Key Takeaways:
- The gaming industry is a common target for cyberattacks due to its financial success and vast user base.
- Volumetric DDoS attacks can disrupt service, distract from more serious attacks, and cause financial damage, especially on sites that offer online multiplayer games or real-time sports betting.
- Attackers target web applications and APIs for various motivations, including stealing user data, gaining unauthorized access to gaming systems, or disrupting services.
- Gaming sites suffer cross-site scripting (XSS) at twice the rate of all other industries.
- In 2022, 28% of all API traffic in the gaming industry went to shadow APIs.
- Account takeover (ATO) attacks were highest in the last year, notably during the holiday season.
Why is the Gaming Industry a Target for Attackers?
The gaming industry has grown exponentially in recent years, with millions of gamers worldwide enjoying a wide range of interactive experiences. However, this popularity has also made it a prime target for cybercriminals seeking to exploit its vulnerabilities.
The gaming industry is an attractive target for cybercriminals for several reasons.
- The industry generates billions of dollars in revenue, making it a lucrative target for financial gain.
- The vast user base of gamers provides a goldmine of personal information that can be exploited for identity theft and other malicious purposes.
- The high-profile nature of the industry makes it an appealing target for attackers seeking to make a statement or gain notoriety.
- Users want to modify their game with mods, cheat tools, or other third-party programs, which expands the attack surface.
- There’s intense competition in this industry, with some players earning substantial prize money when they win. This gives gamers an incentive to leverage attacks, like DDoS, to ensure they beat their competition.
Along with popular online games, the industry also includes gambling and online betting, which attackers can target as a way to rig bets or gain insider knowledge of bets or odds. Accounts on these sites often include banking information in order to receive payouts, which is valuable information for ATO or data theft.
The gambling industry also experiences politically and ethically motivated attacks. Gambling sites are frequently blocked, via volumetric DDoS or DNS poisoning, by hacktivists or potentially government-backed attackers in countries that have banned gambling, like China.
Beyond hacktivism and competition, the industry is also targeted by other common attacks like ransomware. In 2021, CD Projekt Red, which created the popular games “The Witcher” and “Cyberpunk”, suffered a ransomware attack that released internal data, including source code. This breach led to significant delays in releasing the projects, as well as financial ramifications for the company. The impact of releasing source code and internal data can cause a company to lose important intellectual property, and it can have serious security implications for popular games.
Gaming sites’ value and popularity makes them a common target for attackers. Read on to learn more about common attacks and what companies can do to defend their networks, applications, and data.
DDoS Attacks: Disrupting the Gaming Experience
Distributed Denial of Service (DDoS) attacks are a common threat to the gaming industry. These attacks involve overwhelming a target’s network or servers with a flood of traffic. The target is unable to handle legitimate requests and this leads to disruptions in service. Attackers may target gaming networks with DDoS attacks for financial gain, revenge, or simply to cause chaos and disrupt the users’ gaming experience. The industry relies on a stable internet to play multiplayer games and load high-quality content, so any disruption to the network can have serious consequences.
For sports betting, reliable internet connections are crucial for placing bets on time. Sports betting sites were targeted more frequently during the 2022 World Cup last December and during the Indian Premier League cricket tournament in February 2023, as seen in the chart below. On top of disrupting operations, DDoS attacks can also function as a smokescreen to distract from other, more serious attacks.
