CVE-2021-44228 is a high profile vulnerability impacting multiple versions of a widely distributed Java software component, Apache Log4j 2. The specific vulnerability allows for unauthenticated remote code execution. For additional technical information, the team at LunaSec has an excellent technical writeup on their blog.
In terms of magnitude, this will without any doubt, have a big impact on all organizations running Java workloads. Similar to other common vulnerabilities and exposures (CVEs) in its class (referring to those affecting Struts 2 back in 2017), best practices require security teams to immediately patch their software and upgrade third-party components to meet SLAs.
In the spirit of transparency, we want to give everyone a succinct update on how Imperva responded and is continuing to focus on this specific CVE.
Imperva Threat Research Response & Observations
Imperva Threat Research sprang into action shortly after this zero-day exploit was made public. We saw initial attacks attempting to exploit this CVE starting around December 9, 2021 18:00 UTC.
Existing security rules put in place for Imperva Cloud WAF customers appear to have mitigated these early CVE attacks without requiring any patching.
Imperva Threat Research detected new CVE-specific attack variants, resulting in the creation of additional security rules on December 10, 2021 5:41 UTC. These updates were tested and deployed to the Imperva Global Network and ThreatRadar Feed on December 10, 2021 11:44 UTC.
Throughout the day, more attack variants were detected, resulting in the creation of additional rules and a deployment on December 10, 2021 22:46 UTC.
As of writing this blog post, and since rolling out the updated security rules more than 13 hours ago, Imperva has observed 1.4M+ attacks targeting CVE-2021-44228.
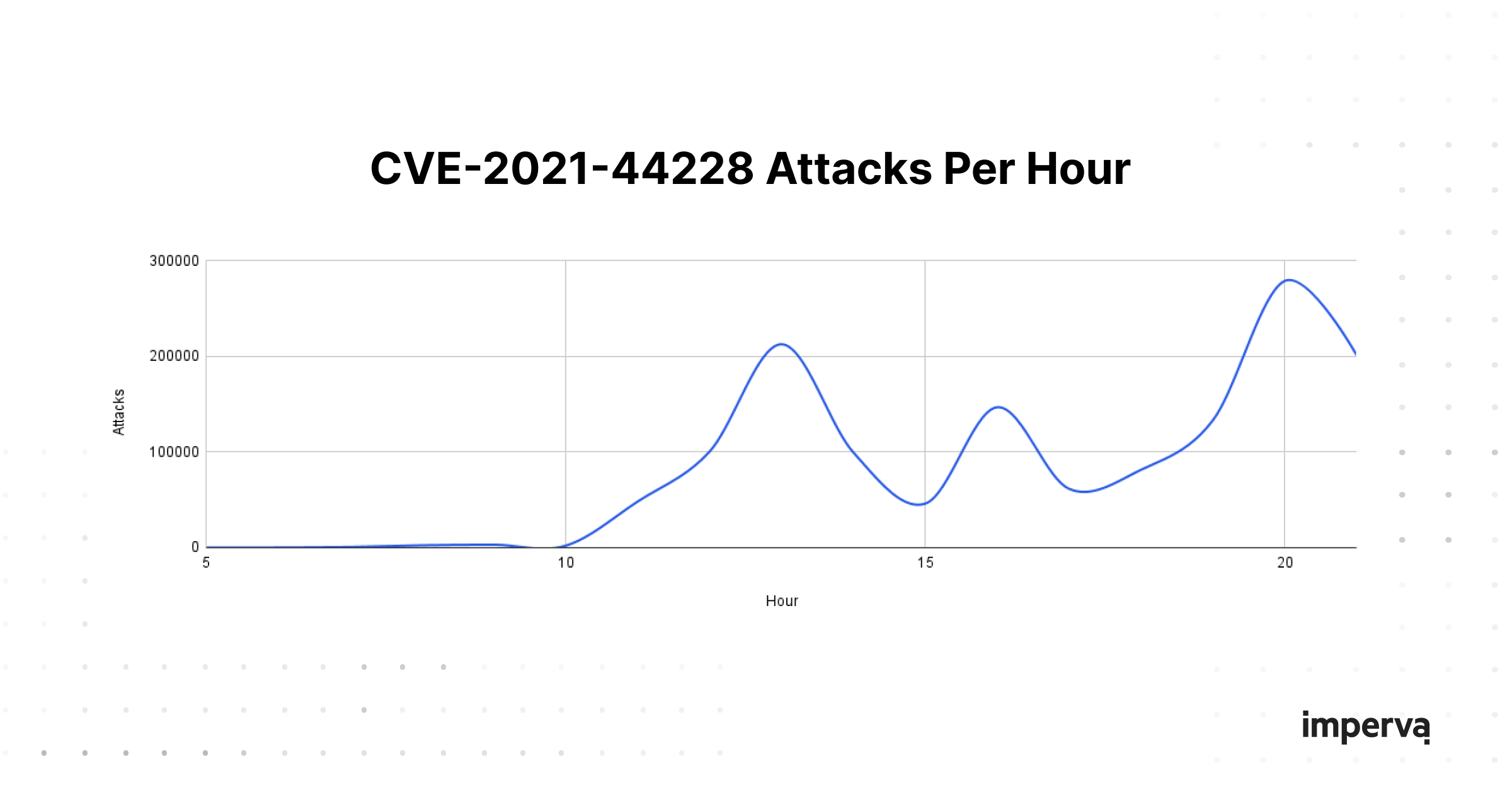
As you can see from the graph above, we’ve observed peaks reaching roughly 280K attacks per hour. As with other CVEs in its class, we expect to see this number grow, especially as new variants are created and discovered over the coming days and weeks.
