There’s no question that today’s cyber attackers use increasingly sophisticated methods in order to disrupt business or steal private data. And faced with so many attacks from various sources, IT professionals are forced to constantly challenge themselves to identify those alerts more critical than others and that require immediate attention. Some of the attacks are carried out using the same IP over and over again, while others use constantly changing IPs hiding behind anonymized proxies.
Nevertheless, while all these incidents take place, some malicious IPs that have previously attacked other customers around the globe could be lurking, waiting for the chance to breach and penetrate your defenses. Wouldn’t you want to know about them and mitigate this threat? This example represents only the tip of the iceberg in the constant and laborious battle to seek the real and immediate threats that require you to act quickly. Attack Analytics, by Imperva, distills millions of events taking place around the world and prioritizes incidents that need investigation and remediation, further benefiting from the intelligent insights generated by Imperva’s Actionable Insights functionality.
IP reputation and actionable insights, hand in hand
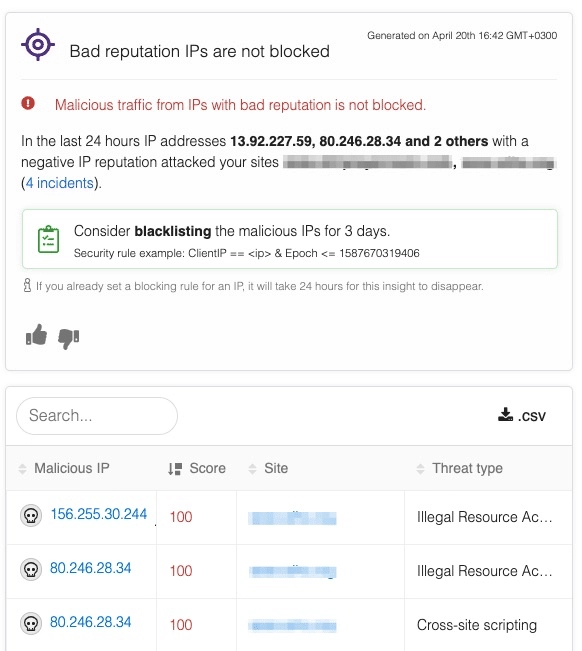
Actionable Insights was formed by combining our recently introduced IP reputation knowledge and customer threat intelligence. Now, we’re able to pinpoint penetrated attacks of customers that were carried out from Bad Reputation IPs. These are the IPs whose risk assessment levels, based on their activity – including both clean and malicious traffic – across our wider customer base over the past two weeks, are without a doubt, malicious. Given an IP’s high maliciousness assessment and the fact it recently attacked a customer, we suggest blacklisting it for a short period of time.
The new Bad Reputation IPs insight provides additional metadata such as:
- The IP address from which the attack was made with basic IP reputation details and a link to our IP Reputation service for a full IP characteristic behavior analysis
- The site this IP penetrated and endangers
- The attack type utilized by this IP
- Drilldown to the specific incidents generated by this malicious IP
This example is just one additional way of how Imperva plays a pivotal role in your decision-making with a simple-to-action recommendation for improving your security posture and eliminating any immediate risk.
Try Imperva for Free
Protect your business for 30 days on Imperva.