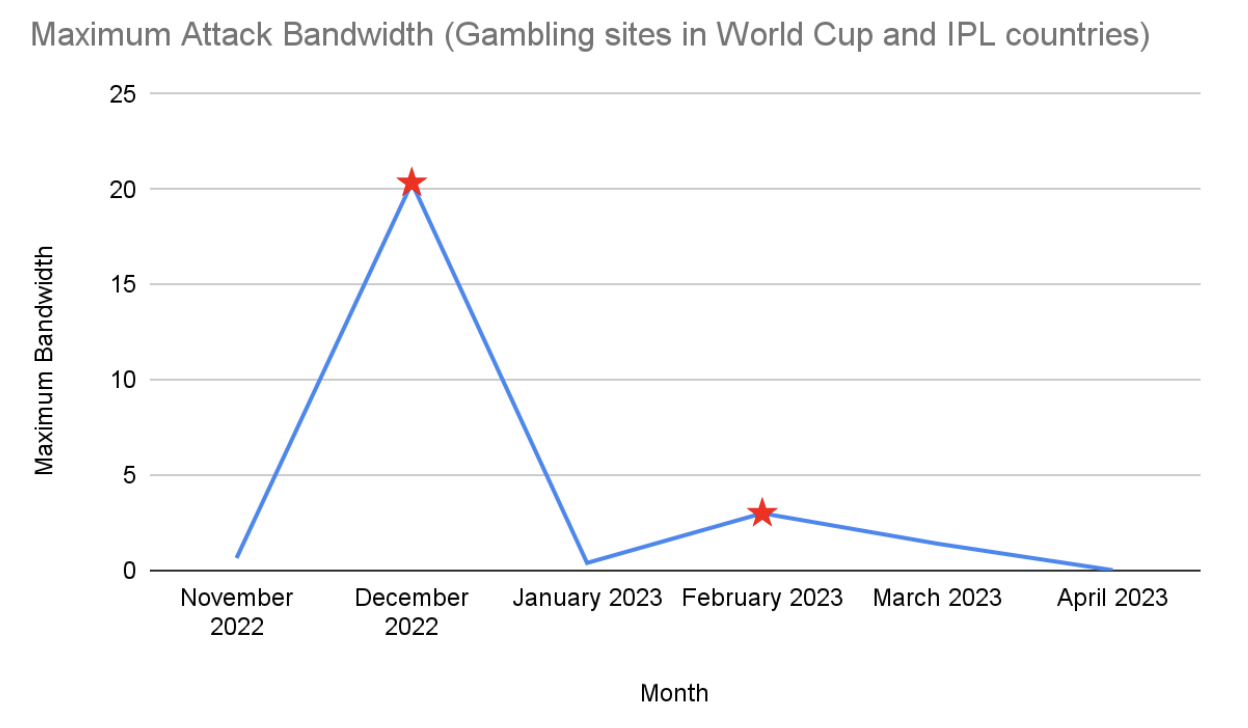
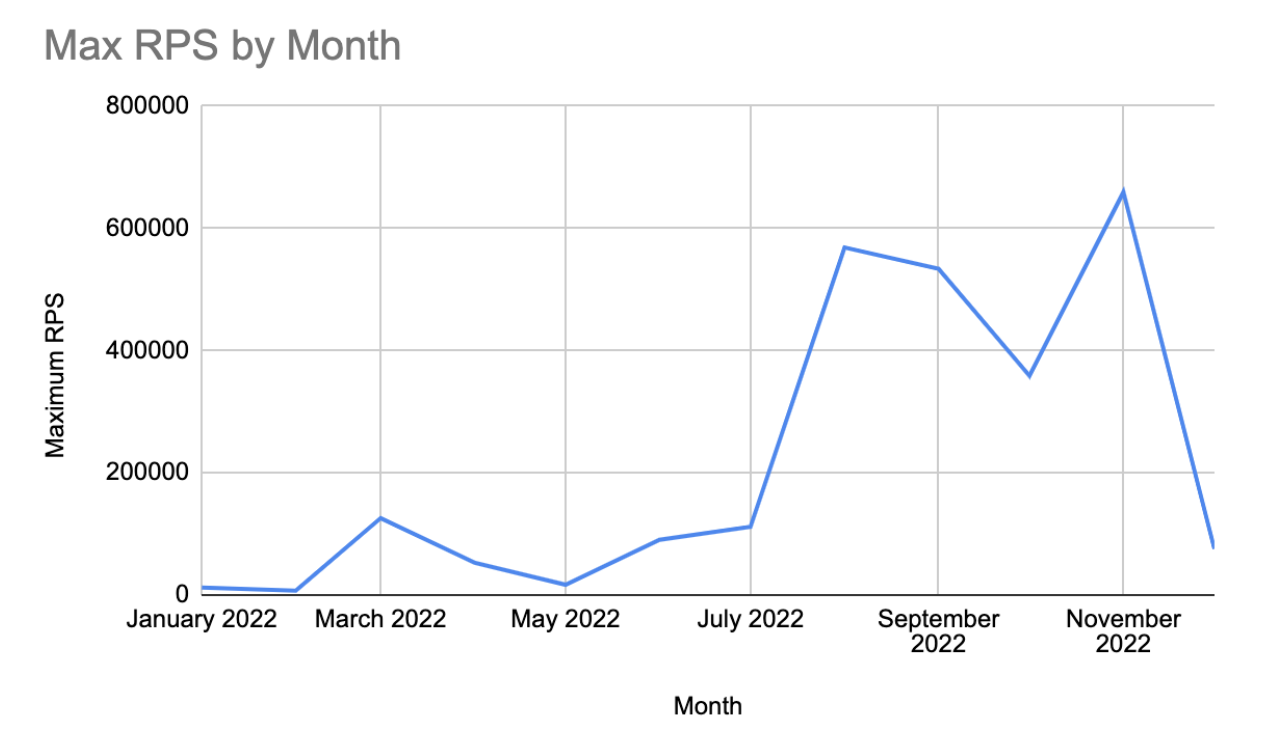
In 2022, application DDoS attacks on gaming sites protected by Imperva were considerably higher in the second half of the year. The volume of DDoS attacks frequently increases during the holiday season — when people have more free time to play games and when popular games are often released.
