Extortionists Claim Connection to Notorious Threat Actor Groups
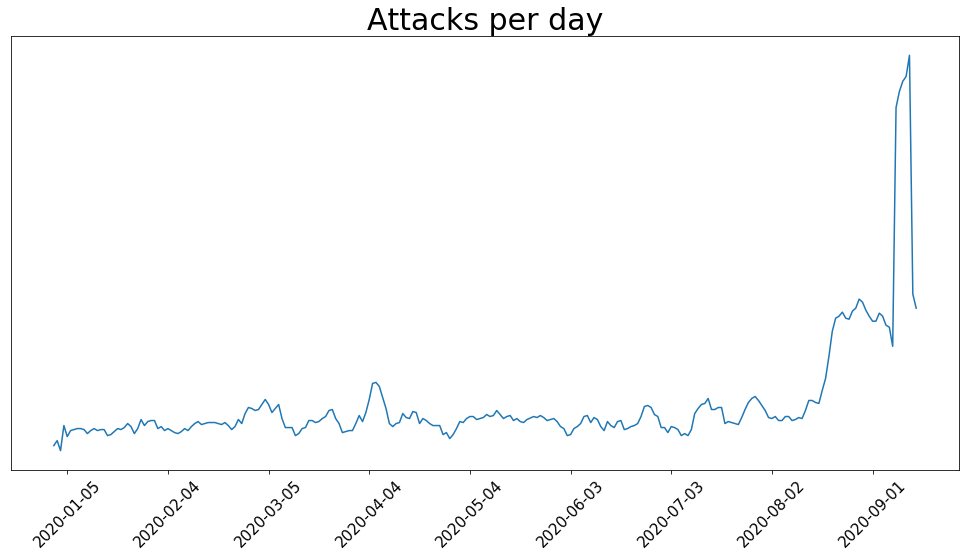
In recent weeks Imperva has become aware of a considerable increase in the number of serious Ransom Denial of Service (RDoS) threats, with extortion campaigns targeting thousands of large commercial organizations globally, not least the financial services industry. RDoS campaigns are extortion-based Distributed Denial of Service (DDoS) threats motivated by financial gain and the extortionists leverage the names of well-known threat actor groups in their ransom messages to demand payment in bitcoin currency to prevent a DDoS attack on their target’s network. The DDoS risk continues to be a challenge across the industry, and at Imperva we investigate all the attack types to better prepare our solutions and to mitigate them for our customers that leverage our products.
Imperva has observed this type of RDoS activity by a group claiming to be carrying out the attack in the name of ‘Lazarus’ and threatening to launch a DDoS attack against the customer’s entire network if a ransom is not paid within six days. Once the attack has started, a payment of 30 bitcoin (approx USD $328K) will stop it, with an additional 10 bitcoin (USD $110K) demanded for each day the ransom remains unpaid. The extortionist also threatened to begin a small DDoS attack on the company’s main IP address immediately to prove the threat is not a hoax.
DDoS attacks don’t always come with a ransom demand but, given that even one hour of downtime can cost organizations up to $100K in some cases, this type of RDoS attack is worth taking seriously and mitigating against.
Should you pay?
Paying might not be the solution. Known cyber threat groups that engage in RDoS campaigns usually don’t announce their intention to attack, so if you receive an extortion email prior to an attack there’s a good chance it’s a scam, or that the attackers aren’t who they claim to be and don’t possess major DDoS capabilities.
In fact, paying doesn’t necessarily guarantee an end to the problem. The extortionists might add you to a list of companies who pay out and just keep on threatening you and demanding even more money. They might even attack you even if you’ve paid.
Alternatively, a DDoS for hire/hacktivist group might want to attack your network but will try to get some extra cash by sending a ransom note. They’ll attack anyway, simply because it’s their agenda or because they’ve been paid to.
So while the scammers might threaten to launch small sample attacks following their initial warning, every second of downtime can hurt a business which is why time-to-mitigation (TTM) is vital.
How does Imperva DDoS Protection work
Imperva DDoS protection supports Unicast and Anycast technologies, powering a many-to-many defense methodology. This automatically detects and mitigates attacks exploiting application and server vulnerabilities, hit-and-run events and large botnets.
It offers an additional unique benefit from all others in that it consistently blocks any attack – no matter the size or how fast it ramps up – in less than one second, guaranteed by a 3-second SLA.
Are you currently under DDoS attack or have you received a ransom demand with a DDoS threat?
Imperva offers an Emergency DDoS Onboarding solution to protect you against any secondary attacks. The Imperva Infrastructure Protection service is easily deployed as either always-on or on-demand and a Solution Manager will guide you through the onboarding process to protect your entire network infrastructure against further DDoS attacks.
Click here for help now.
