While Christmas is often seen by most as a joyous time to be spent with family and friends, exchanging good wishes and gifts, there are those who seek to exploit it. For fraudsters, this time of the year is above all, an opportunity for profits to be made, all while wreaking havoc on eCommerce applications.
According to the Imperva State of Security Within eCommerce Report, over the past 12 months, nearly 40% of traffic on retailers’ websites wasn’t human. Instead, it was automated traffic, commonly referred to as bots – software applications controlled by operators that run automated tasks, often with malicious intent. Account takeover, credit card fraud, web scraping, API abuse, scalping, and distributed denial of service (DDoS) are just a few of the nefarious acts these bots are responsible for.
The Imperva Threat Research Team is constantly on the lookout for new trends and techniques used by bad actors to improve their efficiency. In this blog, we will uncover some of those, focusing on Skewing and Scalping bots.
Skewing bots
One of the threats we see growing is Skewing bots. Skewing bots are automated software whose purpose is to disrupt application telemetry to serve the fraudster’s interests. In a skewing attack, attackers falsify (or skew) data, causing an organization to make the wrong decision in the attacker’s favor. There are two common variants of skewing attacks:
- Machine learning data poisoning attacks: Attackers modify the training data used by a machine learning algorithm, causing it to make a wrong decision.
- Web analytics skewing: Attackers modify analytics data from platforms like Google Analytics or Adobe Analytics, by performing a large number of automated queries using bots. The objective is to make it appear that web visitors perform certain actions more often than they really do.
To illustrate this trend, let’s review an example of data skewing.
The chart below shows the evolution of activity for a popular eCommerce Skewer bot, available on a fraudster Discord channel targeting the eBay marketplace. The purpose of this bot is to simulate fake views on specific eCommerce products and indirectly increase the visibility of the fraudster’s items.

First, this chart shows the bot’s consistent increase in activity over the last year. It also illustrates a spike in activity over the last few months, coinciding with the holiday shopping season.
A drill down into this data shows that resell fraudsters are focused on clothes (e.g., Adidas, Nike, Supreme, Eric Emanuel, Vuitton, Gucci, Puma, J.Crew, Nixon…) and collectible items (e.g., Baseball cards, Vinyl albums, Comics…).

To safeguard your business from this threat, refer to the recommendations outlined in the Recommendations section below.
Scalping bots
Scalping bots, also known as Grinch bots, are another very common threat this time of the year. Scalping bots are software that automates the purchase of sought after products, making them inaccessible for real users who don’t use automation. Those bots are progressively shifting from the sneaker market where they are omnipresent to other types of markets (e.g., NFTs, consoles, hardware…). They are also evolving towards Lowkey Flips to make a difference.
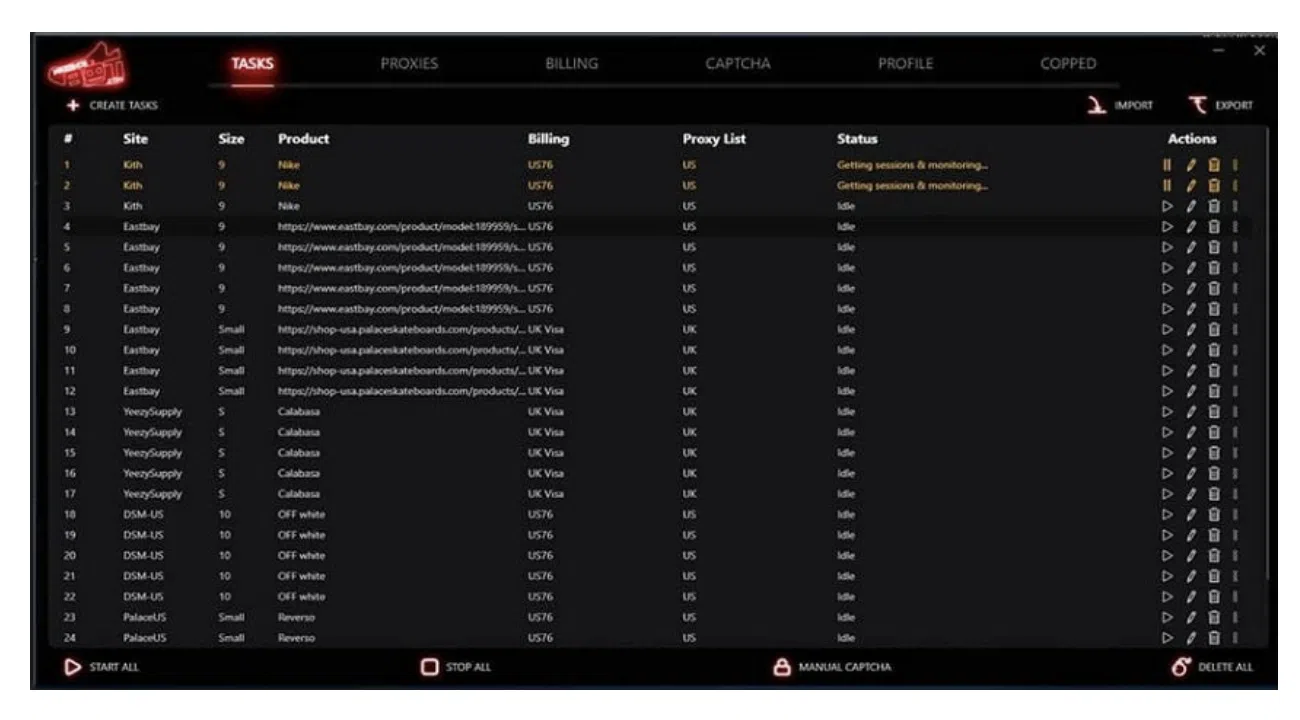
Main dashboard of NSB (advanced scalping bot)
Since eCommerce applications are progressively investing in their anti-bot defenses, fraudsters are therefore improving their techniques:
- They’re looking for more efficient proxies, combining excellent reputation and good time performance despite their high price.