In 2020, popular gaming company Ubisoft won a lawsuit against a group of attackers who sold software to conduct DDoS attacks on servers running “Rainbow Six Siege” games in order to disrupt matches and attempt to gain advantages. Players frequently leveraged this DDoS software to avoid losing games and ruining online rankings.
These services, known as DDoS-for-hire, booter, or stresser services, are common in the gaming industry. These services allow anyone to rent DDoS attack capabilities in a user-friendly format, and allows people without technical capabilities to conduct attacks on gaming servers. This allows the user to gain an easy victory by disrupting the game or forcing the opposing player to disconnect. Attacks like this can also be done in retaliation for perceived cheating or other slights.
Network DDoS attacks were more consistent throughout the year. This type of DDoS is frequently used in DDoS-for-hire attacks, making them a common threat in the gaming industry. Attackers may also choose network DDoS in an attempt to cause maximum outages, as opposed to application DDoS that can be targeted against a specific game functionality.
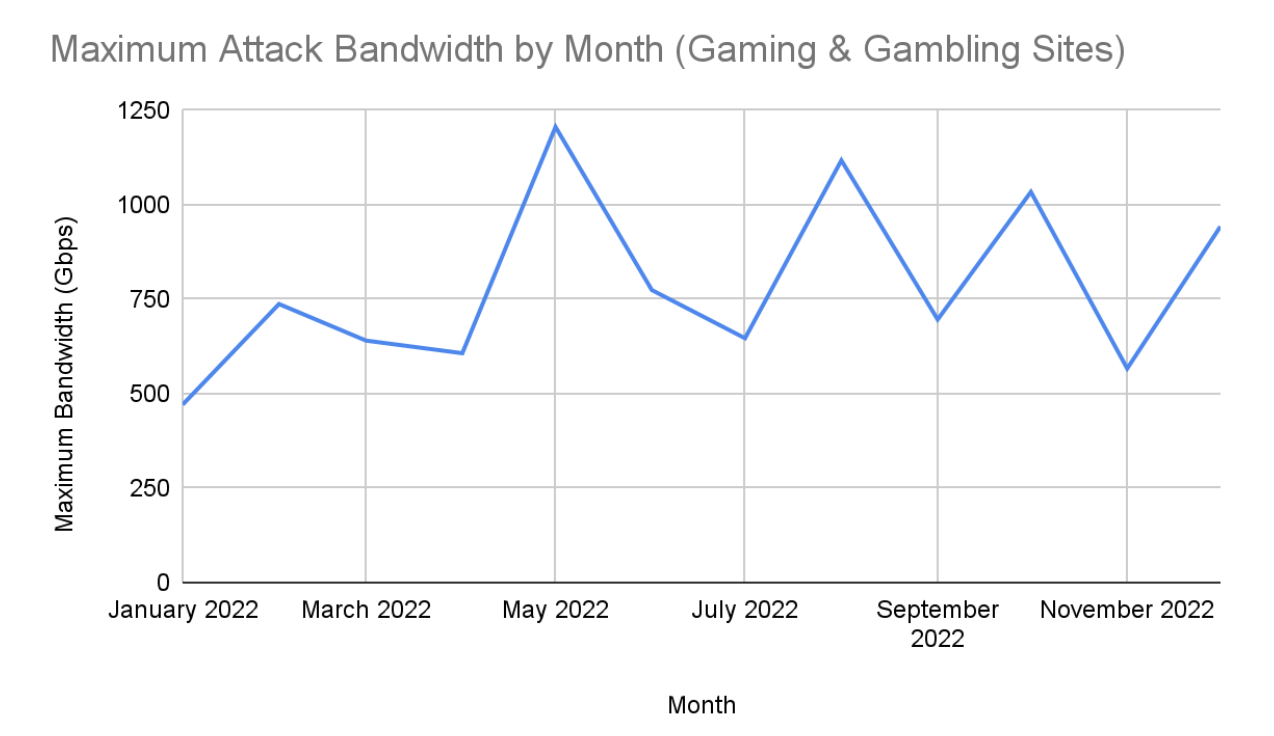
Securing the Gaming Industry: Web Application and API Protection
Web applications and APIs are integral to the gaming industry, powering everything from online multiplayer experiences to in-game purchases. However, these technologies introduce vulnerabilities that attackers can exploit.
