Since debuting Attack Analytics back in 2018, this groundbreaking security analytics functionality has come a long way. Time and again our customers have told us how powerful they find the tool and how much time it saves them. Attack Analytics better positions Imperva’s customers to focus on what’s most important first while making no small feat of reducing application risk easier. And the great news is it just keeps getting better.
Baseline Functionality
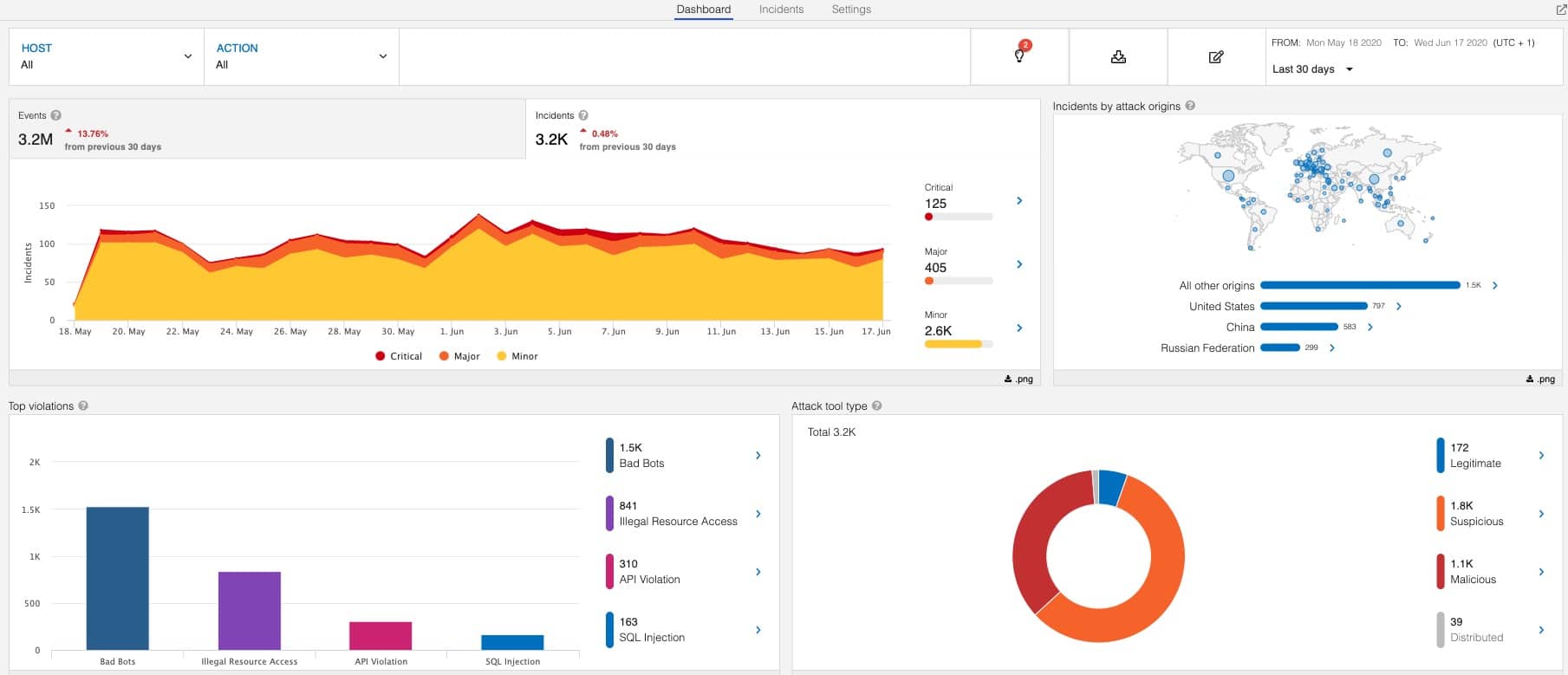
To level set, Attack Analytics is a machine learning and domain expertise-based system, which smartly clusters a huge amount of events into a manageable number of incidents.
For example, you could easily view events from the last 30 days and cluster, say, three million events, into a few thousand incidents, drastically reducing the amount of information to sift through and analyze. Incidents are then further classified by severity as critical, major, and minor, which leaves you with even less critical events that probably require your immediate attention.
Integration with Multiple Sensors
A huge area of investment we’ve had at Imperva over the past year has been integrating Attack Analytics with multiple sensors. In the beginning, Attack Analytics focused on collating security events filtered through our WAF Gateway and Cloud WAF solutions to deliver an integrated, accurate, actionable report of security incidents.
Now, essentially, Attack Analytics is able to provide you a single pane of glass, for an account-level attack landscape point of view. It’s able to analyze events and information from all Imperva sensors, giving you better visibility into your network to understand what happens in incidents from all types of threats.
