Introduction
Cybersecurity experts are on high alert, as the 2024 Olympic Games continue over the coming weeks. Historically, the Olympics have been a prime target for cybercriminals, state-sponsored actors, and hacktivists. The convergence of global attention, vast amounts of sensitive data, and extensive digital infrastructure creates a perfect storm for potential cyber threats.
Previous Olympic Games have experienced a variety of cyber threats. The 2018 Winter Olympics in Pyeongchang, for instance, was targeted by the Olympic Destroyer malware, which disrupted IT systems during the opening ceremony. Similarly, the 2016 Rio de Janeiro Olympics faced numerous phishing attacks, data breaches, and attempted financial fraud in connection with the Games, as well as a DDoS campaign leading up to the events.
The primary targets during the Olympics typically include official websites, live streaming services, ticketing systems, and critical infrastructure such as transportation and power grids. Additionally, athletes, sponsors, and spectators may also be targeted through social engineering and phishing schemes.
Based on previous incidents, here’s what we can expect in terms of cyber threats at this year’s Olympics.
What We Expect To See
There are several attacks we expect to see during this year’s Games.
Ransomware Attacks: Given the rise in ransomware incidents globally, it is likely that attackers will attempt to disrupt Olympic operations by encrypting critical systems and demanding ransoms. The high stakes and visibility of the event make it an attractive target for such attacks.
State-Sponsored Espionage: Like the Russian state-sponsored hackers who targeted Pyeongchang, state actors may use the Olympics as an opportunity to conduct espionage, targeting sensitive communications, strategic plans, and personal data of high-profile individuals. The goal may range from intelligence gathering to attempting to influence outcomes or create political tension.