Attackers target the gaming industry with various motivations: stealing user data, gaining unauthorized access to gaming systems, or disrupting services. Web applications and API security is crucial for ensuring the security of the gaming industry and safeguarding user data.
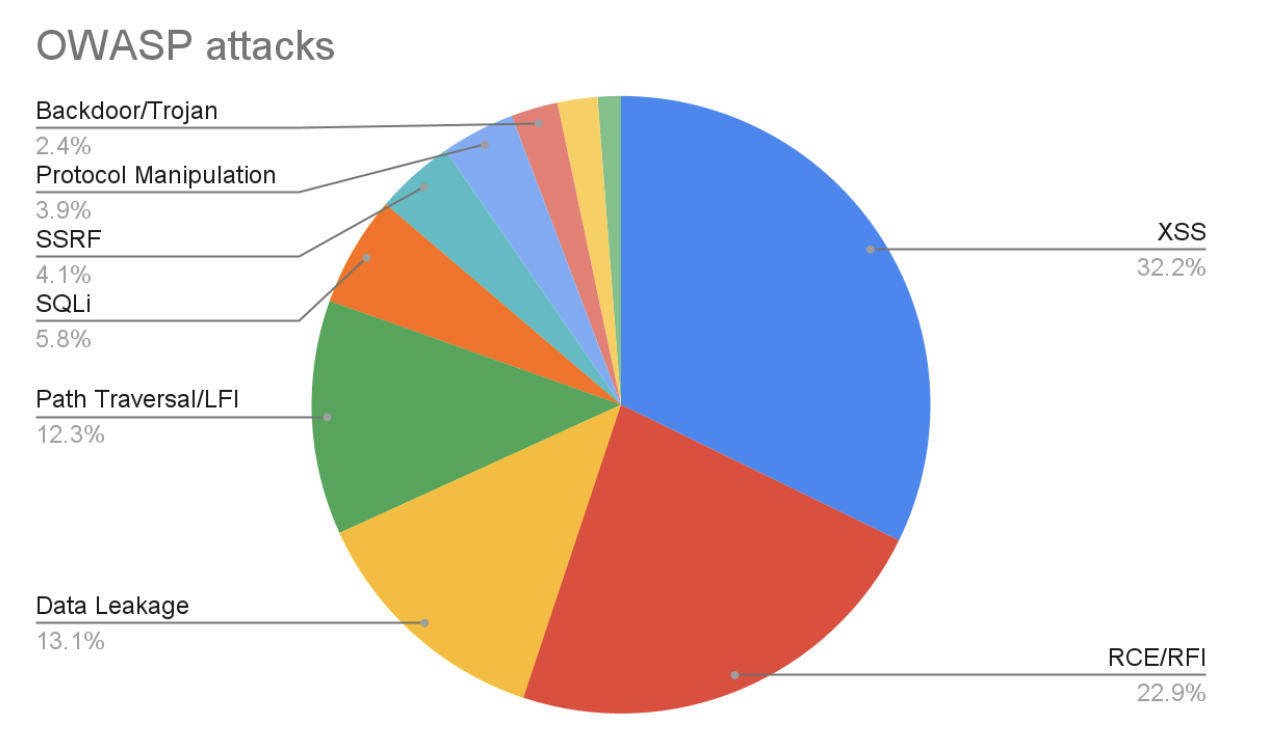
In 2022, the most common attack on the gaming industry was cross-site scripting at 32.2%. It made up a majority of all attacks because of a targeted attack on a popular online role-playing game in June 2022. XSS can be a common threat in the gaming industry because of the prevalence of user-generated content, which gives attackers the opportunity to input malicious scripts.
