On July 22, an Imperva customer was targeted by a network DDoS attack that reached a maximum bandwidth of 1.37 trillion bits per second (Tbps), making it one of the largest attacks that Imperva has stopped and one of the larger DDoS attacks on record. The attack lasted a little over two hours in total, and targeted a single IP owned by a domain-hosting site.
Most DDoS attacks stick to either TCP or UDP floods, but this one contained both a UDP wave reaching 1.37 Tbps and a TCP wave that reached 1.06 Tbps – marking the first time we’ve seen both TCP and UDP rates reach more than 1 Tbps in a single attack. Traffic switched between both TCP and UDP floods greater than 0.5 Tbps in a matter of minutes, which goes to show why it’s so important to have a fast DDoS detection and remediation solution.
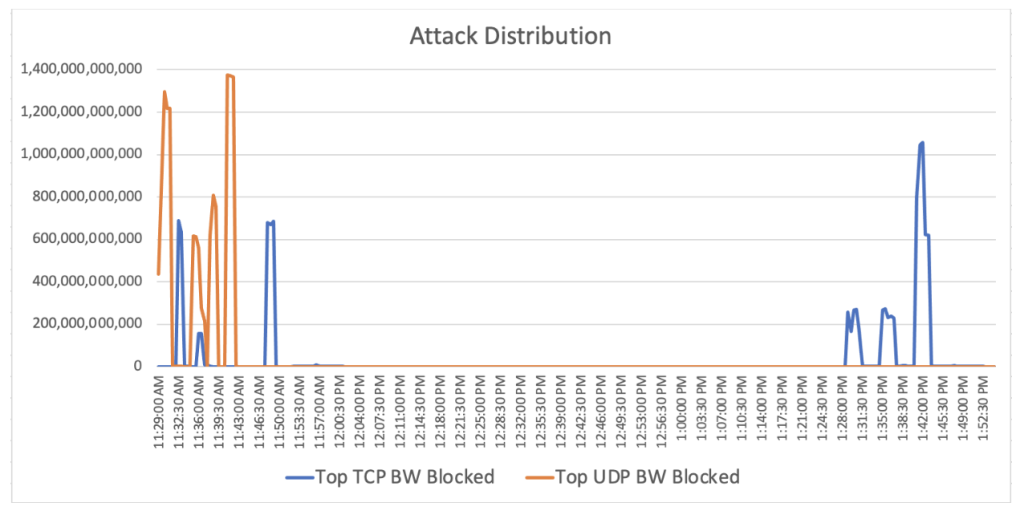
The attack was conducted by a very active botnet that has targeted over 50 Imperva customers with network DDoS attacks since this attack was mitigated in July. The botnet is composed of at least 20,000 IPs from 109 countries, and uses devices susceptible to many vulnerabilities, including recent 2022 CVEs. This botnet includes a variety of routers, Boa web servers, security cameras, and devices running Windows and Linux operating systems.
Imperva Threat Research was able to identify this attack by its distinct packets, which sent garbled content in an effort to overwhelm the servers. Usually, attacks with high spikes like this stick to one type of protocol, so it’s interesting that the same IPs sent both TCP and UDP packets right after each other, reaching high rates in each type of flood.
Imperva DDoS Protection stops attacks quickly with minimal impact. Click here to learn more and schedule a free demo.
Try Imperva for Free
Protect your business for 30 days on Imperva.