Other integrations include services like account takeover protection within our Advanced Bot Protection, integration with API Security, DDoS Protection, and reputation intelligence.
Advanced Bot Protection – Account Takeover
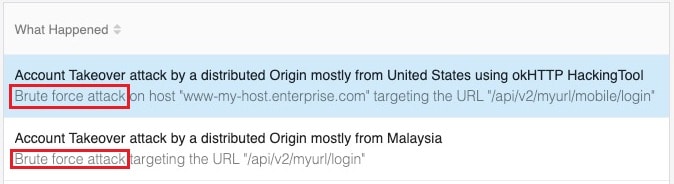
In the case of account takeover, an Attack Analytics incident description on the Attack Analytics dashboard clearly indicates the presence of an account takeover attack. The subtitle below further indicates the activity that caused the accounts to be marked as compromised, like brute force or credential stuffing:
Our best practice approach encourages you to start reviewing your triggered alerts first. The next step, based on this information, may be to review any incident details within your accounts that were under attack having been set to Alert mode instead of Blocking mode to ensure those accounts were not compromised, and, if so, readjust your security settings accordingly.
API Security
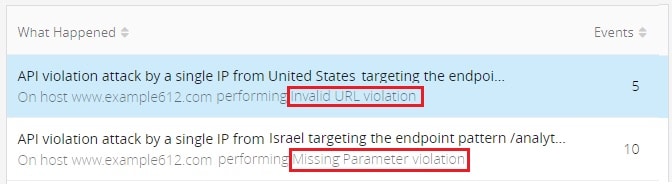
With Attack Analytics, incidents also list API violations with helpful details of the specific API Security violation type:
With this information, you can easily gain visibility into any security incidents that violate your uploaded API Swagger file. Ideally, you will have determined in advance which endpoints you’d block violations against versus alert; however, if you hadn’t earlier, now would be the time to make the necessary changes to ensure your APIs are secure going forward.