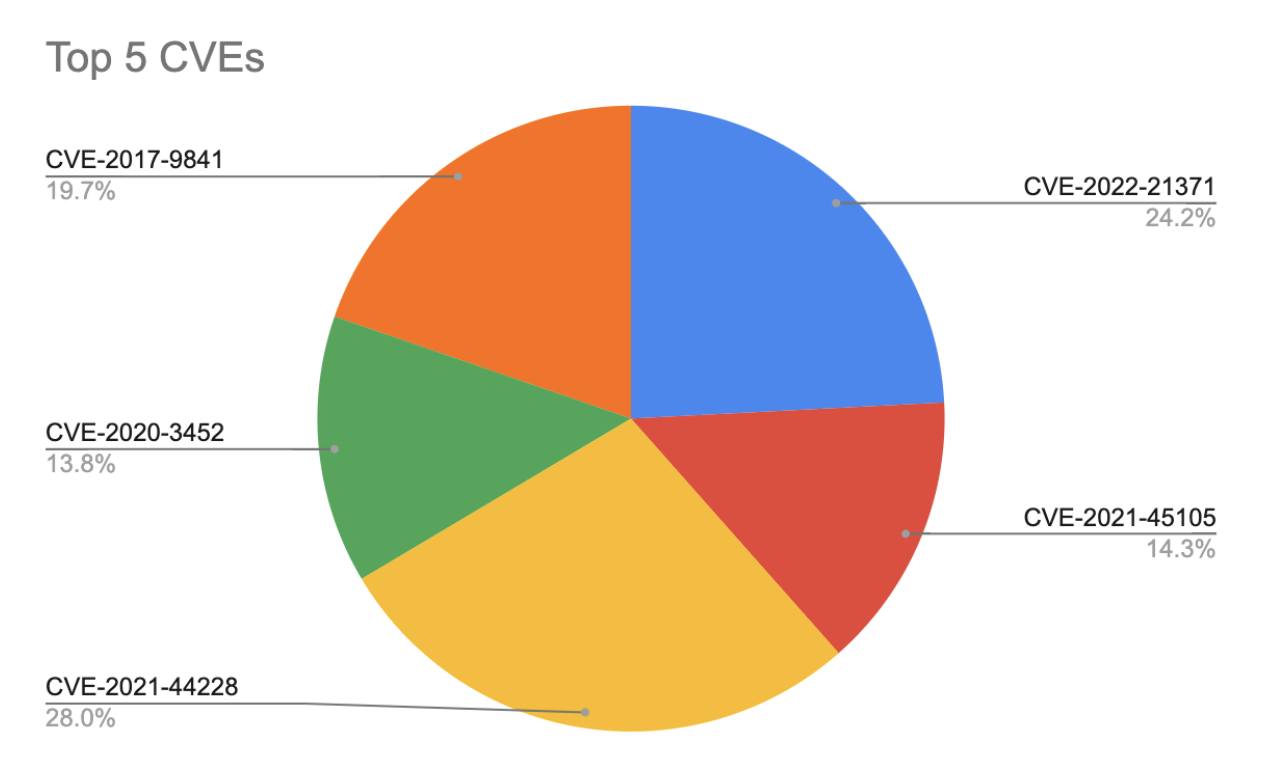
Last year, the top CVEs were primarily remote code execution vulnerabilities, like Log4Shell (CVE-2021-45105 and CVE-2021-44228) and Oracle and ThinkPad bugs. These vulnerabilities could allow attackers to gain control over gaming servers, steal data, and run cheat code, giving them an advantage during gameplay. Other zero-day vulnerabilities found in specific games could be exploited to gain access to user data or manipulate gameplay.
