There’s no doubt that cybercrime is on the rise, and bad actors are constantly on the lookout for vulnerabilities. In the first half of 2020 data breaches exposed over 36 billion records. Attacks are becoming more wide-spread and more prolific.
Malicious hackers are exploiting zero-day vulnerabilities in new iterations of software, like the recent exploit of the popular File Transfer Appliance (FTA) from enterprise firewall company Accellion, to collect passwords and gain account access to company systems. The Accellion tool, which was vulnerable for an estimated 72 hours, continues to hit hundreds of high-profile targets from Harvard to Kroger and CSX to Flagstar Bank.
In 2020 the average ransomware demand rose by 33% (over the previous year) to $111,605 while the average cost of a data breach totaled US$3.86 million.
As an example, in a recent separate incident, Foxconn (the global electronics giant) was the target of a ransomware attack that encrypted 1,200+ servers, locked over 100 GB of unencrypted files, and deleted nearly 30 TB of backup data (a terrifying growing trend). The attackers demanded more than 1,800 BTC - approximately US$90 million at today’s exchange rates - for access to the decryption tool.
Attacks like this are happening daily, so what can companies do to stay safe in a world where there is a malicious attack against your computers every 39 seconds?
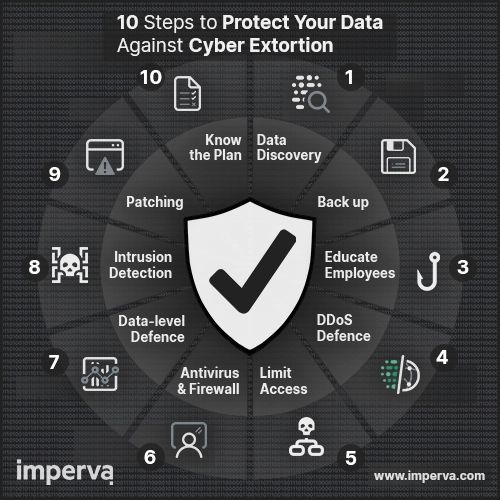
Here are ten steps to help protect your data against cyber extortion
- It’s all about the data: An organization can’t know how they’re at risk without knowing the amount and location of their data. “Where is my sensitive data?” should be the first question you must be able to answer.
- Back up. Back up. Back up: Being ready and being safe is the ultimate fallback if an extortion scam happens. Being able to roll back the clock is the best precaution possible. Spreading those backups around and ensuring their security is becoming CRITICAL.
- Educate employees about phishing: Human error accounts for 95% of cybersecurity breaches. All staff should be cybercrime-savvy and briefed about protecting the data they handle. This is a major way to reduce potential risk.
- DDoS (Distributed Denial of Service) defense: It’s important to have the ability to absorb or avoid malicious attacks designed to overwhelm or slow-down your systems. Taking away access to your data isn’t the only way cybercriminals hold businesses hostage.
- “Need to know”-only: Limiting employees’ access to systems and documents, especially sensitive information, bolsters legal compliance and narrows accountability.
- Strong antivirus and firewall software: The right antivirus protection helps to protect the file system against unwanted programs, while your firewall helps keep external threats from getting access to your system to begin with.
- Data-level defense: How is your data being used and by whom? You should be continuously analyzing data usage patterns so you can identify potentially suspicious activity and stop it before it becomes a breach event.
- Intrusion detection tools: It’s great to have data breach prevention and detection tools, but are employees monitoring them? It’s important to prevent a breach, but if a breach occurs it’s CRITICAL to be aware as soon as possible.
- Patching: Set a scheduled routine for patching your systems and regularly review them for patch management requirements.
- Know the plan: How will your IT security team manage a data breach if one occurs? Knowing who is part of the incident response team, and their responsibilities, is key to a fast and effective response. Create an incident playbook and stick to it.
If you’re looking for more advice on avoiding cyber extortion, we have specific recommendations and case studies for a wide range of business sectors at www.imperva.com.
Try Imperva for Free
Protect your business for 30 days on Imperva.












