Consider for a moment that an army of bots is setting their sights on your website. They target your login page and hammer it with millions of requests in an ongoing attack that lasts days, raising your infrastructure and fraud prevention costs. Would this frighten you? What if this barrage of bots were causing business-wide problems with no end in sight and you didn’t have tools to effectively block them? This is the nightmare of security practitioners everywhere.
The highly sophisticated bad bots (more on them later) in this scenario that are attacking your website are testing stolen credentials in a malicious attempt to gain access to user accounts, a method known as Credential Stuffing. If these attempts are successful, they will cause substantial damage to your business and brand reputation, which will prove to be far more damaging than issues caused by minor downtime.
This nightmare was a reality for one financial services enterprise. Read on to learn what happened.
Imperva recently detected and mitigated the largest, longest lasting Account Takeover (ATO) attack it has ever recorded. This attack targeted the login endpoint of one particular digital banking service provider, resulting in over 500 million malicious login requests over the course of three weeks, peaking at over 25 million malicious login requests per day!
The timeline of events
The campaign began on July 8th, when the attackers made their first attempt to exploit the website, indicated by the short, yellow colored spike in the image below. We believe this attempt was a trial run, meant to evaluate the target and learn whether or not it was sufficiently protected. Having seen that none of these ATO attempts had been mitigated, the malicious actors then proceeded to launch their full scale attack on July 10th.
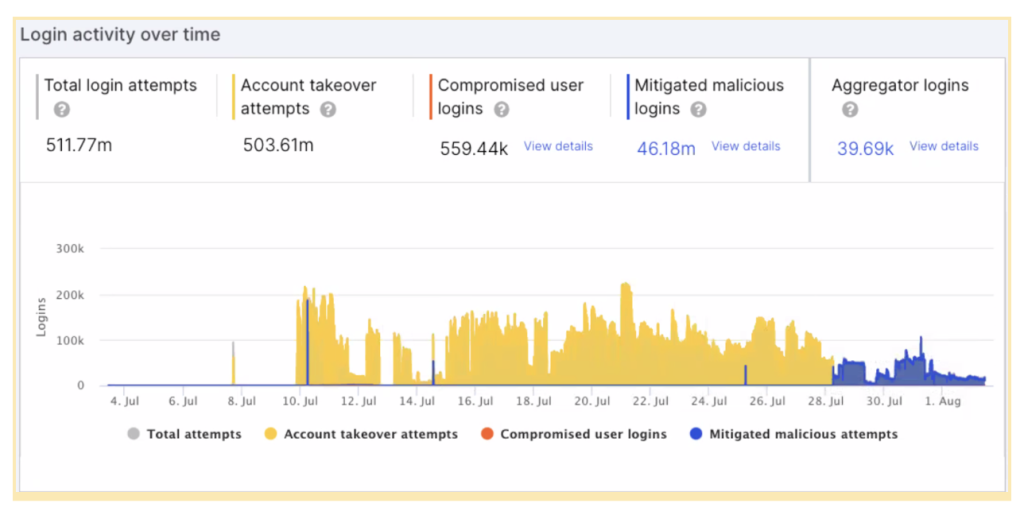
Answering common questions
You might notice from looking at the chart that there is a gap between when the attack began and when the customer enabled mitigation. They had to go through various approvals internally, and some of those required that some questions will be answered before turning on mitigation. This is understandable and something that many customers deal with, especially considering their size and industry. Let’s address some of the common questions about mitigating requests on the login page:
- “How do I know for certain that this is an attack?”: Imperva is able to accurately determine if the requests to the login page have the characteristics of an account takeover attempt. It does so through a multilayered process which includes reputational analysis leveraging crowdsourced data, an advanced client classification engine, and proprietary algorithms developed by Imperva which include behavioral analysis models. Imperva’s platform approach allows us to crowdsource data from attacks we are seeing across our global network of customers and use it to fine tune our algorithms, so that all customers benefit from that.
- “I can’t afford to block legitimate traffic.”: Similar to the previous answer – Imperva’s ability to determine if the interactions with a website have the characteristics of an account takeover attempt with pinpoint accuracy means none of your legitimate users will be blocked. Furthermore, Account Takeover Protection is tuned for success right out-of-the-box, ensuring your business-critical traffic will not be affected in any way.