Social engineering is also common in the gaming industry. The online communities, the virtual chat rooms, and messaging platforms that many players use are susceptible to social engineering attacks. The anonymity allows a hacker to impersonate game officials, or even gaming platforms, in an attempt to harvest credentials and other valuable information.
APIs, or protocols that allow programs to interact with each other, are another common attack vector. They’re vulnerable to threats like shadow APIs and business logic abuse. Shadow APIs, or APIs that are undocumented and not maintained by normal IT management and security processes, but not removed, present a threat to gaming sites. In 2022, 28% of all API traffic in gaming went to API endpoints flagged as a shadow API. These forgotten and unmaintained APIs offer attackers a pathway to the rest of the network, which can have devastating consequences. Gaming companies can be more vulnerable to API threats because they often deal with sensitive data, such as user credentials and financial information. Additionally, gaming companies are more likely to use APIs to provide game services, making APIs an attractive target for attackers.
Another common attack on APIs is business logic abuse. At 65% of all API attacks, business logic is a massive threat to gaming and gambling sites in an attempt to exploit flaws in the logic of an application. These attacks may target the mechanics of online games, payment portals, user interactions, or other ways to compromise gaming and online gambling operations.
The Impact of Bad Bots and Automated Attacks on Gaming
Bad bots are automated software programs designed to perform malicious tasks, such as scraping data, launching DDoS attacks, or exploiting vulnerabilities in web applications and APIs. Bots can wreak havoc on the gaming industry by stealing user data, disrupting services, and manipulating in-game economies. Attackers use bad bots to target the gaming industry for financial gain, competitive advantage, or simply to cause chaos.
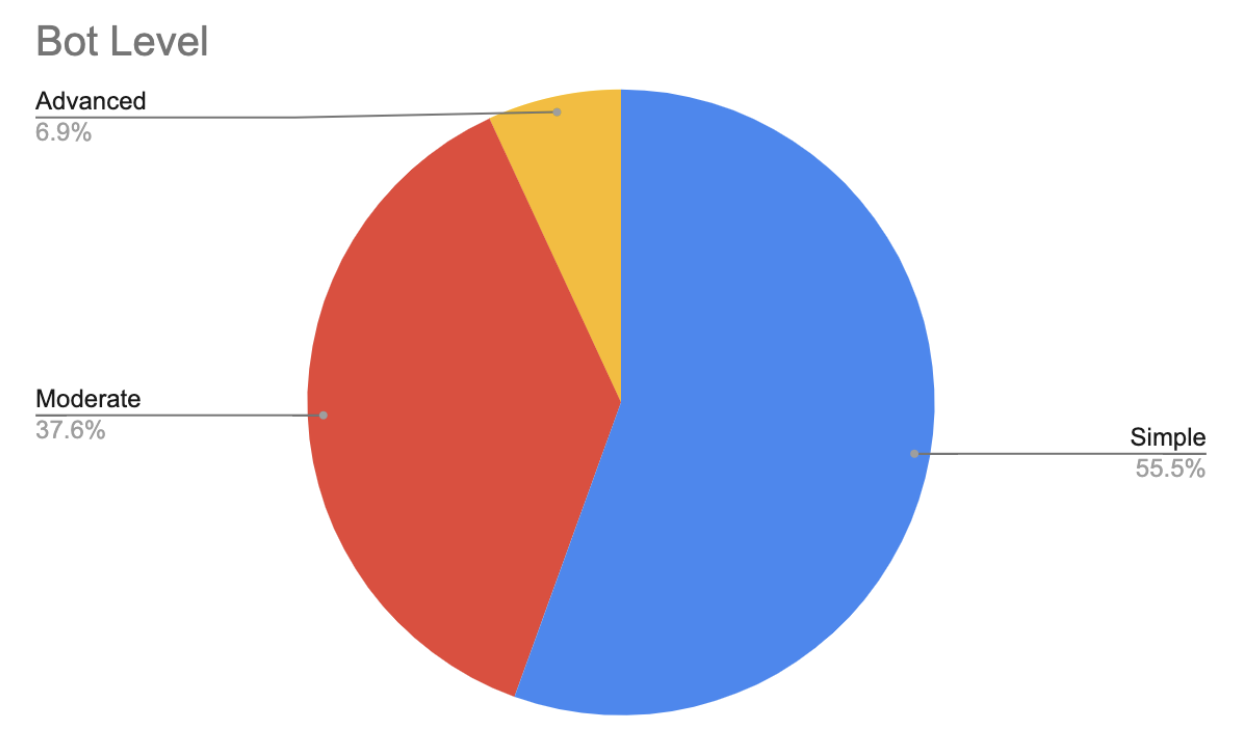
The 2023 Imperva Bad Bot Report classifies bots at three levels: simple, moderate, and advanced. Simple bots connect to sites using automated scripts and don’t self-report as a browser, while moderate bots simulate browser technology and advanced bots emulate human behavior.
