On April 25, 2023, researchers at Bitsight and Curesec jointly discovered a high-severity vulnerability — tracked as CVE-2023-29552 — in the Service Location Protocol (SLP), a legacy Internet protocol.
What is SLP protocol?
Service Location Protocol (SLP) is a network protocol designed to simplify the process of discovering and accessing network services. Developed by the Internet Engineering Task Force (IETF) and defined in RFC 2608, SLP eliminates the need for users or administrators to manually configure clients with the addresses of available network services. Instead, it allows devices and applications to automatically find and connect to services in their local area networks (LANs). Since the SLP protocol doesn’t require authentication, anyone can register new services, which is why it wasn’t intended to be publicly available over the Internet.
How Does SLP Work?
SLP operates based on a request-response model that involves three primary components: User Agents (UAs), Service Agents (SAs), and Directory Agents (DAs).
- User Agents (UAs): UAs are clients seeking network services. They send out service requests to discover the available services in the network.
- Service Agents (SAs): SAs represent the network services themselves. They advertise the services they offer and respond to service requests from UAs.
- Directory Agents (DAs): DAs act as a centralized repository for service information. They cache the advertisements from SAs, and UAs can query them to find the desired services more efficiently. Although DAs are optional, their presence improves the overall performance of the SLP system.
Understanding How CVE-2023-29552 Works
The attack technique allows an unauthenticated, remote attacker to register arbitrary services. This would enable the attacker to use spoofed UDP traffic to conduct a denial-of-service attack with a significant amplification factor.
The researchers uncovered a novel technique in which attackers can register new bogus services until the SLP servers are overwhelmed and deny more entries.
Attackers can then send requests to the SLP server to list its services, forging the source IP as the victim’s IP. The vulnerable SLP servers then send the SLP reply packets which contain the list of bogus services. This results in a massive DDoS amplification attack that could potentially reach an amplification magnitude of up to 2,200X.
Below a list of the top countries with SLP instances that are exposed to the internet:
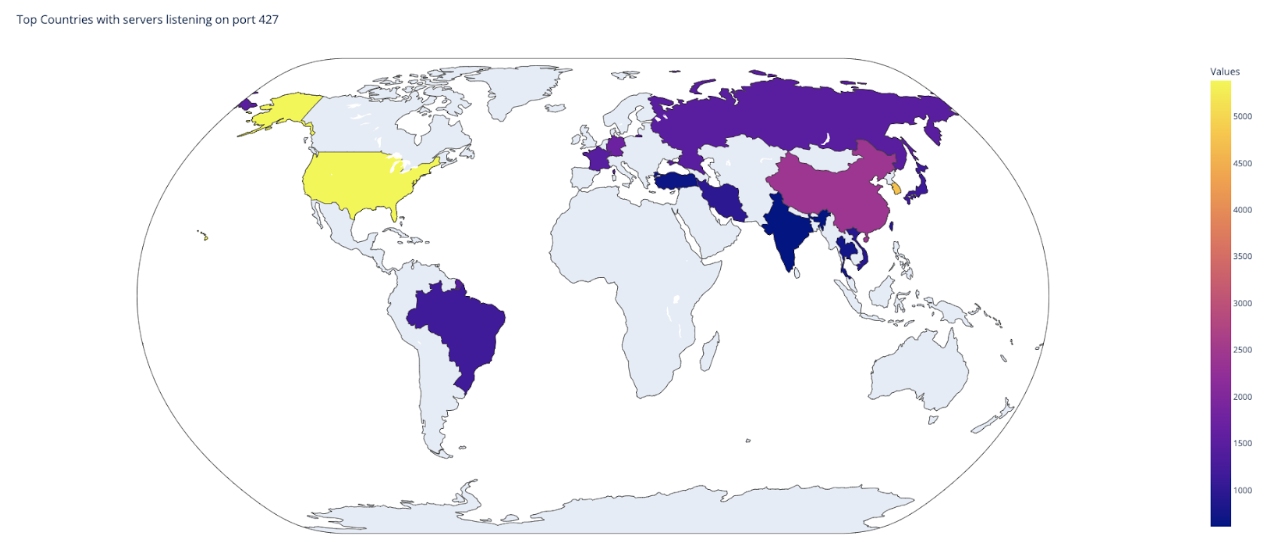
Assuming each reply packet from one exposed SLP server could be up to 64,000 bytes long, or higher, an attacker would need to send a server listing request simultaneously to 2,000 SLP servers. That’s less than 10% of all publicly exposed SLP servers. This would enable the attacker to overwhelm any IP with a whopping 1Gbps of malicious traffic that consists of the replies from the SLP servers.
In theory, SLP servers are capable of replying to multiple requests simultaneously. It is estimated that there are 33,000 exposed servers on the internet; therefore, this attack technique could be quite massive.
In the video below, we show how this attack is carried out using an open source tool written by one of the researchers who discovered this CVE.
It’s important to note that the number of publicly accessible servers using the SLP protocol are declining. Over the past few days, Imperva Threat Research has not observed an increase in exploitation attempts against customers using Imperva DDoS Protection for Networks.
The Imperva Threat Research team made sure customers are protected from this attack method when using Imperva DDoS Protection for Networks.
As always, Imperva Threat Research is monitoring the situation and will provide updates as new information emerges.
Try Imperva for Free
Protect your business for 30 days on Imperva.










