, high volume attacks, with an average duration of only six minutes. Just over a fifth of attacks last two minutes or less, before the attackers circle back and hit again. When Imperva Research Labs first started examining these pulse attacks a few years ago, they were considered unusual. Imperva’s latest research shows that they account for almost half of all attacks today – and, as we’ll see, some of them come with a twist: a ransom note from the attackers.
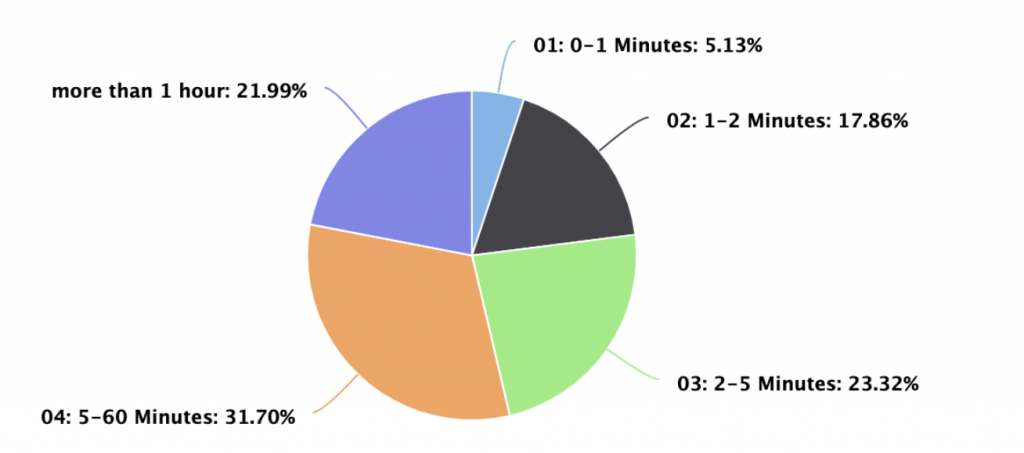
But what if even longer attacks were also part of this broader pulse trend? There’s a lot of evidence to suggest that this is the case…
Anatomy of a ‘normal’ DDoS attack
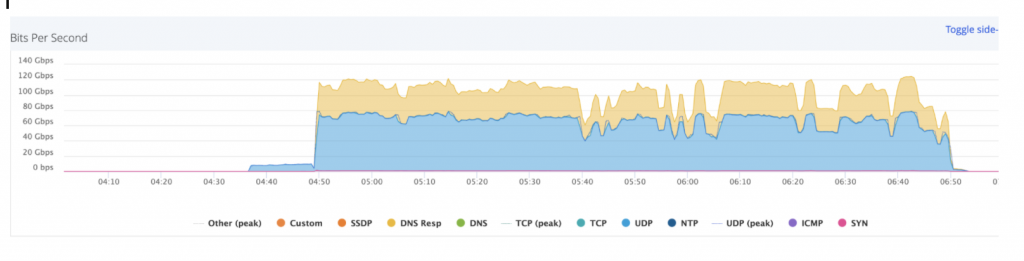
When Imperva mitigates a DDoS attack, we only send a ‘DDoS End’ notification after three hours of ‘peace time.’ So an attack that stops and resumes after an hour is considered an ongoing attack. If you’re one of the 22% of organizations that experienced a network DDoS attack lasting longer than an hour, here’s what two hours of ~100 Gbps DNS amplification looks like at first glance:
And this is a four-hour long attack…
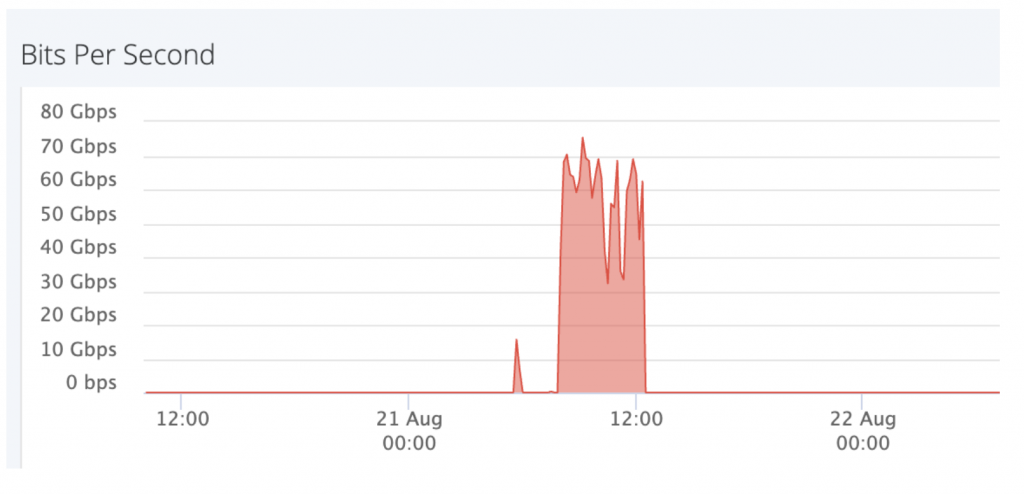
Zoom in for a closer look, and you’ll notice that the attack is coming in short, repeated bursts that last up to one minute, like a series of punches. How many times over the course of this four hour attack did the victim think “It’s over” only for it to start again?