The majority of bot attacks in 2022 came from simple bots, at 55%. Common gaming attacks like spamming, DDoS, or in-game currency farming can be written fairly simply and require less sophistication than more in-depth attacks. This is why simple bots like GnBots or LSS Bot, which can be purchased easily online, are prevalent. Moderate bots, at 7%, are seen in higher proportions on betting sites because those sites require more specialized attacks.
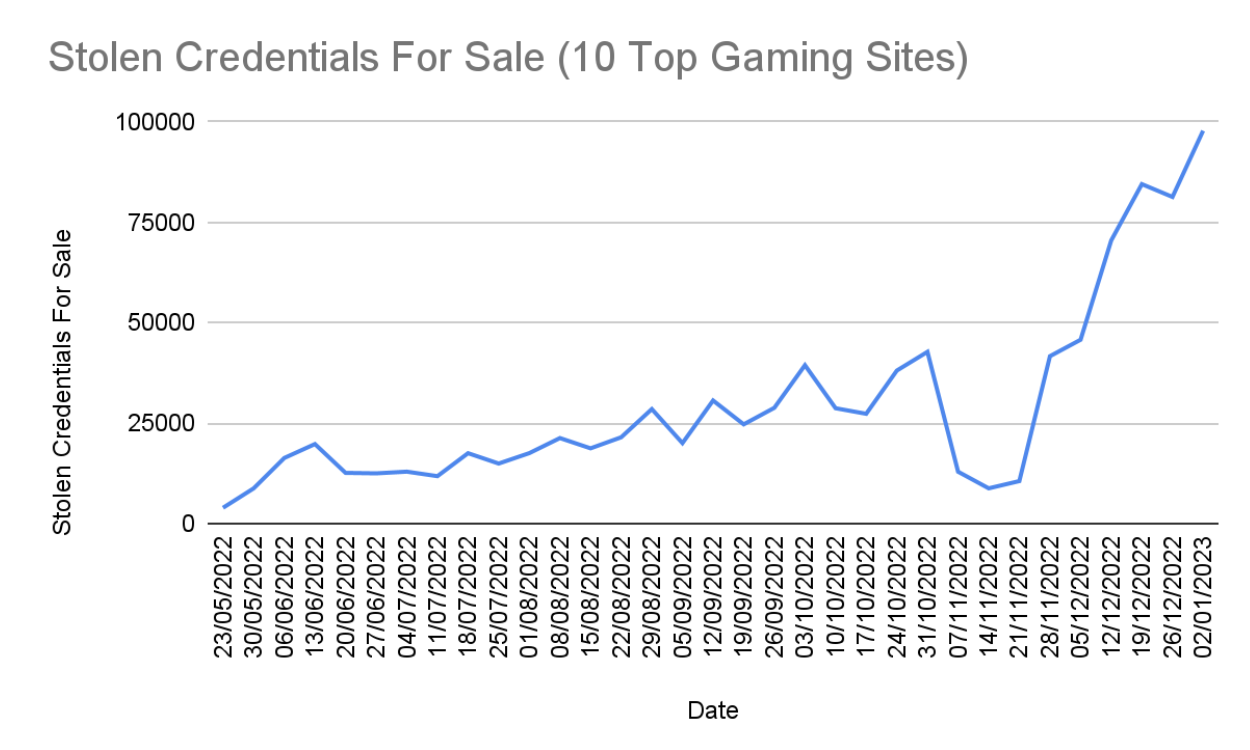
Account takeover is another common bot attack that leverages stolen credentials to access accounts with the intention of compromising valuable information. ATO is common in the gaming industry because many black market sites translate stolen gaming accounts, virtual items, or in-game currency into real-world currency. Additionally, gaming sites often have lower security measures than something like highly regulated online banking accounts, giving attackers a lower barrier to entry. As illustrated below, the volume of gaming credentials for sale on hacker forums increased steadily in the last year, particularly during the holiday season.