- They’re investing in good reputation Google accounts to beat Google CAPTCHA at its own game.

This offer from a Gmail account provider guaranties a smooth bot experience against applications. The reason for that is their use of aged, warmed Gmail accounts. Aged, because old accounts are more trusted by the Google anti-bot solution. Warmed, because the provider controls the account(s) and makes it perform human-like actions like watching videos, interacting with social media websites, etc.
Still, there are a few tricks used by fraudsters that can be monitored to detect and mitigate scalping attempts:
- Jigging: The action of slightly transforming a textual input (Address, name …) in order to bypass fraud detection and allow a massive amount of checkout requests.
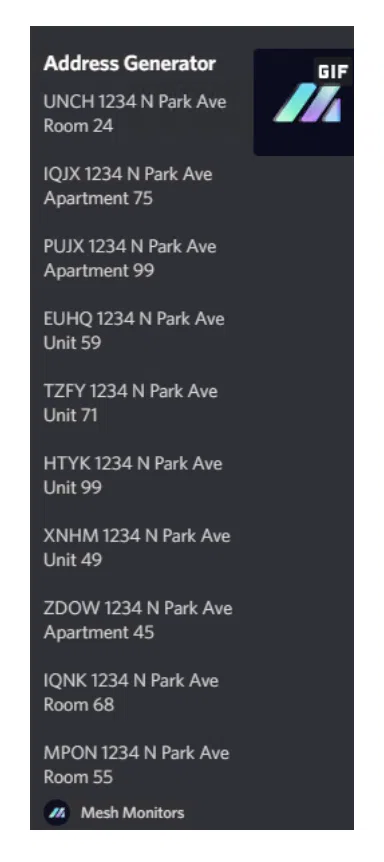
Multiple addresses generated from “1234 N Park Ave”
- Dot trick: A `.` in a Gmail address is completely transparent. Therefore, any email sent to abc@gmail.com is also sent to a.bc@gmail.com and ab.c@gmail.com. Attackers can then leverage this feature and create multiple accounts or checkout operations using the same email address and bypass scalping detection.
Recommendations
In general, there are a few steps to counter these types of attacks:
- Block outdated browsers or user agents
- Block known bad hosts and proxies
- Shield access points vulnerable to bots
- Evaluate traffic sources
- Investigate spikes in usage
- Detect deviations from the normal application behavior
- Invest in an efficient anti-bot solution
For more information, read these articles about scalping bots and data skewing.
Conclusion
These are just a few of the bad bots that target online retailers daily, causing chaos and impacting the bottom line. One thing is clear: bots are here to stay.
It’s best to be prepared, and to stay one step ahead with your website security. Imperva Threat Research is constantly evaluating new bots and their operations to enhance the market-leading Imperva Advanced Bot Protection and to mitigate the most sophisticated automated threats, including all OWASP automated threats. It leverages superior technology to protect all potential access points, including websites, mobile applications, and APIs. It does so without affecting the experience of legitimate users.
Try Imperva for Free
Protect your business for 30 days on Imperva.











