Imperva’s report, The State of Vulnerabilities in 2020 has revealed that unlike in previous years, researchers observed a fall in the number of vulnerabilities last year, even as businesses were compelled to accelerate digital transformation processes due to the COVID-19 pandemic. Vulnerabilities are defined as the gaps or weaknesses that undermine an organization’s IT security efforts, such as a firewall flaw that enables hackers into a network.
The overall number of new vulnerabilities in 2020 (23,006) was down by 2.04% compared to 2019 (23,485) and by 0.86% compared to 2018 (23,207).
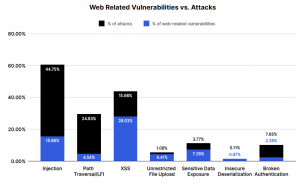
According to the report, the dominant root cause of vulnerabilities was cross-site scripting (XSS) with injection as the second-most dominant root cause. Drilling down into the report data, the researchers note that a large percentage of this appeared to be related to SQL injection. While XSS was the dominant root cause of vulnerabilities, most of the attacks in 2020 were related to injection vulnerabilities rather than XSS. Only 15.68% of the attacks that Imperva registered were related to XSS. On the contrary, the injection vulnerability category appeared to be the attackers’ “favorite” with 44.75% of all attacks. After injection vulnerability, path traversal and local file include (LFI) attacks were the attackers’ second “favorite” with 24.83%.
Social media, in fact, echoed this finding with 75% of the top 20 most viral tweets being related to the leading attack category, injection and remote code execution. Researchers observed a high correlation between the chatter in social media and actual attacks. Analyzing tweets from Twitter, the two most trending vulnerabilities on social media belonged to CVE-2020-5902 and CVE-2020-3452 which were also the top vulnerabilities used by hackers in 2020.
Imperva researchers continued to see a constant growth of vulnerabilities in APIs (Application Programming Interfaces) in 2020, with WordPress the most popular platform in the content management system category. In the server side technologies category, the report indicates an increase in the number of vulnerabilities in applications or packages written in JavaScript for NodeJS.
The report also shows MySQL to be ahead of all other popular databases in terms of new vulnerabilities discovered in 2020, although 92.4% of these had an unknown exploit. This is likely because Oracle acquired MySQL and doesn’t usually share technical details in its security reports. Additional analysis of bug bounty vulnerabilities revealed that almost 40% of them were ranked as Critical.
Vulnerabilities and cyber security attacks forecast for 2021
Given the degree to which APIs have become a necessary element for applications, Imperva researchers expect to see constant growth in the number of API vulnerabilities, although the rate of this growth is likely to decrease in 2021. The release of the OWASP API Security – Top 10 which standardizes the main threats in APIs will increase the awareness of security among developers and play a role in decreasing vulnerabilities.
Old faithful injection and XSS vulnerabilities will remain a serious concern, despite greater awareness and the number of tools that check code for their presence. The reason for this is the direct impact of the exploitation of these vulnerabilities, as well as – in most cases – the lack of preconditions required to exploit them. Injection vulnerabilities may also lead to supply chain attacks resulting in PII data theft.
The number of vulnerabilities in third-parties will continue to grow, as major platforms and frameworks become more reliant on third-party plugins. These vulnerabilities may be the gateway to various supply chain attacks. WordPress has over 58,000 plugins, the NPM registry has almost 1.5 million packages for NodeJS, and PyPI has over 280,000 packages for Python. In addition, there are also main package registries for Java and Ruby-based projects. As the community continues to grow, and without code standards or restrictions to publish a plugin or a package, they remain the weakest point in an application, making them the sweet spot for attackers.
Download the full report here.
Protect your apps from attack with a Web Application Firewall (WAF)
One of the best solutions for protecting against web application database vulnerabilities is to deploy a Web Application Firewall (WAF) and Data Monitoring & Protection. The solution may be either on-premise, in the cloud, or a combination of both depending on your needs, infrastructure, and more. Start a free trial today.
Try Imperva for Free
Protect your business for 30 days on Imperva.