- “Will this impose any friction on my customers?”: No, our multilayered detection approach provides laser-focused detection with minimal false positives, reducing the need to use CAPTCHA challenges and preserving the user experience.
- “Will there be any added latency?”: No, Account Takeover Protection is deployed across the Imperva global network, leveraging our robust Content Delivery Network (CDN) which offers the best in speed, performance, and resilience. This, combined with ATO’s advanced detection, guarantees that malicious logins are immediately mitigated closest to where they originate, long before they even have a chance to reach your infrastructure.
During the attack, Imperva’s account team worked closely with the customer to alleviate any concerns. They Periodically enabled Account Takeover mitigation to test how it affected their website, these are indicated by the blue spikes amidst the yellow attack traffic. Once their concerns were addressed by the account team, the customer fully configured ATO mitigation on their site.
Mitigating the attack
Once mitigation was fully enabled, Account Takeover Protection immediately kicked into action, blocking the attack traffic, which can be seen turning from yellow to blue, all while allowing legitimate users to continue logging into their accounts without disruption. In this case, the customer is using ATO’s “out-of-the-box” recommended mitigation strategy, which is ‘Block’ when a login is classified as ‘High’ risk, and do nothing for ‘Low’ and ‘Medium’ risk. This further demonstrates the high confidence of ATO’s detection, as the customer was not experiencing false positives. Even while under a heavy, consistent ATO attack, they still didn’t need to mitigate logins classified as ‘Low’ or ‘Medium’ risk.
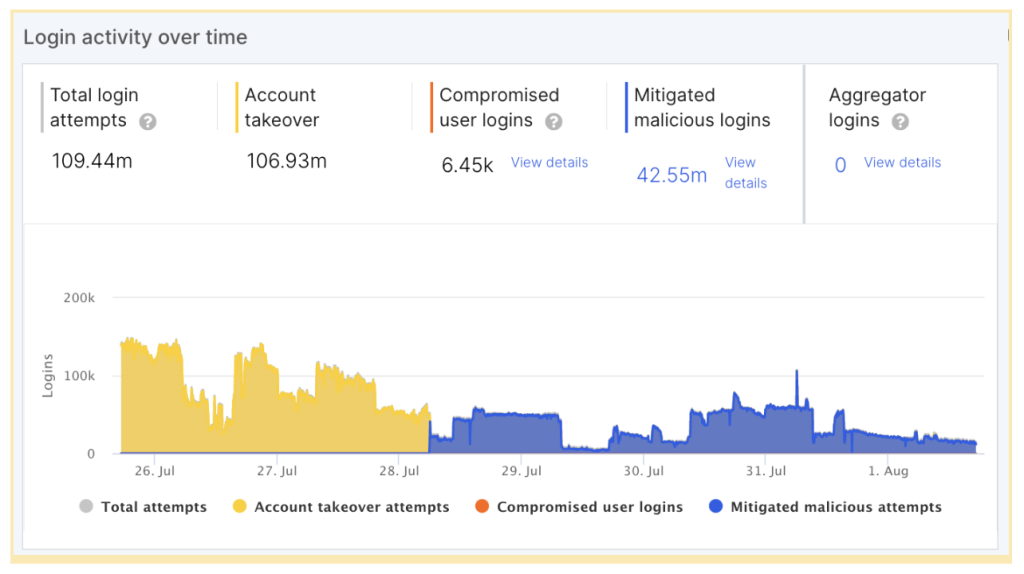
As a result of the customer enabling mitigation, the attack began to subside. This can be explained by the fact that more often than not, attackers prefer to target low-hanging fruit; if a site is not protected, they will keep attacking until they get whatever they’re after. However, if they come across a website that’s well protected, they eventually give up as this is not profitable for them to continue spending time and resources on it. The ability to deter attackers and lower the ROI of their attacks is the main reason why Account Takeover mitigation should always be enabled, rather than only when under attack.
The increasing sophistication of bots
Over the past couple of years, we have observed an increase in the sophistication of bad bots. This is reflected in the technologies and methods they use to evade being detected while still maintaining persistent attacks on their target. These technologies include frequently cycling through IP addresses, hiding behind anonymous proxies and peer-to-peer networks, manipulating their login parameters and cookies to make it appear as if the requests are being made from different browsers, changing their user agents, and more. Bad bots can even evade or defeat CAPTCHA challenges through integrations with various tools and platforms such as Death by Captcha and 2Captcha.