A closer look at the attacks
By Johnathan Azaria – Imperva Threat Research
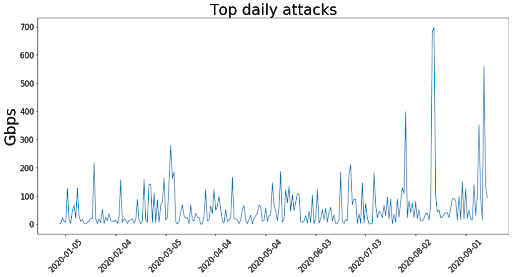
Imperva’s analysis of the sample DDoS attacks launched by the threat actors shows that the common, low-effort ransom DDoS attacks use amplification vectors such as DNS response, SSDP, NTP, Memcache etc. These vectors allow the attacker to use only a small number of attacking bots in order to generate a massive bandwidth attack. In other words, it’s a cheap, effective, low-effort way to channel a major attack, and not a small attack that ‘will not cause any damage’, as claimed in the scammer’s original message. These vectors work by exploiting vulnerable servers that can be manipulated into sending massive amounts of traffic to a target of the attacker’s choice.
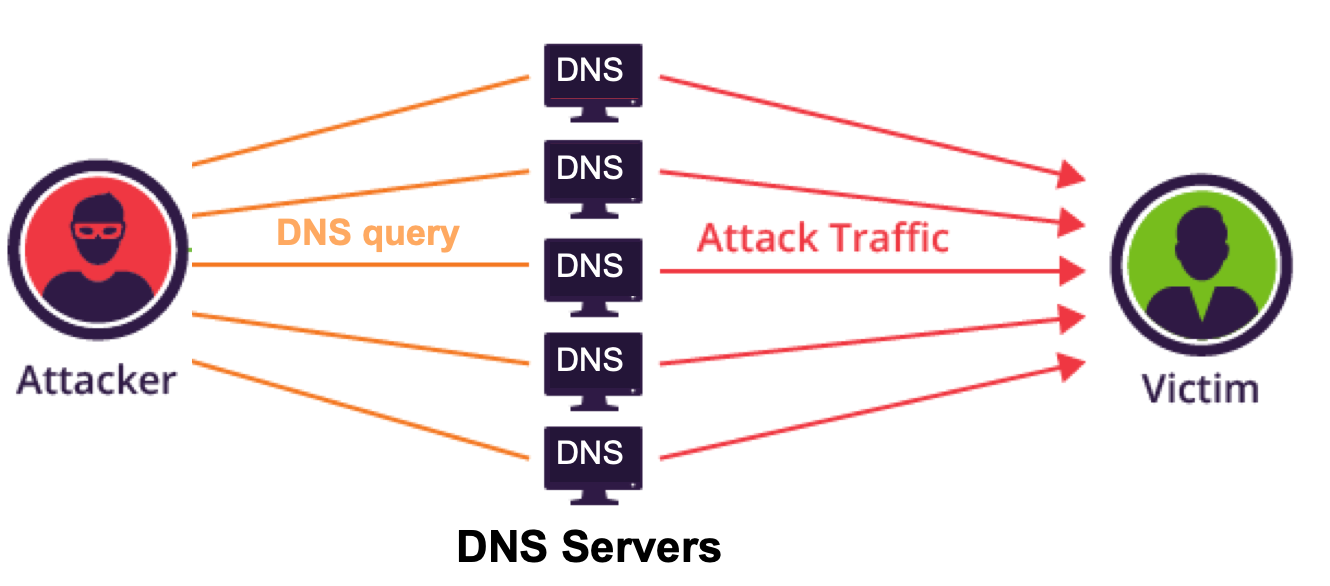
The flow of these attacks is quite simple. In this example, we’ll refer to DNS servers, i.e. a DNS amplification attack. Many DNS servers allow users to request all records of a certain site, a request known as an ANY request. The request itself is pretty small but the response from the DNS server is quite big because it contains many records – the ratio between the request size and the response size is the amplification factor. Attackers exploit this feature by sending many DNS ANY requests to DNS servers while pretending to be the victim. This causes the DNS server to send the response to the victim server, unaware it’s flooding it with massive amounts of traffic and effectively DDoSing it.
These vectors, as deadly as they might sound, are simple to detect and easily mitigated by cloud DDoS protection solutions. Because these attacks can peak quickly and reach devastating amounts of traffic, the most important factor is the time to mitigate – the amount of time it takes the protection service to start mitigating traffic.
Most of the RDoS attacks we mitigated in the last few weeks used amplification vectors. However, in some cases, the attackers took the time to do their homework.
In one massive attack we mitigated, the attackers partially studied the attacked network and sent in tailored HTTPs requests that were somewhat similar to the normal traffic.
Learn more about Imperva DDoS Protection Solutions here.
Try Imperva for Free
Protect your business for 30 days on Imperva.