Distributed Denial of Service (DDoS) Attacks: DDoS attacks, which overwhelm servers with traffic, are a common tactic to disrupt services, as seen in Rio de Janeiro. These attacks could target live streaming platforms, ticketing websites, or other critical online services, causing frustration and financial loss.
Phishing and Social Engineering: Cybercriminals are likely to exploit the excitement and urgency surrounding the Olympics to craft convincing phishing emails and social engineering schemes. These could target attendees, athletes, or even officials, aiming to steal credit card information or distribute malware.
Supply Chain Attacks: The complexity of the Olympics involves numerous vendors and partners. Cyber attackers may attempt to infiltrate less secure elements of the supply chain to gain access to core systems. Ensuring robust security practices across all partners is essential to mitigate this risk.
Insider Threats: With a vast amount of personal data being processed, from athlete information to attendee details, access to this information by those with malicious goals is a significant threat. Unauthorized access to this data can lead to privacy violations, identity theft, and financial loss.
What We’re Seeing
We’ve observed a surge in cyber threats targeting sites directly related to the Olympic Games and related industries such as Sports and Travel. Notably, vulnerability scanner activity on Olympic sites has skyrocketed, with a staggering 770,000% increase in scanning activity from June to July. This uptick highlights the growing interest of malicious actors in exploiting any potential weaknesses. Additionally, we’ve detected a rise in the use of automated tools on these sites, which has primarily led to attempted instances of data leakage, Remote Code Execution (RCE), and DDoS attacks.
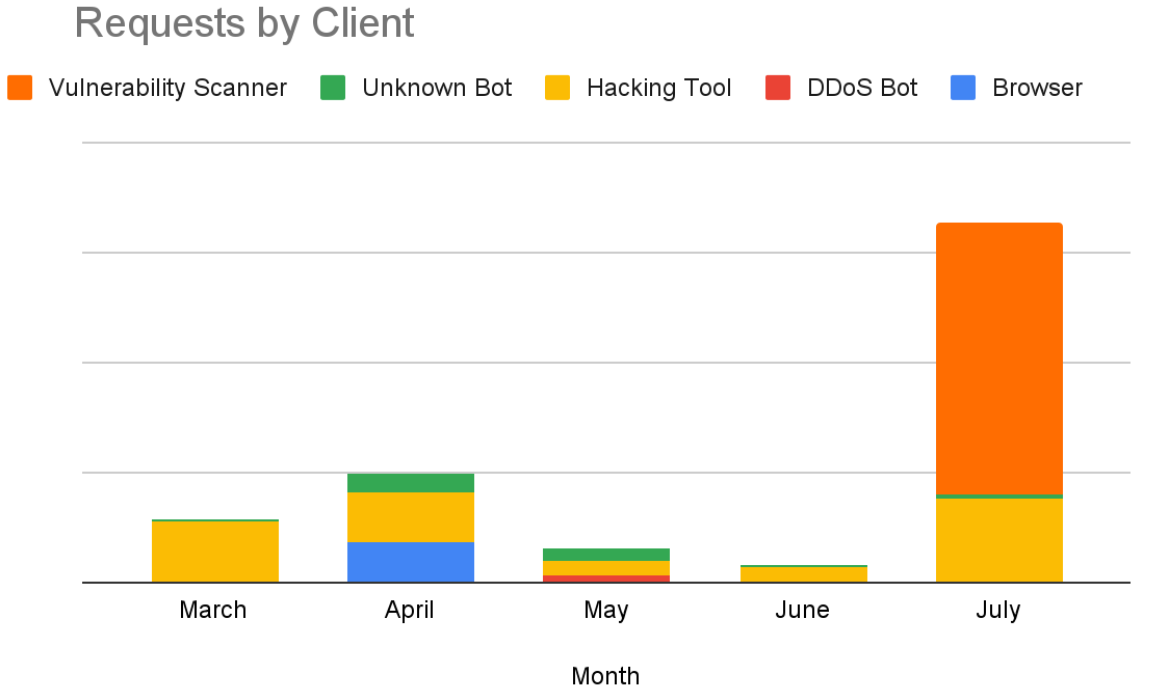
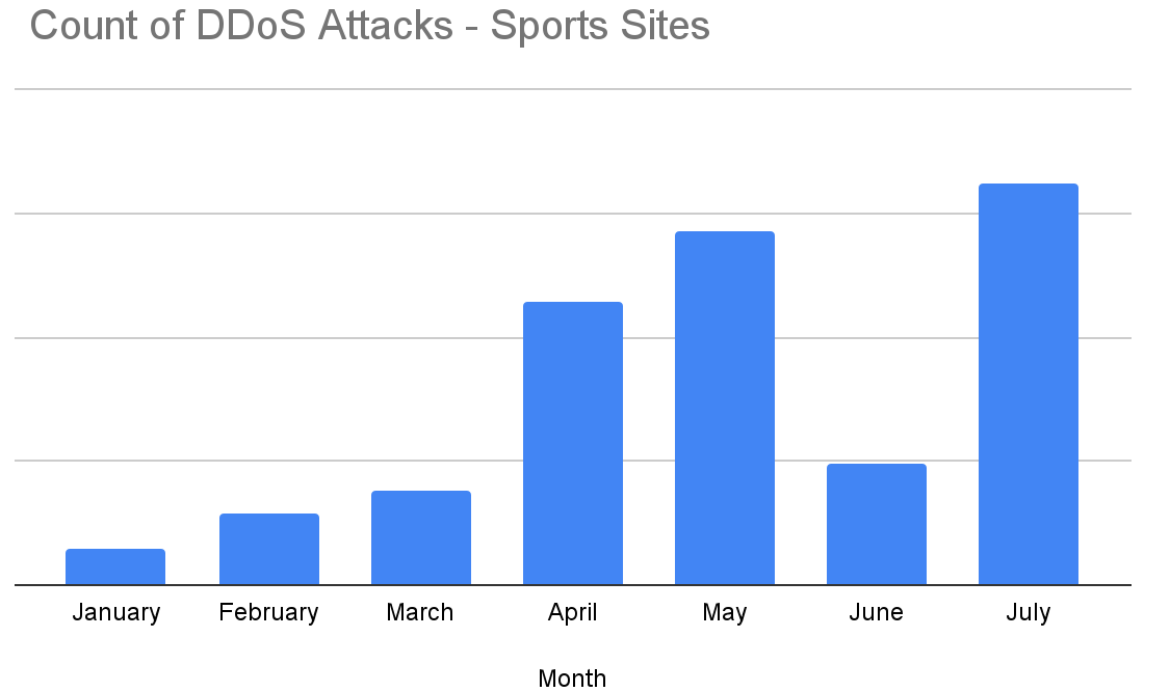
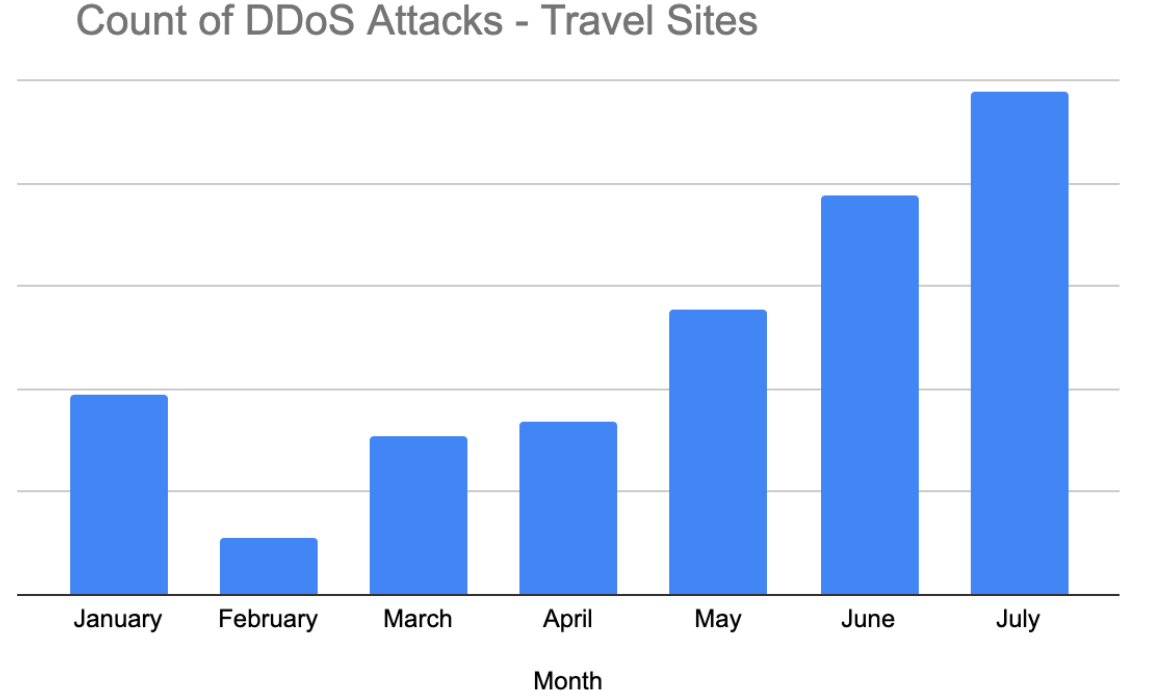