Mitigate account takeover attacks and prevent account based fraud with Imperva
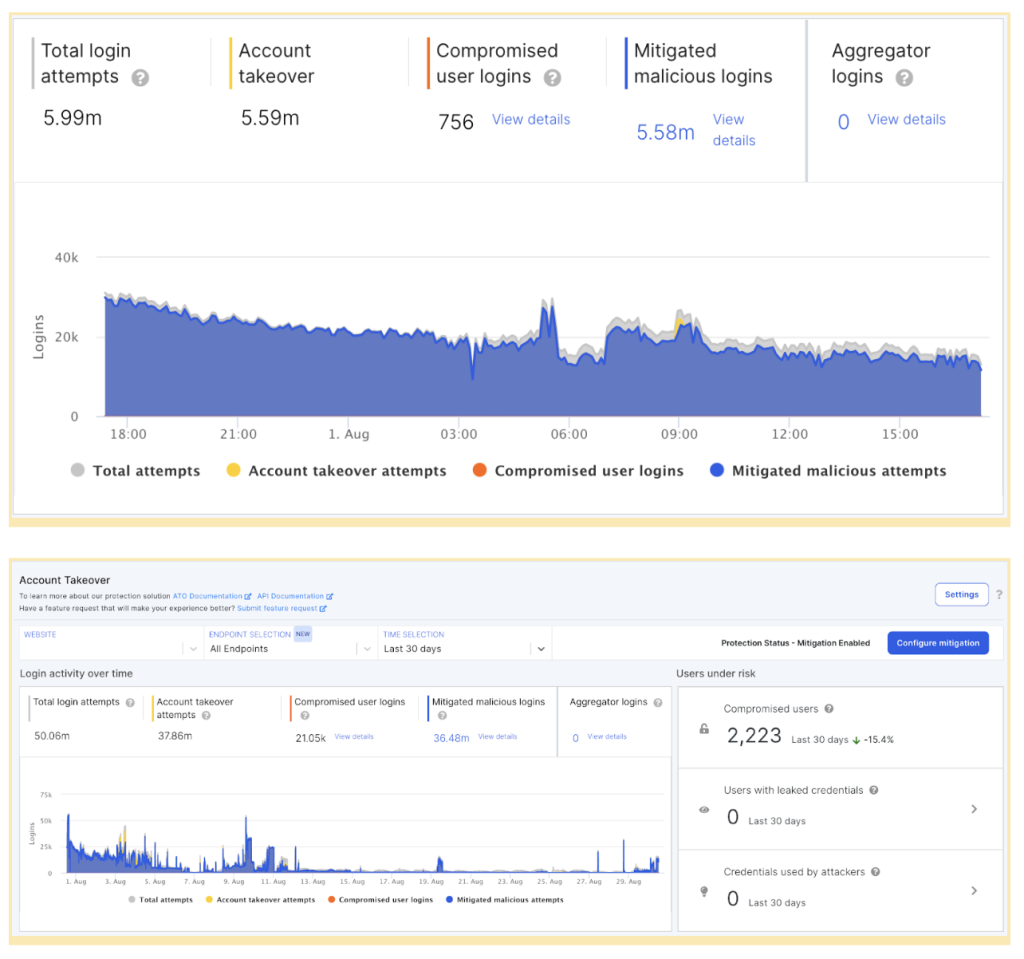
Imperva Account Takeover Protection provides login protection without affecting legitimate user traffic in the process and with no added latency. It does so by accurately determining if the interactions with a website have the characteristics of an account takeover attempt with pinpoint accuracy, stopping malicious account takeover attacks long before they even have a chance to reach your infrastructure. Account Takeover Protection enables fraudulent behavior investigation and detection by bringing the focus to the login functionality as a whole. The intuitive dashboards provide clear visibility and actionable insights into attack attempts, leaked user credentials, compromised user accounts and successful login attempts, while user behavior anomaly detection points out accounts at risk of fraudulent activity.
Account Takeover Protection is part of Imperva’s market-leading Web Application & API Protection (WAAP) solution. Start your Application Security Free Trial today to protect your login pages.
Try Imperva for Free
Protect your business for 30 days on Imperva.













