In a world where DevOps is oiling the wheels of accelerated software development, it’s hardly surprising that automation, code re-use and third-party libraries are integral parts of our high-speed app development cycle. But what happens when the pace of development outstrips security? Or when the tools that help you go faster become vulnerabilities themselves?
For these new attack vectors, traditional protection mechanisms like perimeter and endpoint security either can’t be deployed or are ineffective. Even organizations with secure coding practices can struggle to manage risk in their software supply chain and development processes.
Code dependency
An estimated 90% of security incidents begin with exploits against defects and vulnerabilities in the design or code of software. When most of your software isn’t really yours – as much as 97% of enterprise codebases are open source, with an average 203 dependencies – it’s no surprise that attackers are increasingly looking for ways to exploit vulnerabilities in the same code you’re using to accelerate DevOps and digital transformation. According to GitHub, there’s a 59% chance of you getting a security alert in the next year from an active repository.
Factor in the compilers, APIs, build systems and the rest of your technical stack and you’re looking at a massively connected, complex system. In this environment, managing application vulnerabilities is a massive challenge. How do you prioritize which ones to fix? How do you know which ones put your applications at risk? How many of your applications are based on open source, third-party software or other sources beyond your control? Do you have time to suspend workflows to patch a zero-day in a critical application? When you’re deploying software at such a fast pace, how is this code being protected from attacks?
According to Code Complete, every 1,000 lines of code has an average 1-25 errors. Where do you even start?
Mind the gaps
In this dynamic environment, traditional security approaches are ineffective. Perimeter security, static and dynamic analysis, and endpoint security variously rely on updates, can’t protect against zero-days or lack visibility into application attacks. For example, the backdoor code used in the SolarWinds attack could not be detected by static analysis, because it contained no errors.
Web Application Firewalls (WAFs) protect you from threats coming via web traffic, outside of the network; if you have compromised software within your trusted network (e.g. Exchange Server), the WAF can’t protect you, because that traffic doesn’t go through a WAF. Code analyzer tools do a great job of finding errors and vulnerabilities, but you still have to mitigate manually – a process that can take months.
A positive security model allows you to lock down software so it can’t do things it’s not expected to do. It allows you to ship applications that are secure by default, protecting the entire stack, including open source and third-party dependencies. Runtime Application Self Protection (RASP) is a positive security model that allows you to ship code that’s secure by design, mitigates risk, and gives you more time to patch/remediate vulnerabilities without interrupting workflows.
Mitigate now, patch later
RASP helps security teams keep up with the pace of DevOps while giving teams more flexibility and time to manage and fix vulnerabilities. It operates at runtime, from inside applications, and travels with your applications, wherever they operate. Even if perimeter defenses are breached and the application contains vulnerabilities, RASP can control application execution, block the attack and alert security teams. In this way, RASP acts as complementary to WAF; while the latter keeps known bad traffic out, RASP mitigates the risk posed by unknown exploits.
RASP protects against zero-days and the OWASP Top 10 application security threats, injections and weaknesses. Applications of all kinds are protected, secure by default:
- Active applications
- Legacy applications
- 3rd party applications
- APIs and Microservices
- Cloud applications
- Containers and VMs
RASP is tightly coupled with the application code and uses contextual awareness (as opposed to blocklists/allow lists) to detect threats and ensure a payload is unable to exploit any unknown part of the application code. Having ‘eyes’ inside your applications gives security teams insight into attempted attacks, the location of vulnerable code and metrics around users and origination – enabling better application development in the future, while giving enhanced threat insights.
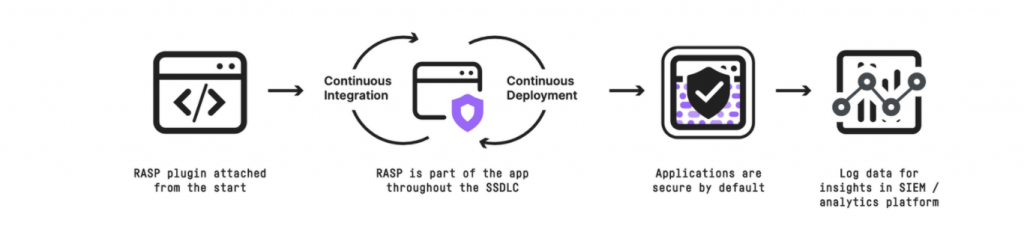
Security that travels with your applications – anywhere and everywhere
Imperva’s unique approach to RASP uses Language Theoretic Security (LANGSEC) as its mechanism for attack detection. Payloads (SQL queries, operating system commands, etc.) are evaluated in real time, within the entire application context and without the need for signatures or a learning phase.
To learn more about RASP and why Imperva was named a Leader in Omnia Market Radar for Next Generation Application Security: Runtime, download our report today.
Try Imperva for Free
Protect your business for 30 days on Imperva.














