“Hold out baits to entice the enemy. Feign disorder, and crush him.” Sun Tzu
The sophistication of cybercriminals and the attraction of the “Black Hat” cyberspace have grown dramatically over the years. In the past, cyber assaults were carried out mostly by amateurs, motivated by boredom or plain curiosity. Nowadays, such activities might be the work of successful business ventures, holding big financial stake in their success. With increasing professionalism, the attack tactics continue to evolve, giving rise to new multi-team and multi-vector attacks.
The decoy
Large scale DDoS attacks slow down a company’s day-to-day operations, sometimes bringing them to a complete halt. During such an attack the whole IT team, often already thinly spread, can become completely engaged in restoring the infrastructure functionality, leaving other areas unattended.
However, a DDoS might be aimed at more than just disrupting service. In recent years we’ve witnessed cases where large service disruptions came in parallel with other attack vectors, where, whether intentionally or not, DDoS was used as a smokescreen, to pivot the defending team’s attention away from a more sophisticated and precise simultaneous offence, such as ATO (Account Takeover) or phishing.
Dispersing the fog
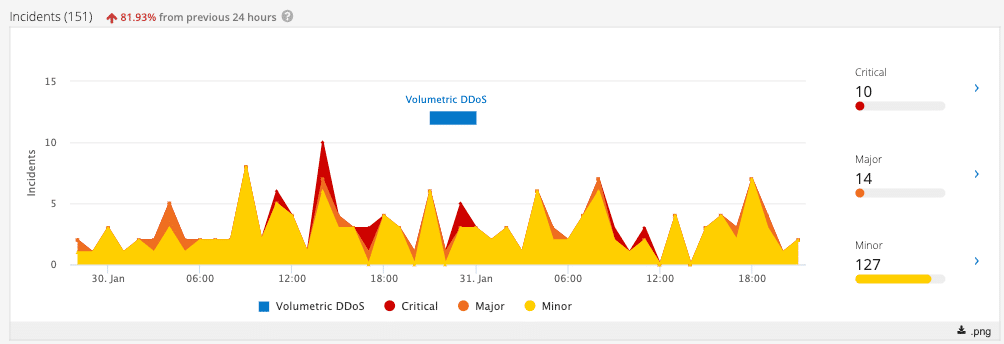
With Imperva Attack Analytics, we evaluate and distil thousands of application layer security events into a few readable security incidents.
A novel feature that Imperva Attack Analytics offers customers is an indication of network layer DDoS attacks correlating to incidents in the application layer.
Full details can be found here, but essentially, clicking on a network layer DDoS incident (marked blue on the chart) navigates to a list of other incidents that took place before, after, or during the DDoS attack in question.
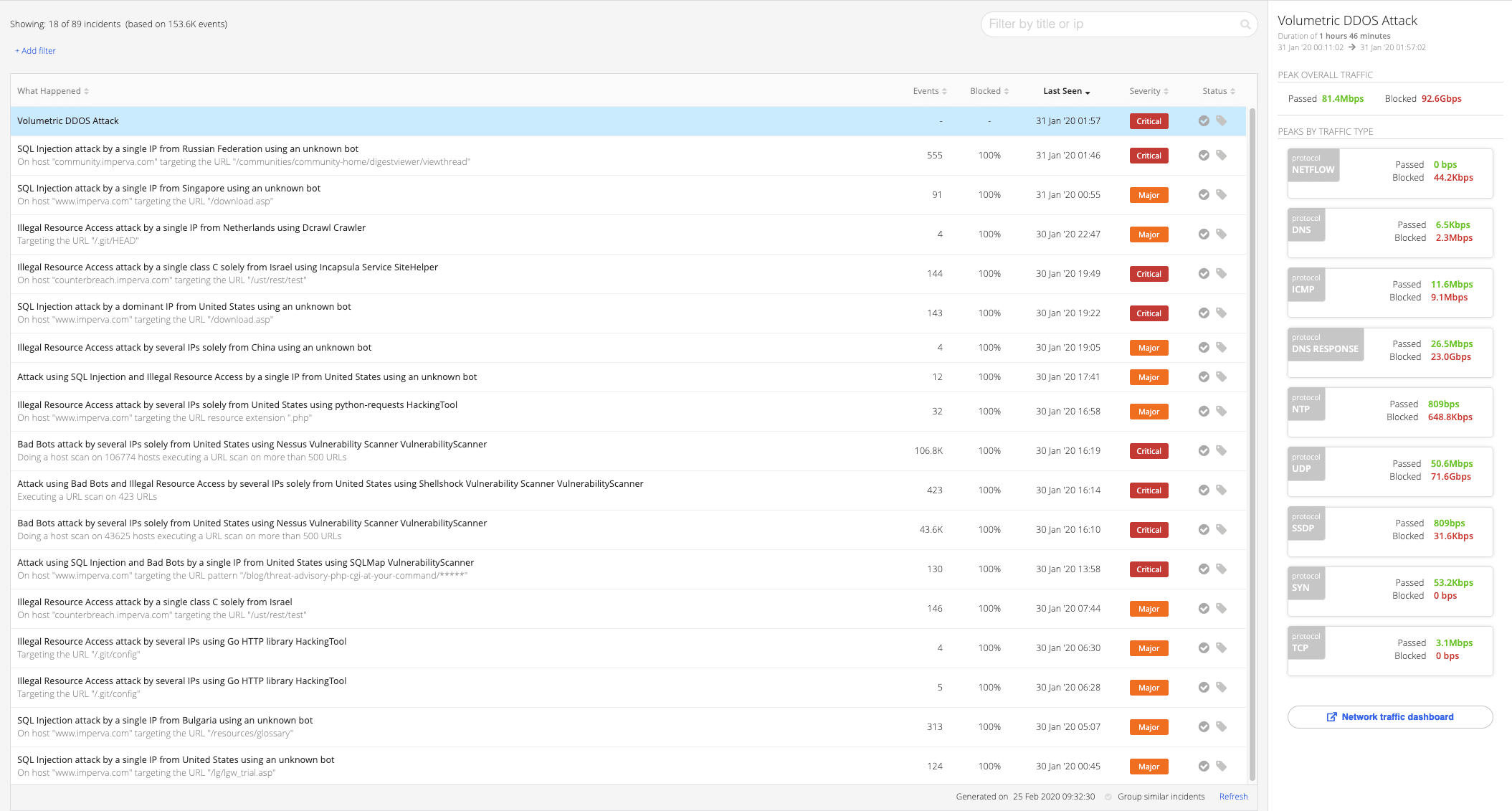
** This image depicts SQL injection attack done in parallel with volumetric DDoS attack, both blocked by our Cloud WAF
This allows us to track harmful cyber activities which might otherwise have been obscured by a massive flow of DDoS events and possibly identify these events as being a part of a single malicious act.
