As part of Imperva’s Security Labs’ ongoing efforts to monitor and report on the current Application and Data Security Threat landscape, we studied and analyzed over 100 of the largest and best-known data breaches of the last decade. Download the full report, Lessons Learned From Analyzing 100 Data Breaches here.
To get maximum value from the analysis of these breaches, Imperva researchers extracted each initial breach, the target of each breach, the system that was compromised by the breach, and what records were stolen in the breach. It is important to understand that because of their sensitive nature, database security breaches often go unreported. Also, in many cases, there isn’t enough data available to provide a comprehensive report.
Imperva researchers gather data from all the available information sources; the web, breach reports, hackers’ forums, analysis of stolen database dumps, and information gathered from deploying bad-actor traps and honeypots.
In this post, we’ll reveal what specific types of data were stolen.
Hackers can only steal data that is available for them to take. Our research found that nearly 75% of the stolen data is PII (Personally Identifiable Information). Over 15% of the breaches resulted in credentials being stolen, and more than 10% resulted in the theft of credit card details.
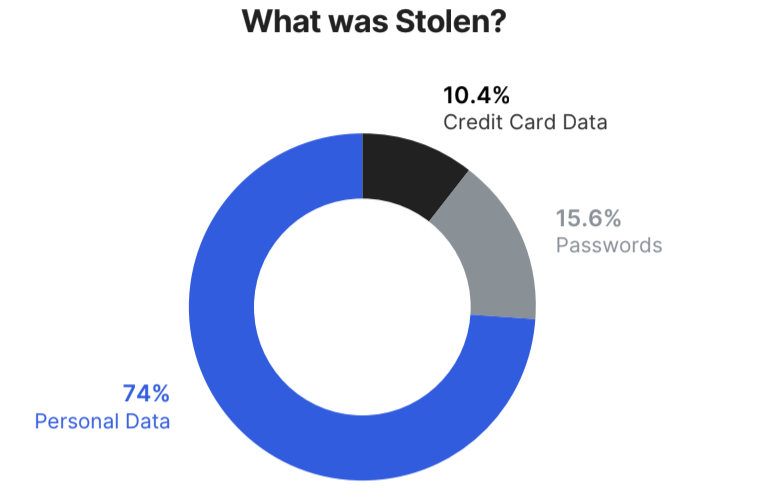
Figure 1: Chart describing the distribution of stolen data types.
Protect your PII
Widespread theft of PII is a strong indication that many organizations are not putting enough protection into place to secure it. Some of this is due to PII being regularly transferred between systems, people and suppliers to perform common business tasks. As regulations governing data privacy get tougher, it will be critical for organizations to discover, identify, and classify PII across their data estate. Only when you know where the PII is hosted and what applications and users are accessing it, will you be able to extend the security controls that protect it.
The data suggest that credit card details are the most vigorously protected data set of the three, and more intensely sought after as it is in high demand on the dark web.
In future posts, we’ll see what the research reveals regarding what are the root causes of breaches, which public cloud services are breached most, and what the trends are in the average volumes of stolen records.
In the meantime, please take the opportunity to learn more about how Imperva delivers analytics, protection and response across all your data assets, on-premise and in the cloud – giving you the risk visibility to prevent data breaches and avoid compliance incidents.
Nearly 75% of stolen data is personal data
Imperva Data Privacy enables complete and automatic visibility through a single UI into all data and user activity at the database level. With this solution, discovering and classifying personal data and PII in both structured and unstructured data sources, on-premise or in the cloud, becomes much easier and faster. The solution constantly scans your entire data estate looking for correlated attributes of sensitive data that constitute PII so you can protect it.
Learn more about the Imperva Data Privacy solution section here.
Try Imperva for Free
Protect your business for 30 days on Imperva.