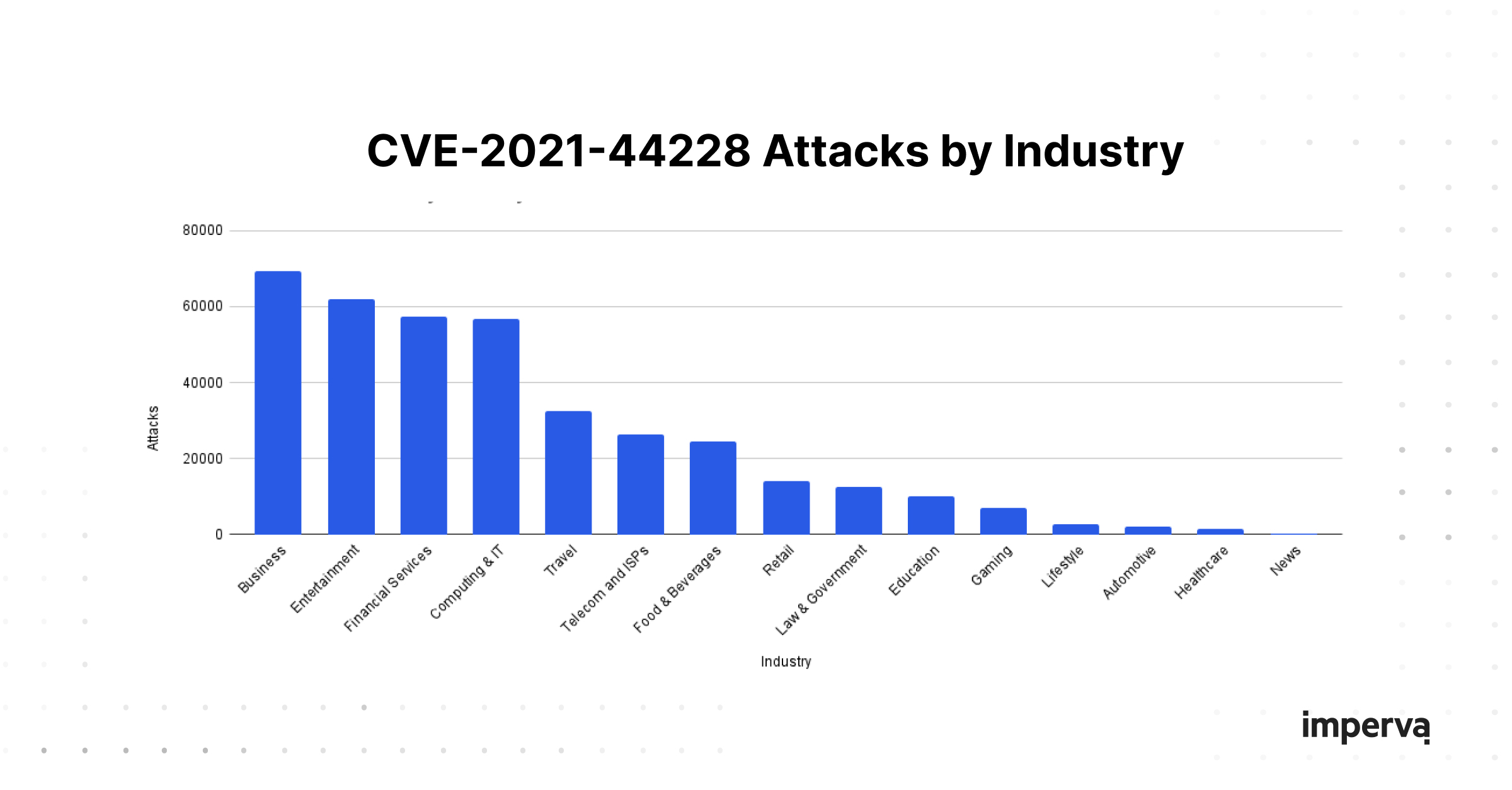
Another interesting property of this particular attack is the normal distribution across industries, which makes sense as Java is a very popular language for building applications and APIs.