Since some network layer DDoS incidents might, in fact, be large application layer DDoS incidents, analyzing them as such provides more detailed information on an attacker’s identity, location and tools than treating them as plain layer 3 denial of service.
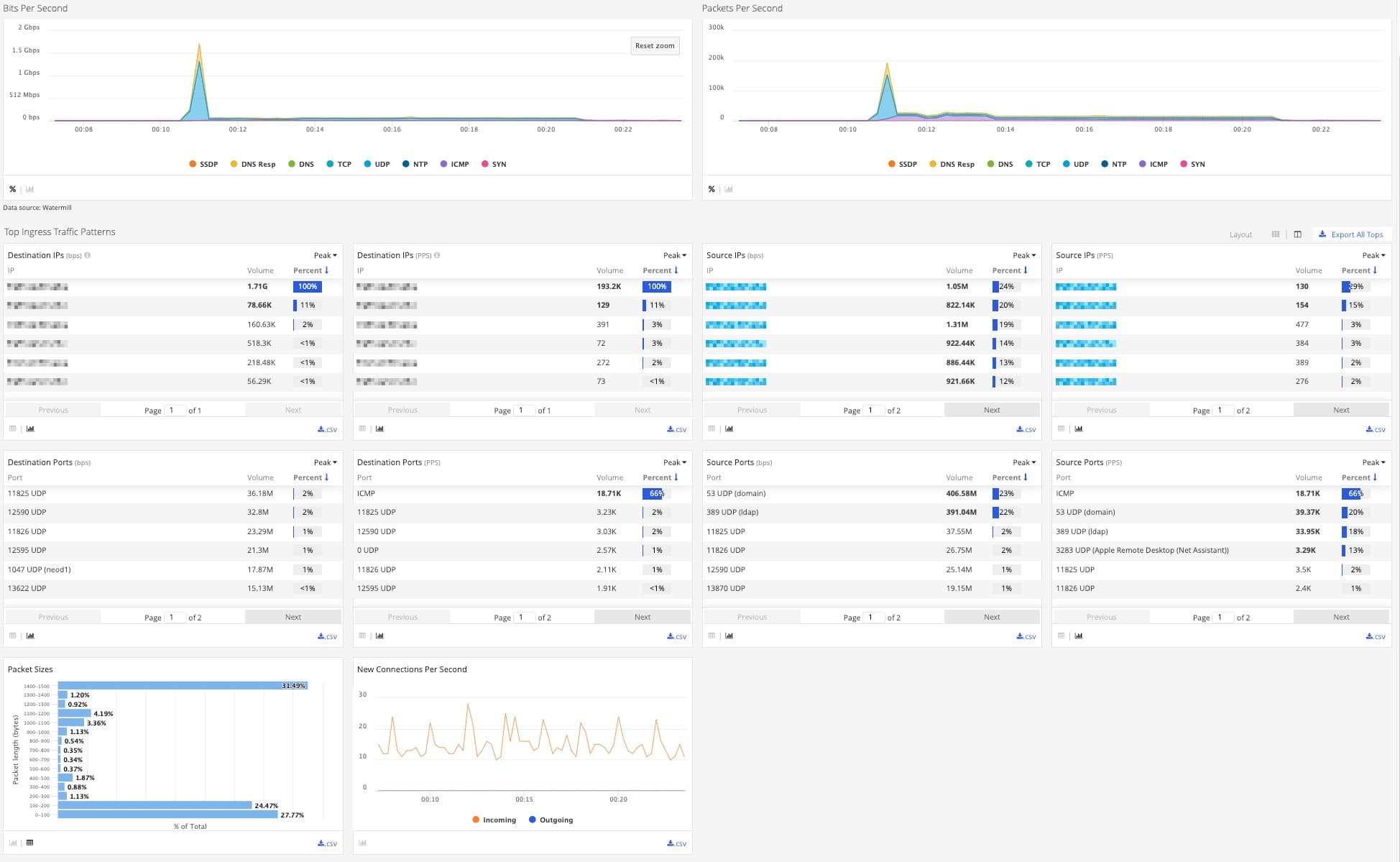
Basic technical details of the attacked protocols and their bandwidth peaks can be obtained from Attack Analytics incident details view.
More advanced investigation tools are available at the Infrastructure Protection dashboard, allowing for further DDoS analysis.
How to proceed from here
If you experience volumetric DDoS attacks and are an existing Attack Analytics customer, log into your account today and learn more about the DDoS attack itself and its surroundings.
If you’re not currently an Imperva customer or would be interested in learning more, you can request a demo.
Protect your business for 30 days on Imperva.Try Imperva for Free