The frequency of DDoS attacks on Sports and Travel websites also increased – 230% for Sports and 31% for travel – as the Olympics drew nearer. While some of these attacks may not be directly related to the Games, the timing suggests that attackers are exploiting the heightened traffic and visibility of these sites to maximize disruption and reputational damage.
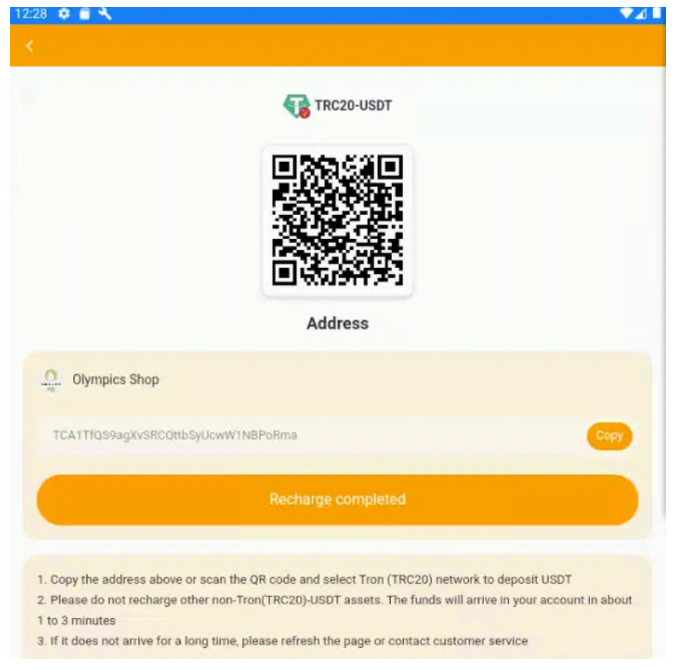
Social engineering attacks are particularly prevalent during high-profile events due to their widespread recognition and the public’s heightened interest. For example, a malicious application called Olympics Shop has started to spread. It leverages the official Paris Olympics logo, and claims support from official Olympics associations, in order to gain trust from the potential victim and ultimately enroll them in a financial scam.

Main activity of the fraudulent application including official logo

Claim of support from official Olympics associations
Finally, the request to invest in the financial scam:
Threat actors are beginning to target Olympic athletes as well. Notably, a new attacker identifying as Zeus, and reportedly of Iranian origin, has begun publishing personal information about Israeli athletes participating in the Games. This data includes family relationships, photos, phone numbers, email addresses, and other sensitive details. For one athlete, Zeus posted what appears to be access to their email account and financial information, highlighting a severe breach of privacy and security.
Conclusion
As the world participates in the excitement and spectacle of the Olympic Games, it is crucial to remain vigilant against the backdrop of evolving cyber threats. By learning from past incidents and implementing comprehensive security strategies, organizers can help ensure that the focus remains on the athletes and the spirit of the competition, rather than on disruptive cyber events. Stay tuned for a second installment in this series after the Games, where we break down what we saw during the events.
Try Imperva for Free
Protect your business for 30 days on Imperva.