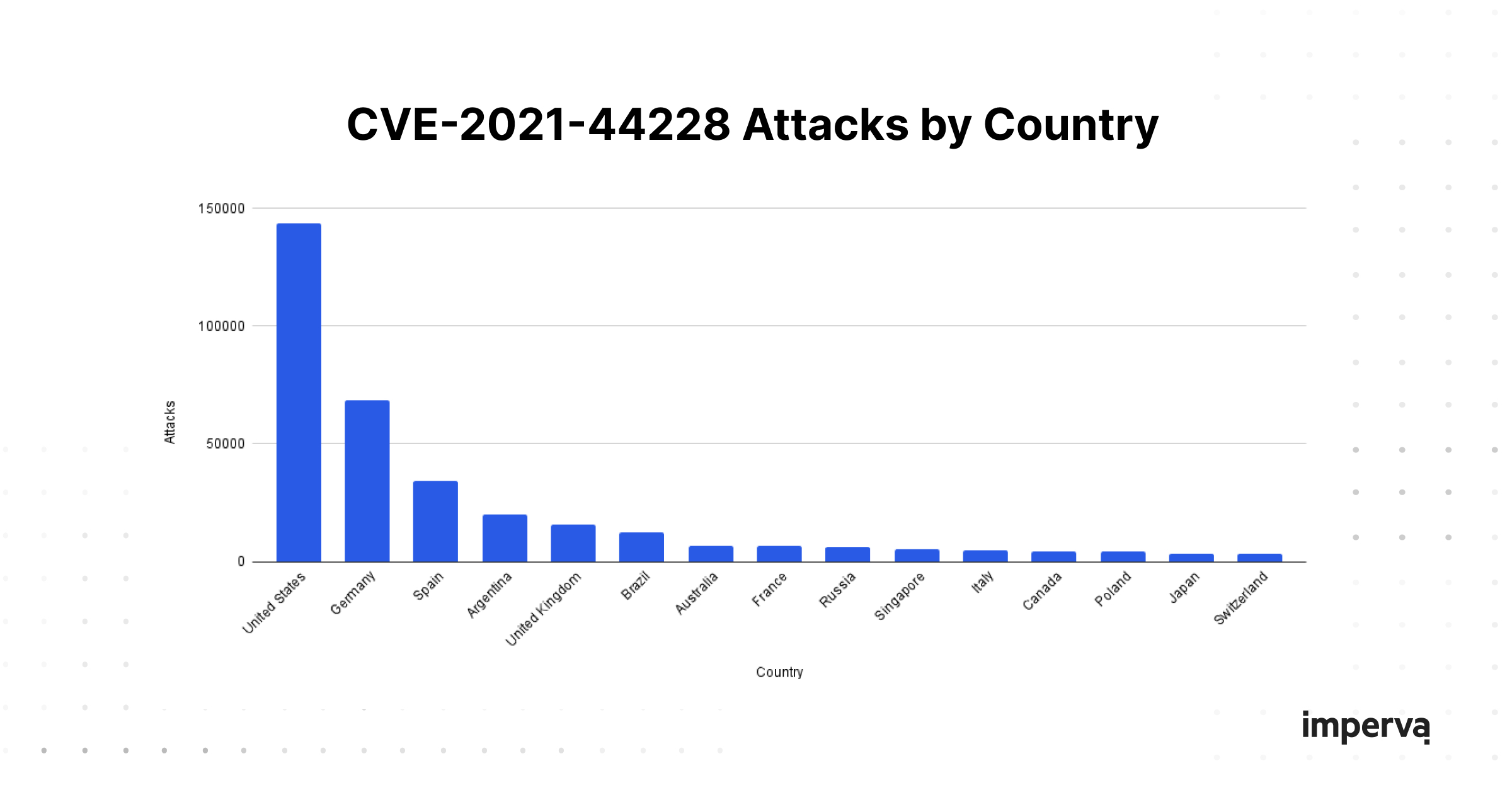
Looking at the distribution of attacks by country (illustrated above), there is nothing abnormal and furthers our hypothesis that the attacks are trying to exploit a vulnerability versus targeting specific industries or countries.
Another Strong Case for RASP
In 2018, Imperva acquired Prevoty, the market and analyst-recognized leader of runtime application self-protection (RASP). The rationale behind the acquisition was that organizations would want to have last-mile protection for applications and APIs, particularly as they became more dynamic and dependent on third-party software components.
As the lifecycle of CVE-2021-44228 is getting started, we can’t help but be reminded of the myriad of Struts 2 CVEs from 2017. Similarly, organizations of all sizes are going to be forced to identify and patch first and third-party applications and APIs.
We also recommend that customers implement RASP as part of a broader defense-in-depth strategy for protecting their applications and APIs. Some of Imperva’s customers, including eCommerce and telco providers, have been able to save thousands of hours in emergency patching and speed up the secure software development lifecycle. Customers that have Imperva RASP deployed across their Java applications are protected from RCEs related to CVE-2021-44228.
Ongoing Vigilance
Imperva Threat Research is continuing to monitor, create, test and deploy CVE-specific security rules based on new attack variants for all of our customers. We will keep all our customers notified as this progresses.
For customers looking for support please access the Imperva Support Portal.
If you’re looking for protection from CVE-2021-44228, please contact us.
Try Imperva for Free
Protect your business for 30 days on Imperva.