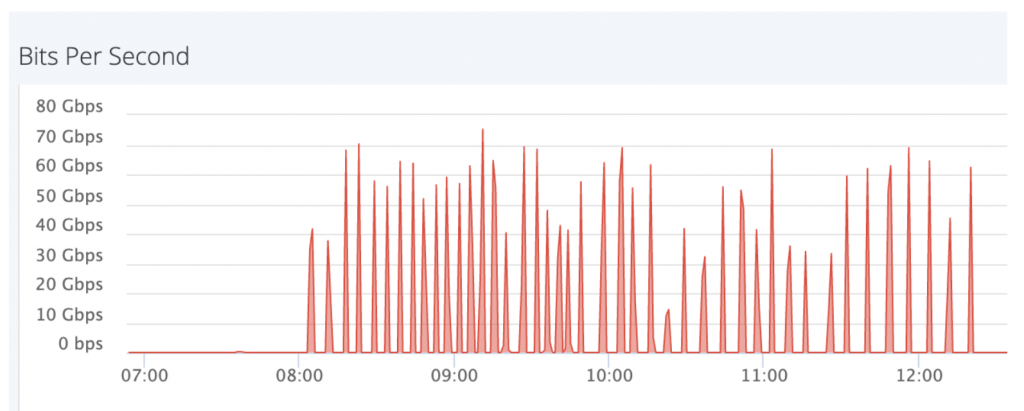
This trend towards heavy-duty spikes is underlined by other recent attacks analyzed by Imperva – one lasting eight hours, the other a twelve-hour endurance sequence of short, high-impact hits. In the case of the eight hour attack, you can see that each spike lasted for 1.5-8 minutes, making it impossible for the victim to know when the attack will end.
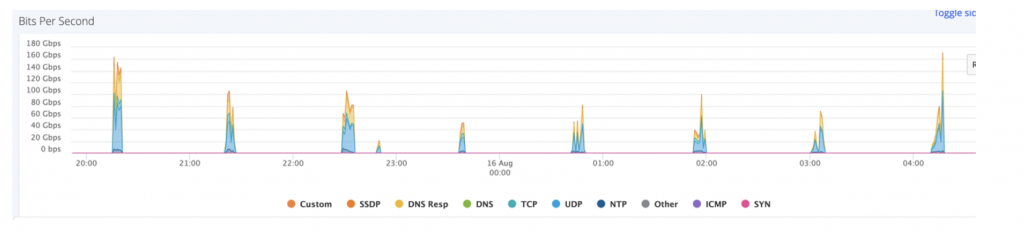
This 12 hour attack is even more remarkable: spike after spike of SYN flood and Large SYN, reaching 26 Gbps.
Again, it’s almost impossible for a victim to anticipate when this will stop. And again, it’s important to understand that even though this went on for 12 hours, it’s a sequence of multiple, sharp, repeated attacks, encapsulating a single attack. While some might interpret this as 19 attacks, as mentioned earlier, Imperva measures attacks that stop and resume within three hours as an ongoing attack.
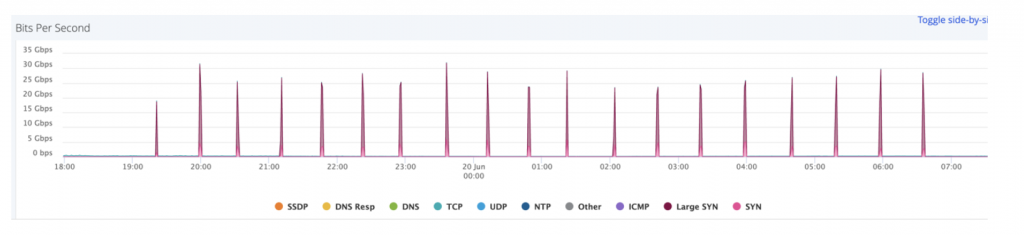
A lot of the time, one big, heavy hit is all it takes: this attack ramped up to 400 Gbps for 90 seconds. That’s enough to take an organization down – and even a brief interruption of service can take hours or even days to recover from.