Learn more here.
DDoS Protection
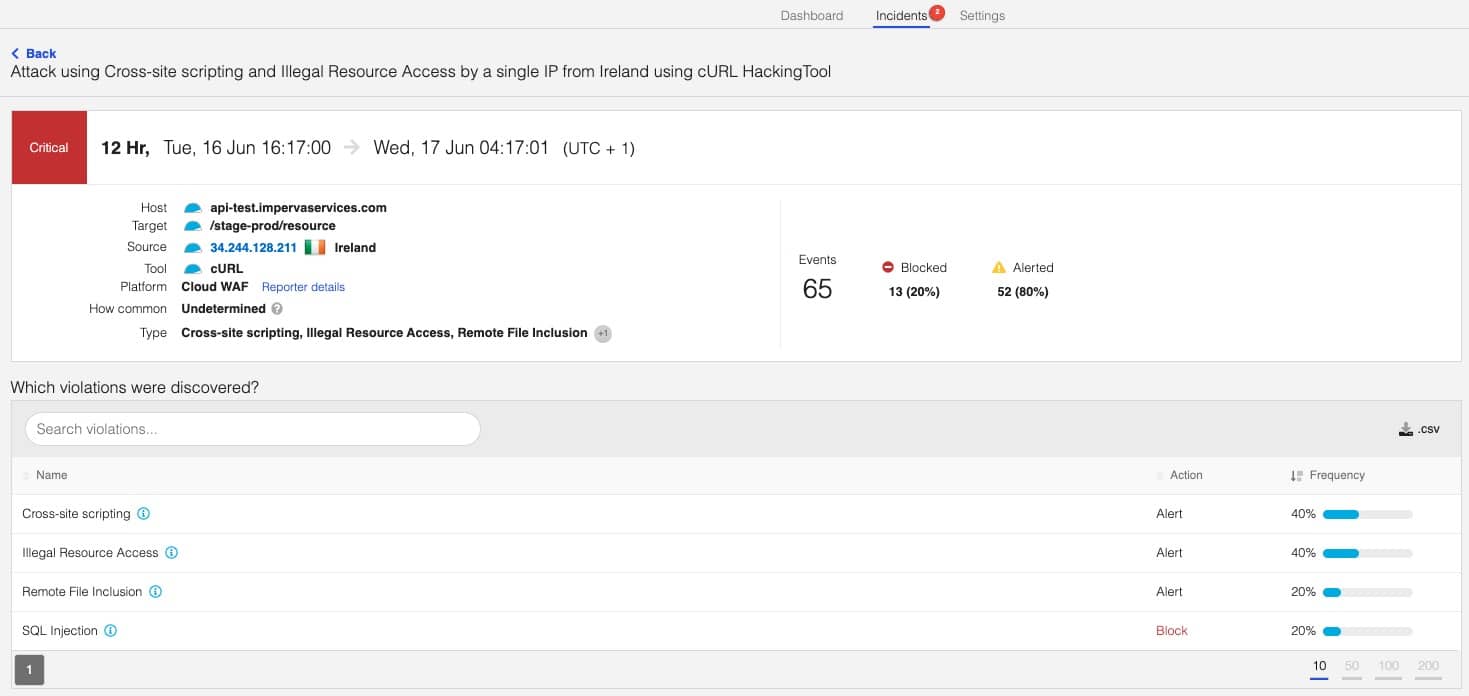
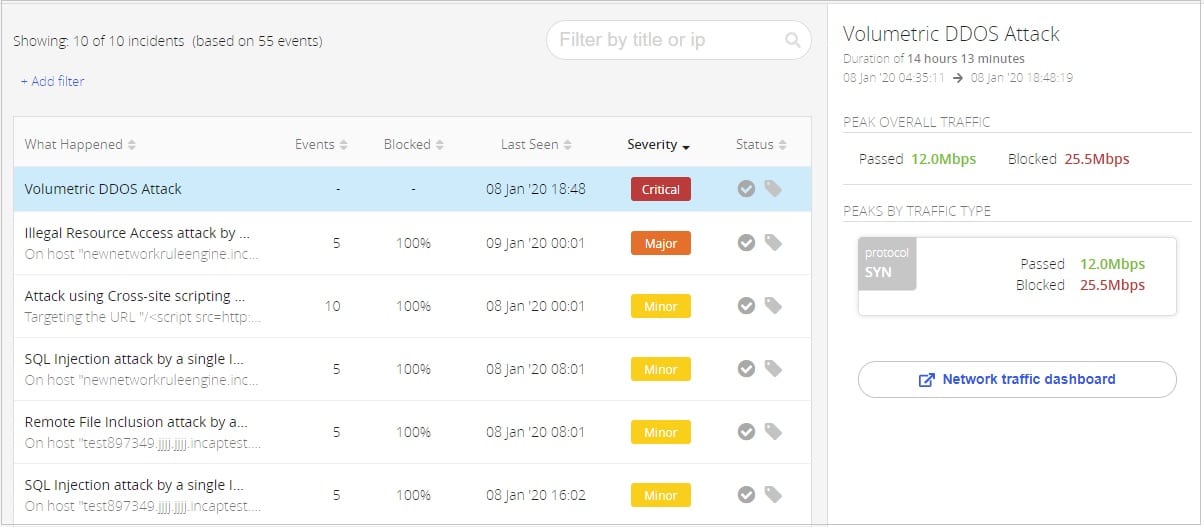
An example of the benefits of the DDoS integration with Attack Analytics is the indication of a volumetric DDoS attack, which many times is masking application layer attacks. Just by clicking on the attack, you can go to the area around the time of the attack, find the attack in the list and see what happened around, just before, during and after the attack.
Seeing other attacks fully blocked gives you a high level of confidence in your security standing alone, but you can also see the network level information of the volumetric DDoS attack itself, and even go directly to the network traffic dashboard to further investigate the attack.
Actionable Insights
A very important addition to Attack Analytics is what we call actionable insights. This is a system which analyzes your attack patterns and your configurations, finding potential issues and recommending optimizations that will help you improve your security posture. Check out this quick 60 second video to see Actionable Insights in the works
The idea behind it is to use machine learning to arm security teams with more information than ever before. If you’re used to doing a lot of manual work and having the burden of security fall solely on you, that’s absolutely not the case here.