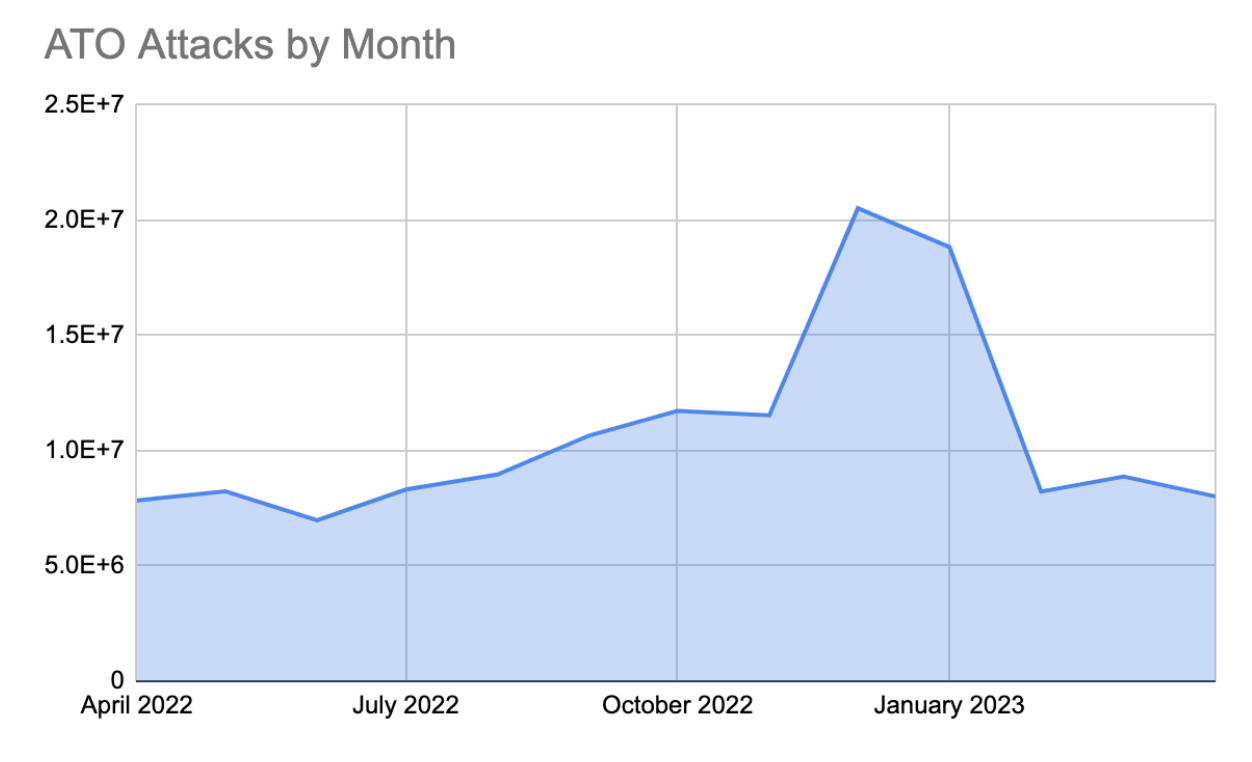
ATO attacks peaked over the holiday season, likely due to both increased online activity and high demand for gaming-related products for gifts.
Conclusion:
The gaming industry’s financial success and vast user base make it a prime target for cybercriminals. They use a variety of attack methods, including DDoS, web application and API attacks, and bad bots. By understanding the motivations and methods behind these attacks, the gaming companies can protect networks and ensure the security of the industry.
By staying vigilant and implementing robust cybersecurity measures, the gaming industry can continue to thrive and provide enjoyable experiences for gamers worldwide.
Learn why organizations around the world trust Imperva to protect their critical apps, APIs, and aata, anywhere.
Try Imperva for Free
Protect your business for 30 days on Imperva.