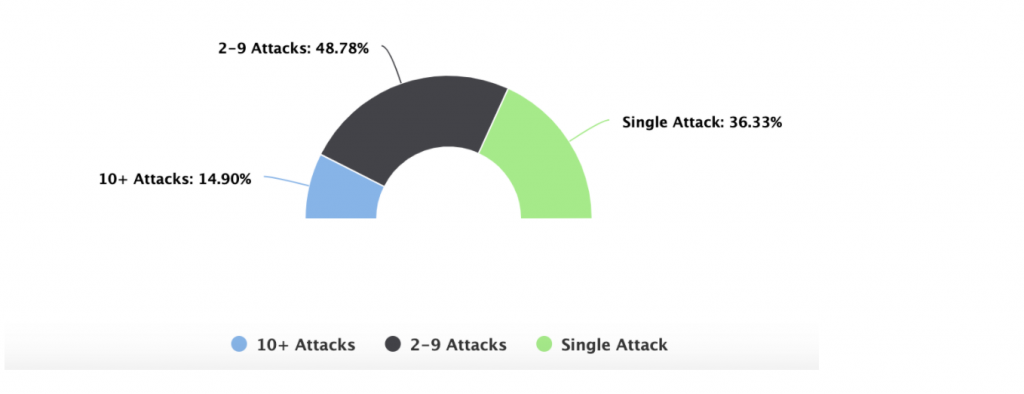
And as Imperva’s research for the first six months of 2021 indicates, if an organization is attacked once, the attackers almost always come back for more:
While this pulse trend is skewed heavily towards networks and websites, Layer 7 application attacks also occur. The key difference observed by Imperva is that the duration of L7 DDoS attacks has remained more or less consistent in recent years.
Why does this matter?
Shorter attacks are dangerous for multiple reasons. They’re often a distraction tactic as part of a wider, multi-vector attack. Legacy DDoS solutions are often configured to ignore this level of activity, giving attackers the chance to stay under the radar and scope out larger attacks.
Short, sharp and persistent attacks typically overwhelm hybrid cloud and on-premise solutions, causing maximum damage before backup mitigation can start. These shorter, more intense hits are difficult to mitigate, unless you have always-on protection or an SLA with your provider that guarantees mitigation within seconds.
DDoS with a twist: when your attackers demand a ransom
Many attacks simply come out of nowhere – for the victim, at least. But there is an increasing trend towards Ransom DDoS (RDoS). These attackers usually begin by sending a ransom note threatening the attack unless the organization pays, followed by a short ‘demo’ attack. Sometimes, however, the ransom note is delivered inside the attack itself, like this recent example we recorded from a ‘justice warrior’ who does not like the line of business of a specific customer:

In this instance, the attacker was unable to ‘fight to the end’ because Imperva mitigated the attack before it could succeed.
What happens when a customer ignores the ransom note? Let’s take a look…
The attacker started with a ‘short and slow’ simple service discovery protocol (SSDP) attack: “We’ll just start with a small attack on a few random IPs to show we mean business.” When you look at the screenshots below, you can see 2.46Gbps of SSDP as execution of the warning.
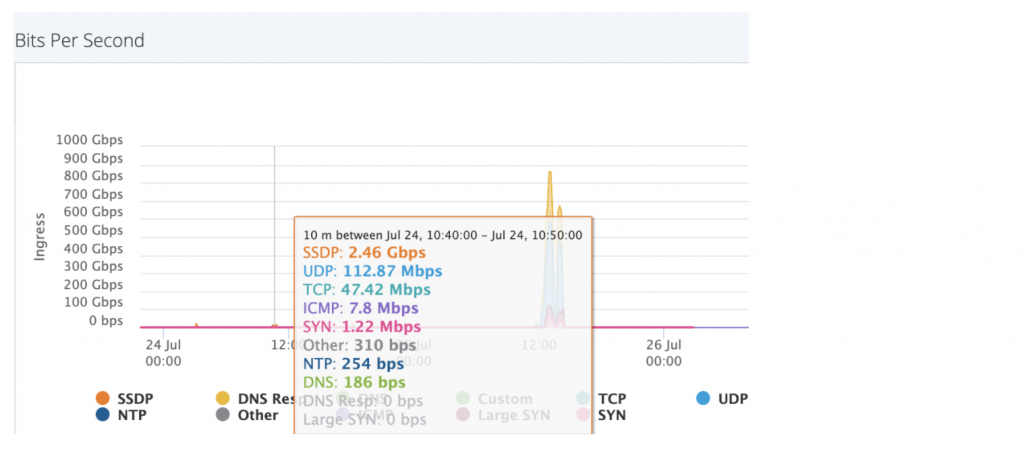
Here’s what it looks like when it’s “Last chance to pay”. When you look at the screenshots below, you can see the attack progressively ramping up over time.