Reputation Intelligence
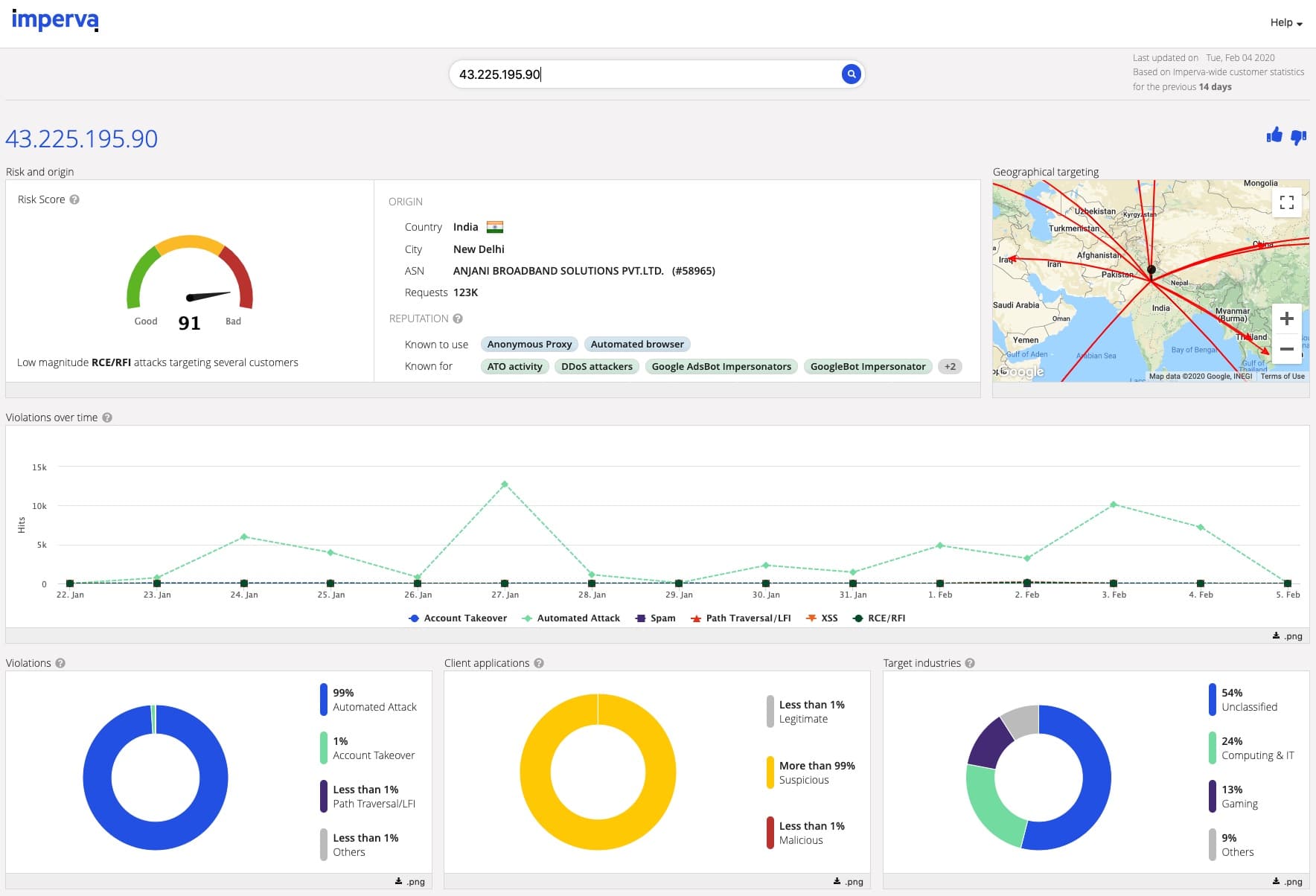
Our reputation intelligence service, also available outside of Attack Analytics, provides visibility into the information Imperva gathers on attacking entities from customers and third party vendors. It’s based on Imperva’s entire cloud community and the work of our in-house security experts at Imperva Research Labs, and gives you a calculated risk score for each IP as it goes through the system.
This score is based on the attacks it performed and how many customers it attacked, the tools that were used, and what it’s known for, the number of requests in the last two weeks, where it attacked from, the attack patterns over time, and more.
Bottom line: This information propels you toward making a more educated and informed decision, so you can feel confident you know what to do with it. And if you decide to act, you can easily go directly to the right setting page in the cloud system and resolve the issue immediately as highlighted in the Youtube video below.
Cloud Readiness and Digital Transformation
It’s important to note that this concept of distilling information from disparate sources is especially beneficial if you’re moving to the cloud and have applications which reside in multiple locations – on premises, in the cloud or in a hybrid environment. This would typically complicate security investigation of events originating from the different locations. Instead, we see Attack Analytics as helping to facilitate the cloud-readiness aspect of your digital transformation.
Understandably, limited personnel resources is an issue for many organizations and the maintenance and administration of multiple security systems and interfaces can consume a large portion of their budget. But by having integrated analytics as part of the glue which ties our breadth of application security solutions together, it greatly simplifies security management and gives a level of visibility that no other vendor can provide.
Going Forward
In future articles we’ll dive further into the specifics of Attack Analytics integrations with our Runtime Application Self-Protection (RASP), where you can have applications installed with RASP opt-in to send events to Attack Analytics.
We’ll also cover the benefits of integrations with other functionalities within our Advanced Bot Protection service, where Attack Analytics is used to create narratives to describe bot-specific use cases like carding, scraping, denial of inventory, ticket scalping and price aggregators.
Try Imperva for Free
Protect your business for 30 days on Imperva.