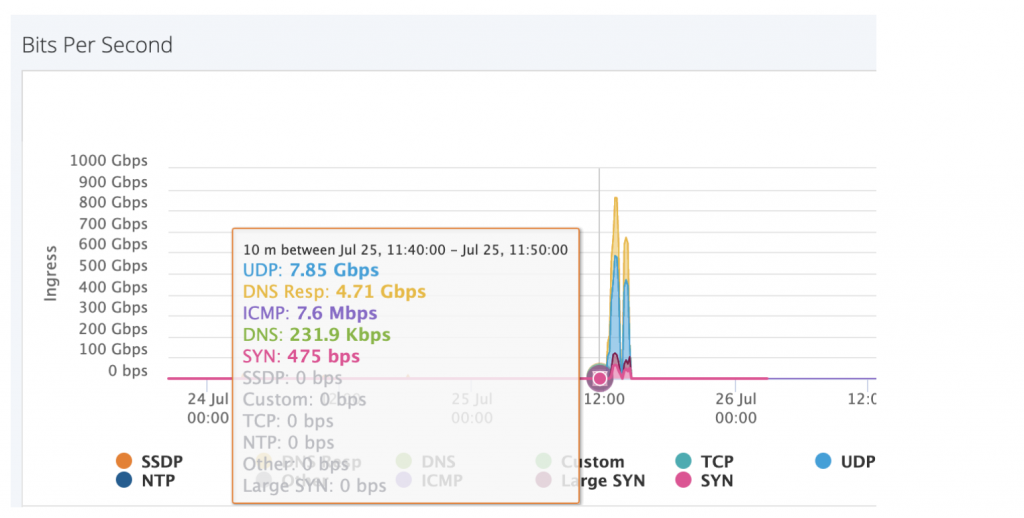
And finally, the real attack hits at 13:10: 860 Gbps of DNS amplification, UDP flood, SYN flood and Large SYN attack…
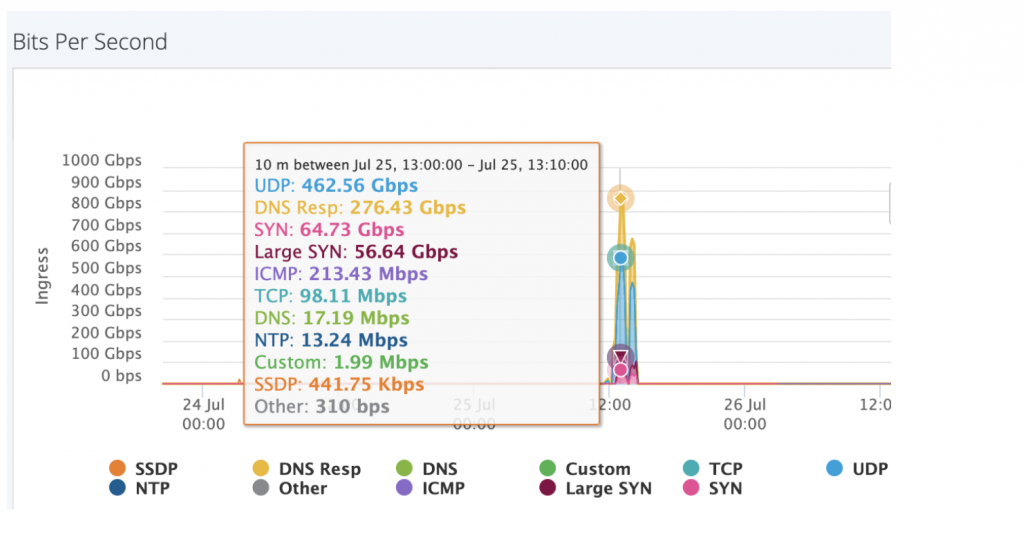
The victim in this case continues to be attacked on a regular basis, but now has a solution in place that can mitigate within three seconds.
You snooze, you lose: time to mitigate matters
The trend towards shorter and sharper attacks that Imperva Research Labs observed last year continues for network layer DDoS. This reality underlines a clear need for always-on DDoS protection, along with faster reflexes for time-to-mitigation.
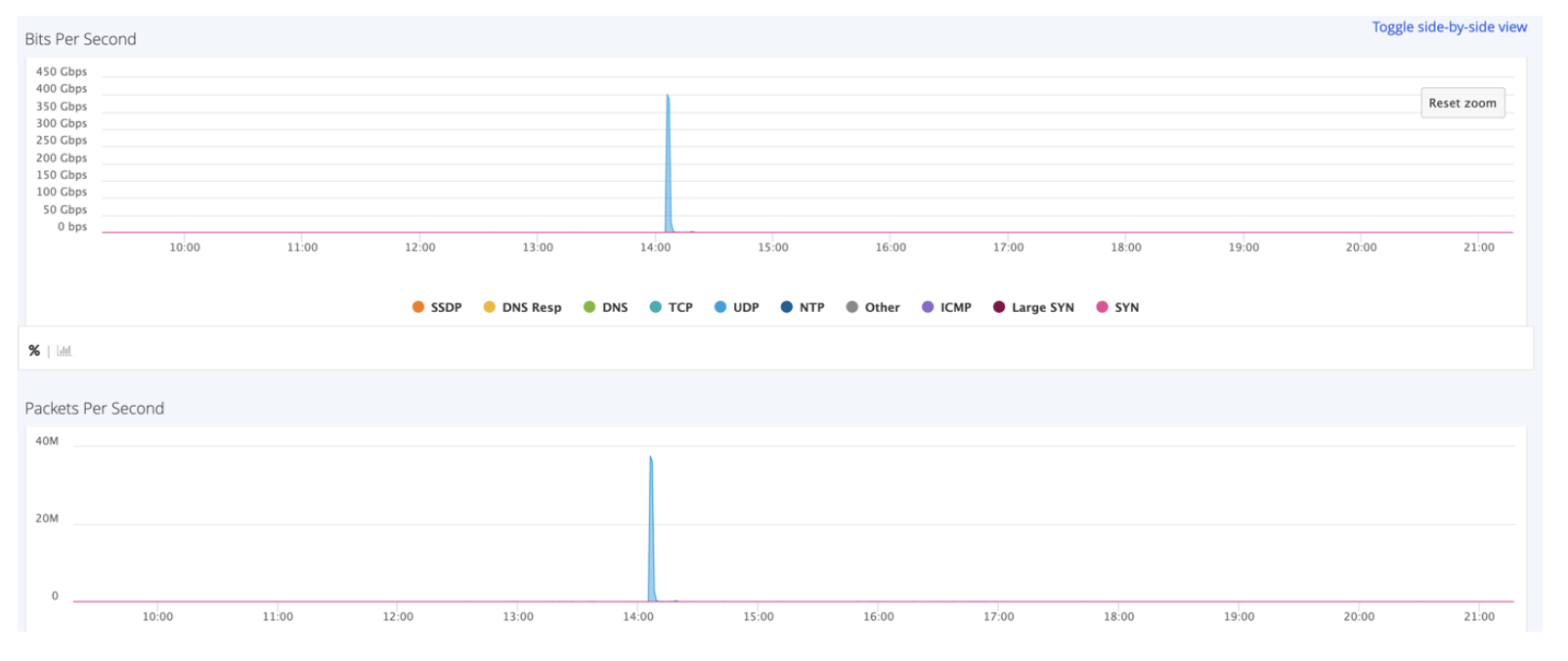
When DDoS attackers are capable of attacking at will, there’s little comfort in the trend towards shorter attacks; the level of persistence can’t be ignored. In this respect, the largest attack ever mitigated by Imperva, in July 2021, is informative – as it ramped up to an eye-watering 1.06 Tbps burst in under five seconds. In a case like this, where the first wave of the attack involved a 90 second burst of a large SYN flood, being able to start mitigation in seconds is vital. This type of attack would be impossible to mitigate with an on-premises or hybrid DDoS approach, where upstream connectivity would be totally overwhelmed.
To learn more about the latest trends in DDoS attacks, get your copy of the 2021 DDoS Threat Landscape Report today.
Got a ransom threat? Have any questions? Not protected? Let us know, we are here for you.
Try Imperva for Free
Protect your business for 30 days on Imperva.














